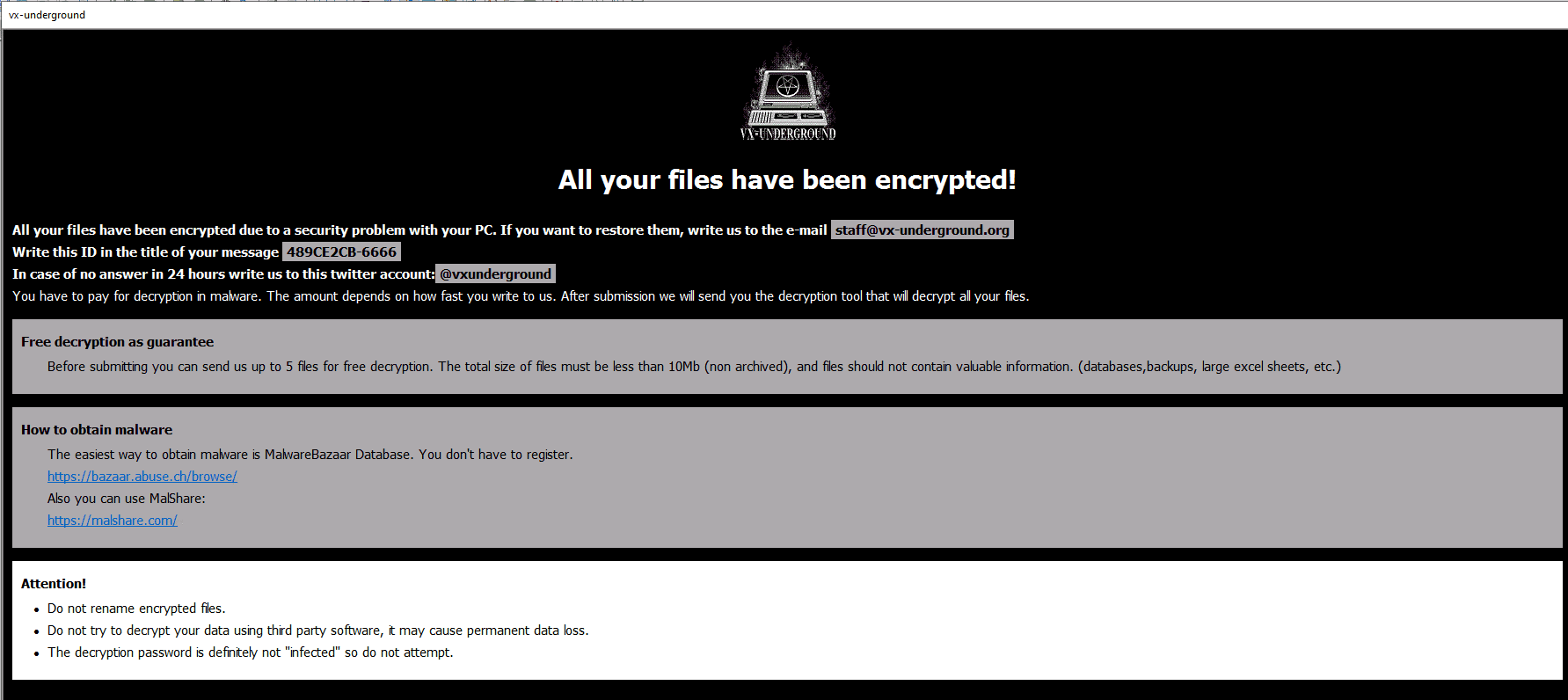
Impersonating Ransom Pop-Up
In the shadowy corners of the cyber world, a new predator has been lurking since early 2019, silently waiting for its next prey. This threat, known as the Phobos ransomware, has been creeping into systems worldwide, leaving chaos and uncertainty in its wake. Discovered by the vigilant eyes of Qualys Threat Research, Phobos has adopted a cunning strategy to camouflage its lethal intentions, impersonating the reputable VX-Underground community.
VX-Underground is the digital agora for malware experts, boasting the largest collection of malware resources on the internet. It serves as a pivotal platform for the global threat research community to share crucial malware samples. In a sinister twist, Phobos ransomware has exploited the credibility of VX-Underground, weaving a deceptive web to entrap its victims.
The Phobos ransomware is a chameleon, masking itself as a benign entity. It often masquerades under the name “AntiRecuvaAndDB.exe”, tricking users into believing it’s part of the popular Recuva data recovery software suite. This clever disguise has been repeatedly used by malefactors to spread their malicious payloads.
A closer examination of Phobos reveals it is packed with UPX Packer, specifically targeting 32-bit architectures. This packing method is a common tactic used by cybercriminals to evade detection.
