Tech support scams from India has recently been found to play with new tricks – scammers send phishing emails to Apple users, if users access them to fake Apple sites, and then call the Apple Care customer service phone. Because it is difficult for ordinary users to understand the complexity of phishing and the format of web pages, it is easy to mistakenly believe that their devices have been “locked for illegal activity.” After the victim clicks to complete the call, the scammer will follow to get money.
In recent years, due to the rise of the mobile Internet and smartphones, technical support scam have begun to focus on the mobile field. Because many people’s lives are closely linked to mobile devices, these goals have become “new grease.”
Jeremy Richards, a threat intelligence researcher at mobile security service provider Lookout, said:
“People are just more distracted when they’re using their mobile device and trust it more.”
Email addresses associated with Apple’s iCloud service are vulnerable to this type of phishing scam. The security researcher tried to dial the Apple “security service” prompting on the page, and the person answering the call claimed to be “Lance Roger from Apple Care.”
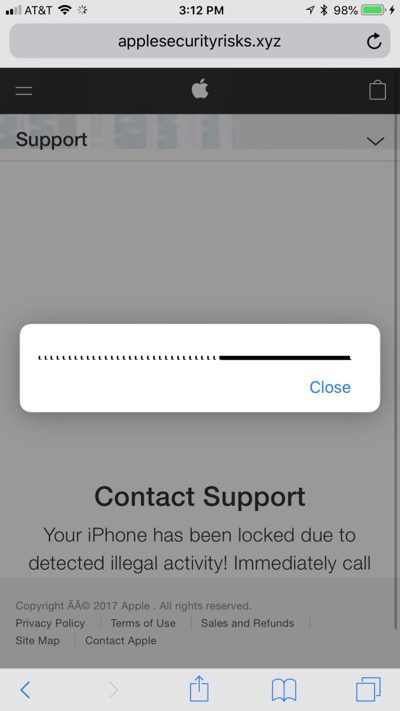
According to the routine script, the user will receive a message with a headline horror, such as “[username], Critical alert for your account ID 7458” It tries to imitate the official format, but the discerning person will always find something unnatural.
For example, this fraudulent email may warn that your login attempt for your account (email address) has been blocked and someone has just tried to log in to your profile with your password.

However, after clicking the ‘Check Activity’ button below, it will be redirected to a fraudulent website in somewhere in India. This page uses JavaScript to obfuscate the code and redirect the victim to another website. The site then jumps to applesecurityrisks.xyz again – a fake Apple Care support page.
Even worse, it uses the ‘tel’ event to activate dialing. When the user clicks, they try to initiate a FaceTime call on the iOS device.
The animated dialog on the screen will urge the victim to confirm the call after all their devices have been “locked for illegal activity.” But in fact, the website script will determine the user’s device type through the browser’s UA:
“window.defaultText=’Your |%model%| has been locked due to detected illegal activity! Immediately call Apple Support to unlock it!’;”
Fortunately, security researchers have passed the technical details of the phishing scam site to Apple security team members. Although the malicious site is still active, both Google and Apple have marked it as a phishing site.
Source, Image: arstechnica