pinky: The PHP mini Remote Administration Tool
pinky v2
Uploading a webshell is almost always the next step after exploiting a web vulnerability, but services like Cloudflare and the new generation of firewalls do a really good job preventing attackers to run commands in the target via HTTP or HTTPS. On the other hand, text content filtering and whitelisting applications policies can be easily exploited with a minimum effort and pinky is a PoC of that.
How is pinky different?
First, pinky tries to find which function is enabled to run system commands; after finding which php function is the best, all communication is encrypted, so even if the Firewall is enabled to read the traffic, it won’t be able to determine whether the activity is malicious or not. Also, pinky is able to communicate through any kind of proxy. In addition to this, we need to send a Basic Authentication (completely insecure, I know!) to avoid others to communicate with the pinky’s agent.
Download
Use
First, exploit the vulnerability found on the target.
Now, we’re ready to generate our agent using the built-in generator like this:
I’m using Obfuscator-Class by Pierre-Henry Soria to obfuscate the agent because results are pretty good.
After the agent is generated, we need to upload it into the target machine and paste the URL into the json file created previously. If we want (and we must), use a SOCKS5 proxy, we need to add the settings:
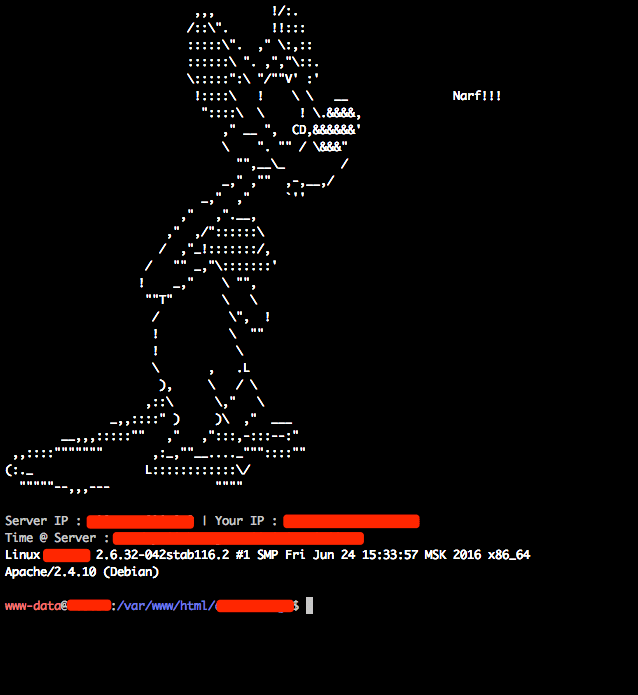
The last step is to upload the agent, open your terminal and then pass the json file as a parameter.
$ php pinky.php config.json
Copyright (C) 2017 davidtavarez
Source: https://github.com/davidtavarez/