Once unpacked, clear indicators betray its true nature as a member of the Phobos ransomware family, closely related to the notorious CrySIS and Dharma malware. Phobos is particularly cunning, halting its execution if it detects Cyrillic alphabets, a trick to evade detection in certain regions.
Before striking, Phobos meticulously eliminates a slew of specific processes, including database, email, and office applications. This step ensures no interference during its main operation: encrypting victim files.
Phobos doesn’t just encrypt files; it systematically dismantles system recovery options. It deletes shadow copies, disables Windows recovery, erases backup catalogs, and turns off the firewall, leaving the system vulnerable and defenseless.
After laying the groundwork, Phobos initiates its encryption routine, appending files with a “.VXUG” extension, a nod to its VX-Underground impersonation. Files are left with an ominous tag: “.id[unique_id].[staff@vx-underground.org].VXUG”. It then establishes persistence by adding itself to the startup directory and registry keys.

Phobos’ final act is the deployment of ransom notes in the hta and txt formats, starting from the Desktop directory. The hta format, in particular, is designed to create immediate panic, coercing victims into a state of urgency and fear.
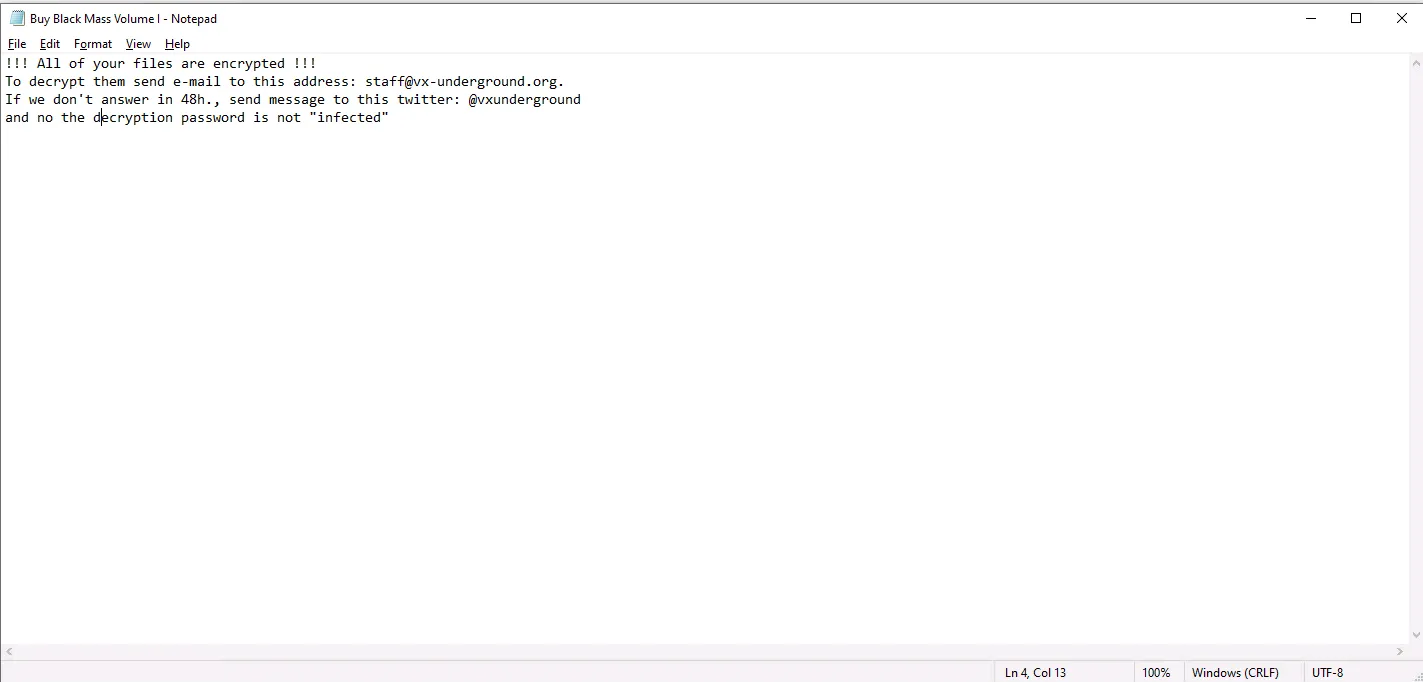
The emergence of Phobos ransomware is a stark reminder of the evolving threats in cyberspace. It underscores the importance of robust cybersecurity measures and continuous vigilance. As Phobos continues to adapt and evolve, so must our strategies to combat such insidious threats. In this digital age, awareness and preparedness are our strongest allies in the ongoing battle against cyber predators.