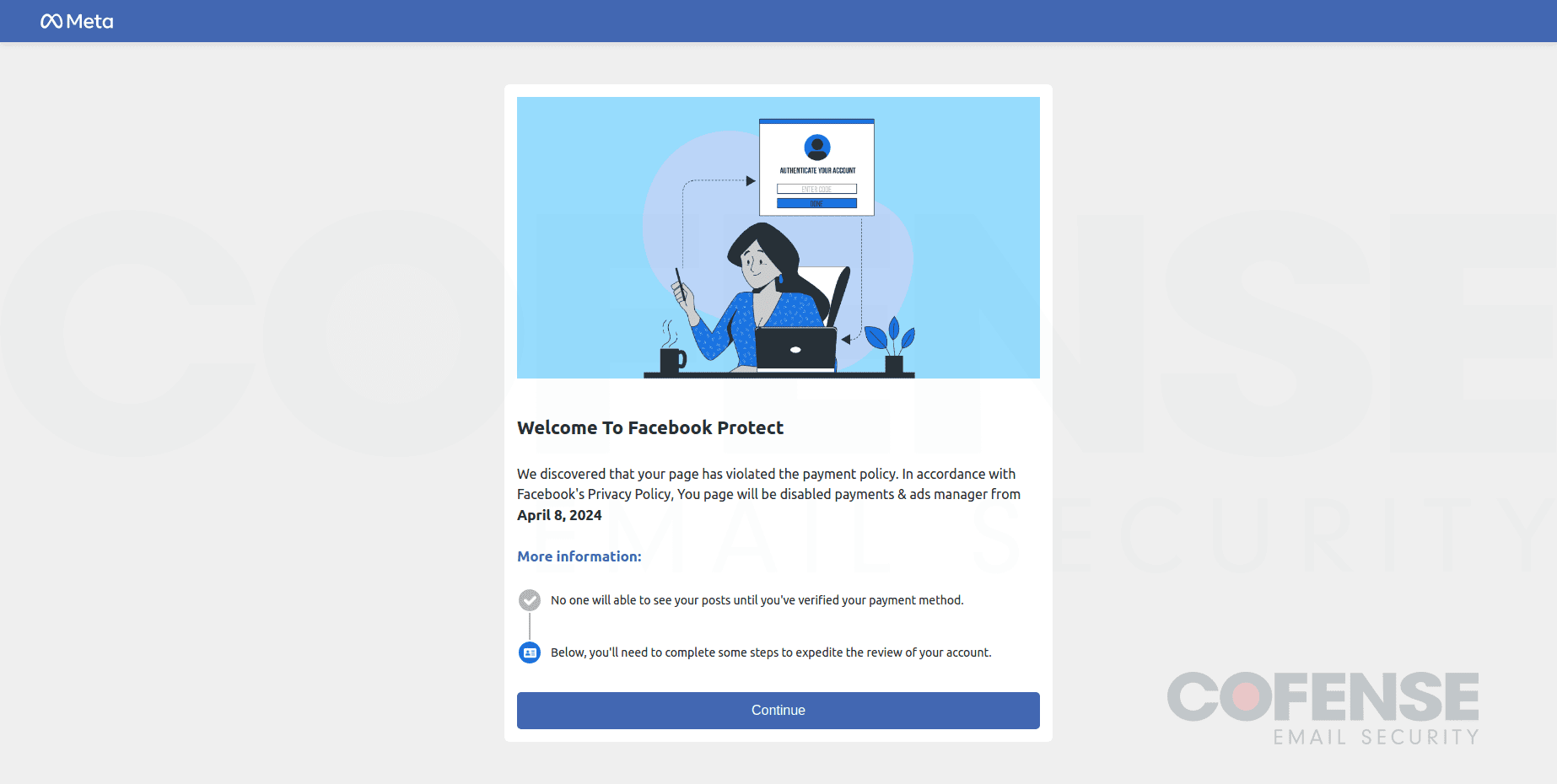
The landing page, the first page that users will see after interacting with the phishing URL.
Cybersecurity firm Cofense has exposed a sophisticated phishing campaign that is actively targeting Meta business accounts worldwide. This elaborate scheme, leveraging a comprehensive toolkit and advanced techniques, has been observed targeting users in 19 different countries, using meticulously crafted emails in various languages to lure victims into compromising their accounts.
The campaign’s success lies in its ability to bypass multi-factor authentication (MFA), a security measure designed to protect accounts from unauthorized access. By employing clever tactics, the threat actors behind this campaign have managed to deceive even the most vigilant users, harvesting login credentials and MFA codes through a series of convincing phishing pages.
