AMWSCAN – PHP Antimalware Scanner
PHP Antimalware Scanner, written in php, can scan PHP files and analyze your project to find malicious code inside it. It provides a text terminal console interface to scan files in a given directory and find PHP code files the seem to contain malicious code. The package can also scan the PHP files without outputting anything to the terminal console. In that case, the results are stored in a log file. This scanner can work on your own php projects and on a lot of other platforms. Use this command php -d disable_functions for running the program without issues.
Scanning mode
You could find some false positive during scanning. For this you can choice the aggression level as following:
| Param | Abbr | Aggressivity | Description |
|---|---|---|---|
| VERY AGGRESSIVE | Search for all functions/exploits on lists and all malware signatures without restrictions | ||
| –agile | -a | MEDIUM | Search for some specific exploits on lists with some restrictions and all malware signatures (on WordPress and other platforms could find more malware and more false positive) |
| –only-signatures | -s | NORMAL | Search for all malware signatures (could be perfect for WordPress and other platforms for having less false positive) |
| –only-exploits | -e | AGGRESSIVE | Search for exploits on lists |
| –only-functions | -f | MEDIUM | Search for all functions on lists (on some obfuscated code can’t be detected) |
Suggestions
no params (default) (not recommended) VERY AGGRESSIVE
–agile | -a (recommended) MEDIUM AGGRESSION
–only-signatures | -s (recommended) LESS AGGRESSIVE`
–only-exploits | -e AGGRESSIVE
–only-functions | -f (not recommended) MEDIUM AGGRESSION
Then if you run the scanner on a WordPress project or other common platforms type –only-signatures or –agile as an argument for a check with less false positive.
Examples:
php -d disable_functions=” scanner -s
php -d disable_functions=” scanner -a
Detection Options
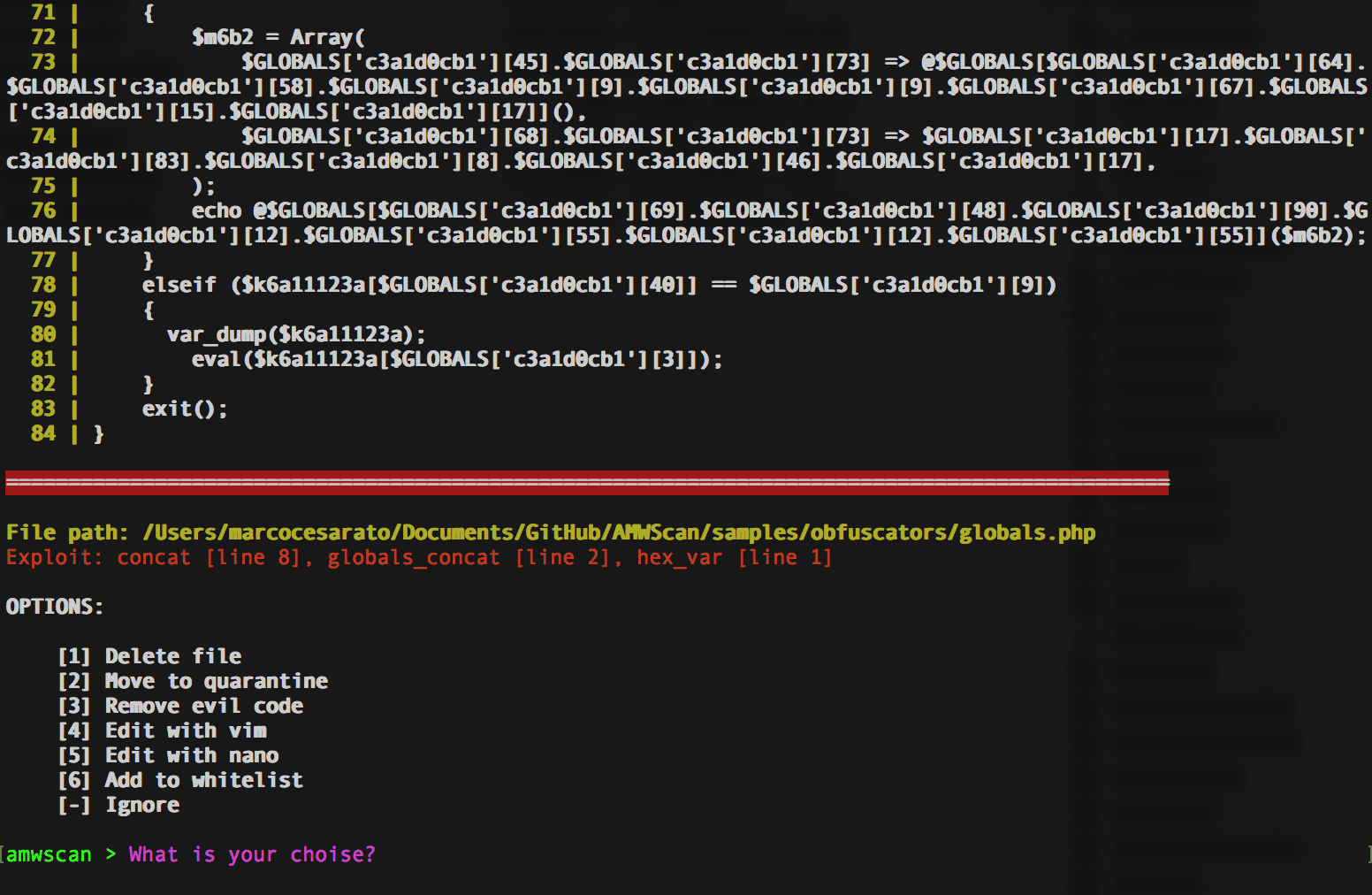
When a malware is detected you will have the following choices (except when a scanner is in report scan mode –report):
- Delete file
- Move to quarantine (move to ./quarantine)
- Try to remove evil code
- Try to remove evil line code
- Open/Edit with vim (need php -d disable_functions=”)
- Open/Edit with nano (need php -d disable_functions=”)
- Add to whitelist (add to ./scanner_whitelist.csv)
- Show source
- Ignore
Exploits and Functions List
Exploits
- eval_chr, eval_preg, eval_base64, eval_comment, eval_execution, align, b374k, weevely3, c99_launcher, too_many_chr, concat, concat_vars_with_spaces, concat_vars_array, var_as_func, global_var_string, extract_global, escaped_path, include_icon, backdoor_code, infected_comment, hex_char, hacked_by, killall, globals_concat, globals_assign, base64_long, base64_inclusion, clever_include, basedir_bypass, basedir_bypass2, non_printable, double_var, double_var2, global_save, hex_var, register_function, safemode_bypass, ioncube_loader, nano, ninja, execution, execution2, execution3, shellshock, silenced_eval, silence_inclusion, ssi_exec, htaccess_handler, htaccess_type, file_prepend, iis_com, reversed, rawurlendcode_rot13, serialize_phpversion, md5_create_function, god_mode, wordpress_filter, password_protection_md5, password_protection_sha, custom_math, custom_math2, uncommon_function, download_remote_code, download_remote_code2, download_remote_code3, php_uname, etc_passwd, etc_shadow, explode_chr
Functions
- il_exec, shell_exec, eval, system, create_function, exec, assert, syslog, passthru, define_syslog_variables, posix_kill, posix_uname, proc_close, proc_get_status, proc_nice, proc_open, proc_terminate, inject_code, apache_child_terminate, apache_note, define_syslog_variables
Changelog v0.104
Bug Fixes
- Disable html report when not on report mode #36 (49a5aa)
- Undefined index when running programmatically #35 (fb265f)
Download
Copyright (C) 2018 marcocesarato