Image: Fortra
A new report from cybersecurity firm Fortra has revealed a dramatic increase in the abuse of Cloudflare’s pages.dev and workers.dev domains for phishing attacks. This abuse capitalizes on Cloudflare’s trusted reputation and advanced infrastructure to deceive victims and execute attacks.
Cloudflare’s Pages.dev and Workers.dev services, designed for developers to deploy web applications and pages, are being exploited for their inherent advantages. According to Fortra, these platforms are attractive for both legitimate users and cybercriminals because of their “strong reputation”, “trusted branding”, and global CDN infrastructure, which ensure phishing sites load quickly and reliably.
The platforms’ free hosting, ease of use, and automatic SSL/TLS encryption provide an additional veneer of legitimacy to malicious sites. Cybercriminals also utilize custom domains and URL masking to increase the credibility of their phishing schemes. As Fortra noted, “Cloudflare’s reverse proxying renders it difficult for security controls to trace the origin of malicious content.”
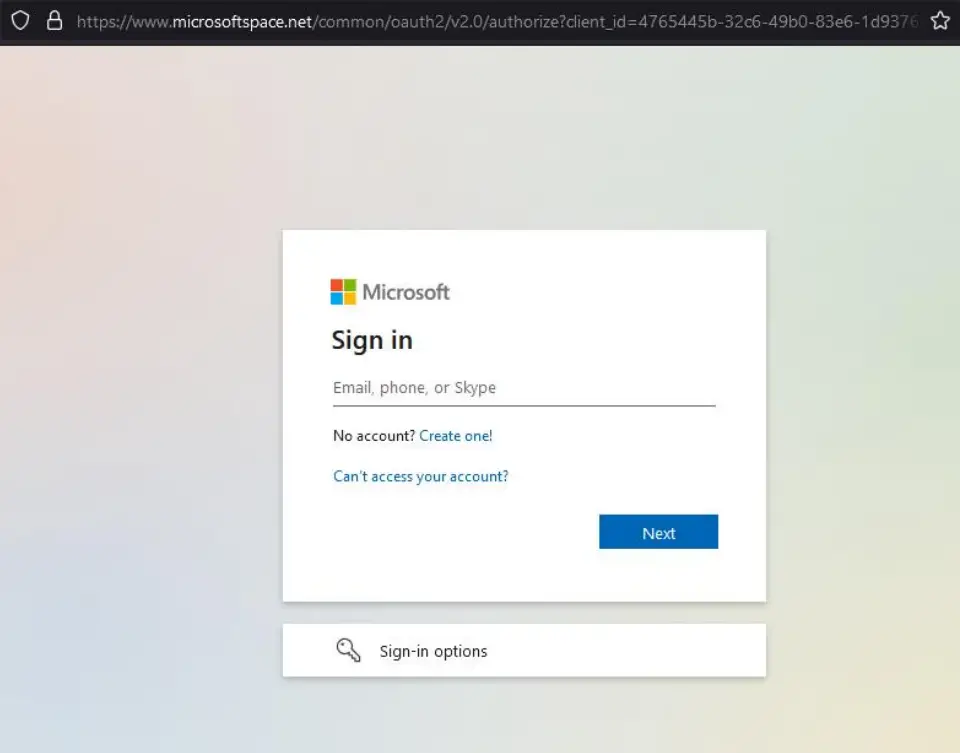
Phishing campaigns hosted on Cloudflare’s Pages.dev frequently start with emails tricking victims into clicking on malicious links. These links often lead to fraudulent documents or redirects, ultimately targeting users’ sensitive information. For example, one campaign observed by Fortra involved phishing emails directing victims to download a document via a Microsoft OneDrive page. This page then redirected users to a fake Microsoft Office365 login, where credentials were harvested. This misuse poses severe risks, including data breaches, business email compromise, and privilege escalation.
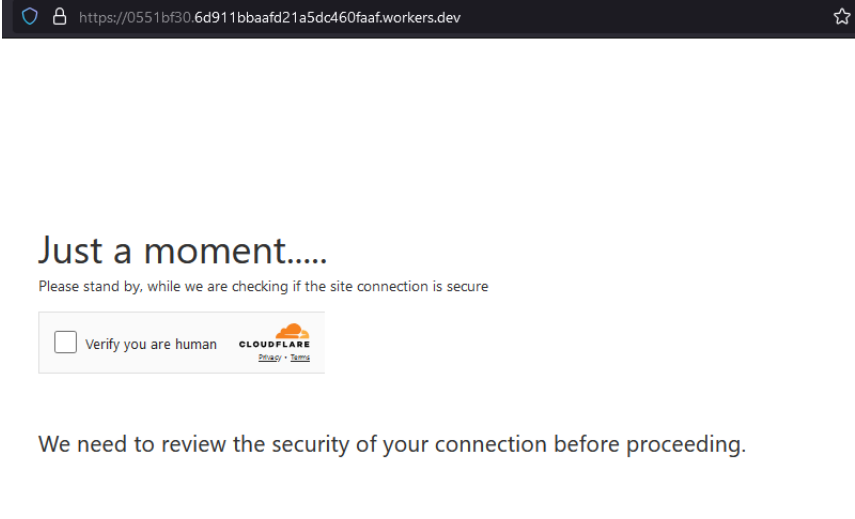
Cloudflare Workers, a serverless platform allowing JavaScript execution at the edge of Cloudflare’s CDN, has also seen increasing abuse. While designed for performance and security enhancements, it has been exploited for phishing, DDoS attacks, and malicious script injection. Fortra highlighted an instance where attackers used Workers.dev to create a human verification page mimicking CAPTCHA. This tactic increased trust, leading victims to unknowingly divulge their credentials.
The numbers underscore the scale of the problem. Fortra reports a 198% surge in phishing attacks on Cloudflare Pages, rising from 460 incidents in 2023 to 1,370 as of October 2024. This trend is projected to reach a 257% year-over-year increase by the end of the year. Similarly, phishing attacks on Workers.dev have increased by 104%, climbing from 2,447 incidents in 2023 to nearly 5,000 in 2024. These statistics emphasize the growing popularity of these platforms among cybercriminals.
Cloudflare has implemented several countermeasures, including threat detection systems and phishing reporting mechanisms. However, Fortra warns that “cybercriminals can still exploit the platform before malicious content is detected.” Users are encouraged to verify URLs carefully, enable two-factor authentication (2FA), and report suspicious activity to Cloudflare.
Related Posts:
- HTTP/2 Rapid Reset Attack: HTTP/2 Zero-Day Vulnerability Rocks Cybersecurity World
- PoC Exploit Published for Fortra GoAnywhere MFT CVE-2024-0204 Vulnerability
- Researchers Uncovers Sophisticated Phishing Campaigns Leveraging Cloudflare Workers