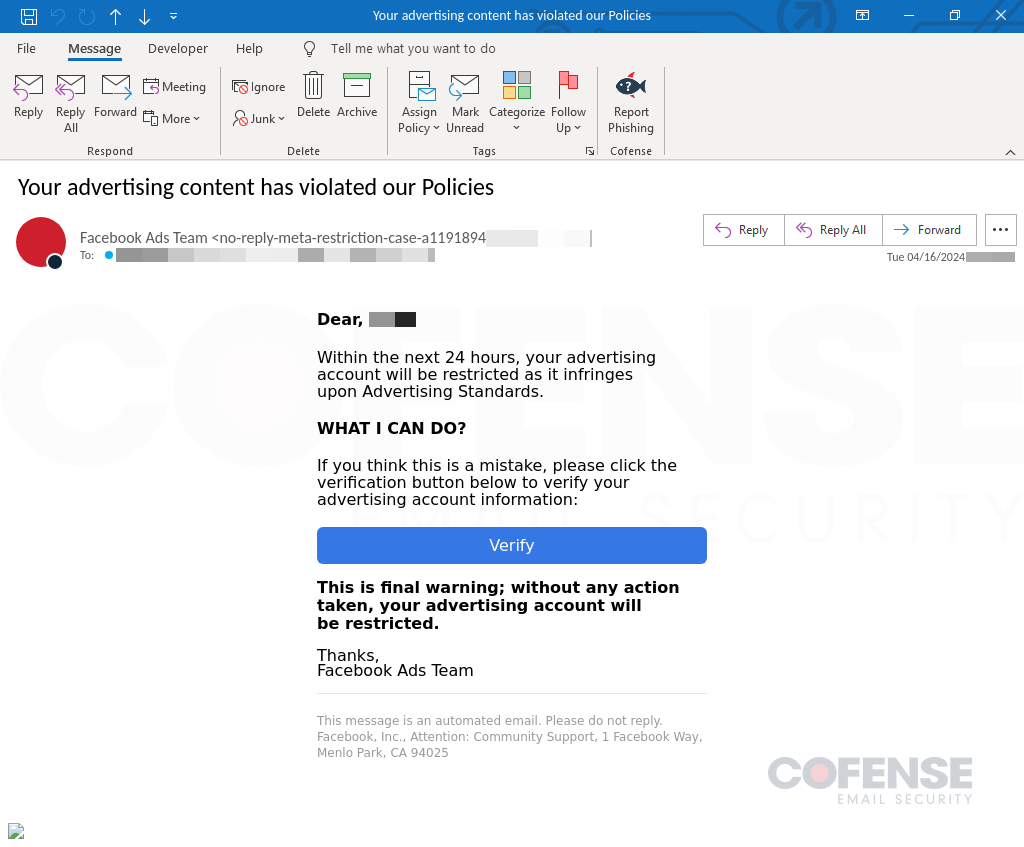
The campaign, characterized by its high level of sophistication, uses emails that cleverly impersonate Meta, particularly targeting the Facebook Ads Team. These emails often allege policy violations or copyright infringements to trick business account managers into clicking malicious links. The emails are crafted to appear legitimate, with some even bypassing secure email gateways (SEGs) to reach user inboxes in enterprise environments.
The attack follows a multi-step process designed to extract as much sensitive information as possible:

- Initial Contact: Victims receive an email containing a link, which directs them to a phishing site hosted on platforms like Netlify[.]app or Vercel[.]app, abused by attackers to appear legitimate.
- Information Harvesting: The subsequent pages mimic Meta’s login and account recovery processes to collect business email, page name, owner information, and even financial details under the guise of verifying the user’s identity.
- Credential Theft: Users are prompted to enter their account passwords and MFA codes. The attackers cleverly time these requests to capture the codes just as they refresh, ensuring they gain access before the codes expire.
Cofense’s investigation has also uncovered the backend operations supporting this phishing campaign. The threat actors utilize a variety of tools hosted on domains like bot1[.]sieulike[.]com, where they manage phishing links, generate emails, and track their financial gains. These tools demonstrate the efficiency and advanced capabilities of the attackers, underscoring the commercial scale of the operation.
This campaign exemplifies a concerning trend in cyber threats where attackers not only seek immediate access to accounts but also establish a foundation for subsequent attacks. By gaining control over Meta business accounts, attackers can potentially launch further malicious activities, including targeted ad campaigns that exploit the trust and reach of the compromised accounts.
The onus falls on Meta business account holders to take immediate action to protect themselves and their followers. This includes remaining vigilant about phishing emails, educating employees about the latest threats, and implementing additional security measures such as password managers and hardware-based two-factor authentication.