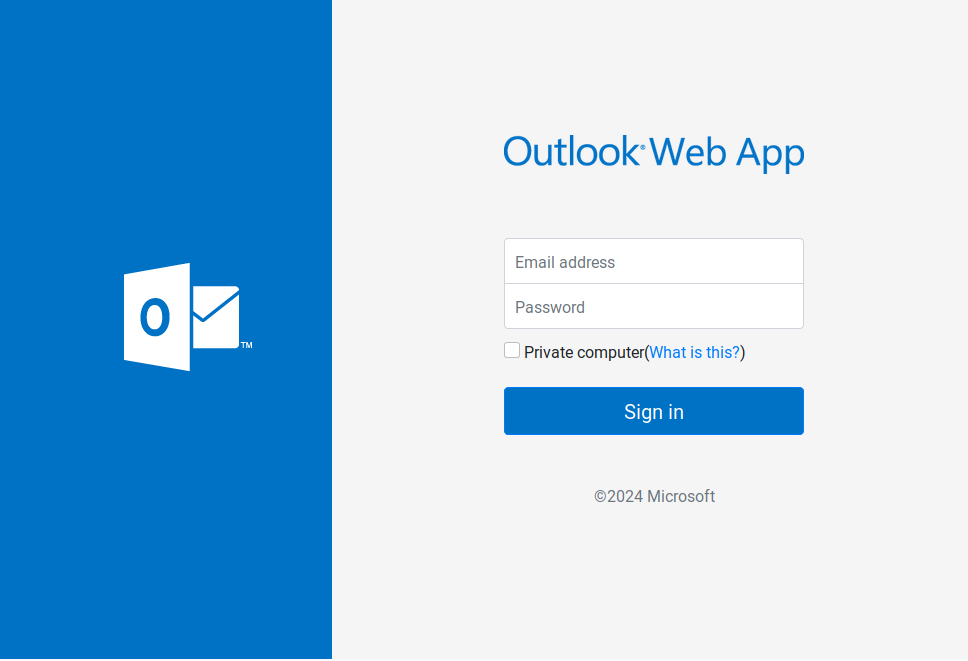
Malicious Microsoft Outlook Web App landing page | Source: Unit 42
A recent report by Unit 42 researchers has uncovered an extensive phishing campaign targeting European companies, with the automotive, chemical, and industrial compound manufacturing sectors among the hardest hit. The operation, which peaked in June 2024, utilized fake forms built with HubSpot Free Form Builder and malicious PDFs mimicking DocuSign documents to harvest credentials and compromise Microsoft Azure cloud infrastructures.
Unit 42’s investigation revealed that the threat actor aimed to deceive users into providing their Microsoft Azure login credentials. According to the report, “The phishing emails contained either an attached DocuSign-enabled PDF file or an embedded HTML link directing victims to malicious HubSpot Free Form Builder links.” Once clicked, victims were redirected through a series of malicious URLs to credential harvesting sites designed to imitate legitimate Microsoft services.
The campaign targeted approximately 20,000 users across Europe, leveraging urgency in its phishing emails. “Phishing emails often create urgency with phrases like ‘immediate action required’ to pressure quick responses,” the report noted. This tactic, combined with spoofed sender domains, enabled the attackers to bypass initial detection mechanisms.
The attackers tailored their phishing lures to reflect the branding of targeted organizations. Malicious PDFs used organization-specific names, and phishing websites mimicked official login pages. One example highlighted in the report showed how French notaries were targeted with customized phishing websites that re-used the same infrastructure observed in other attacks.
HubSpot played an unintentional role in the campaign. While the platform itself was not compromised, its Free Form Builder was exploited to create convincing phishing lures. Unit 42 emphasized, “HubSpot was not compromised during this phishing campaign, nor were the Free Form Builder links delivered to target victims via HubSpot infrastructure.”
The ultimate goal of the campaign was to gain access to victims’ Microsoft Azure environments. Once credentials were harvested, attackers used them to compromise Azure tenants, deploy persistence mechanisms, and move laterally within targeted cloud infrastructures. Unit 42 reported that attackers even engaged in tug-of-war scenarios with IT teams over account control, leveraging password reset mechanisms to maintain access.
Unit 42 has collaborated with HubSpot and affected organizations to mitigate the impact of this campaign. HubSpot has implemented additional security measures, while affected companies have been guided through recovery processes. DocuSign also responded by enhancing its preventative measures to reduce the incidence of fraudulent signature requests.
