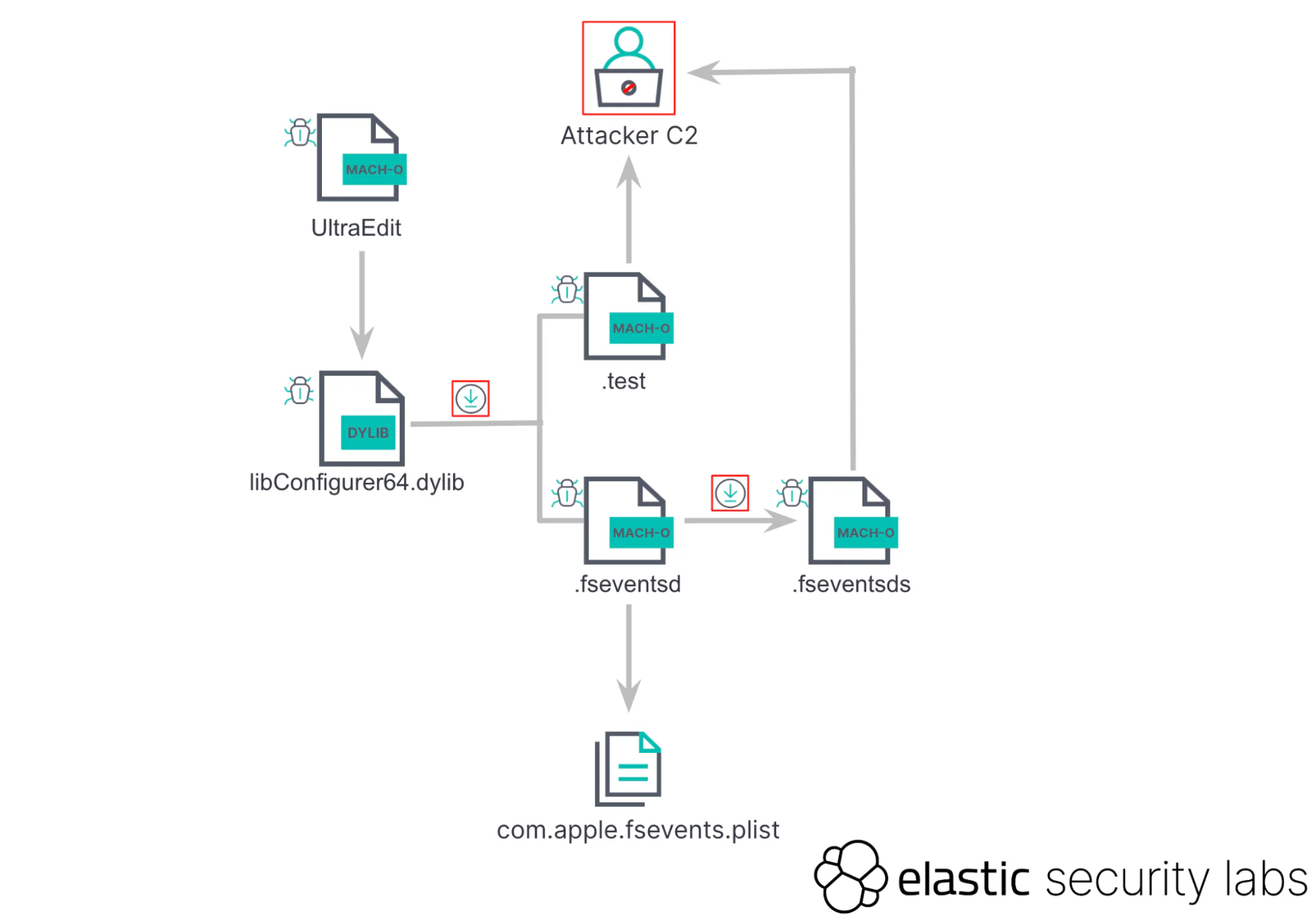
UltraEdit execution flow
Security researchers at Elastic Security Labs have pulled the curtain back on an alarmingly sophisticated malware campaign targeting macOS users. The attack begins with a seemingly innocuous, pirated version of the UltraEdit text editor. However, this trojanized application serves as a launchpad for a series of hidden payloads designed to give attackers extensive control and persistence on infected systems.
On January 12, 2024, when Malwrhunterteam, a vigilant observer of the malware landscape, spotlighted a pirated macOS application teeming with malicious intent on social media. The application in question, a compromised version of the reputable UltraEdit text and hex editor, was soon analyzed by Patrick Wardle, a noted macOS security researcher. His insights, alongside a detailed exploration by JAMF Threat Labs, laid bare the multifaceted nature of the threat.
Attack Methodology

- Initial Infection: Upon running the compromised UltraEdit application, a rogue library immediately executes, initiating the download of hidden malware payloads. The pirated UltraEdit application harbored a sinister secret: an unsigned third-party library, libConfigurer64.dylib, designed to usher in additional payloads surreptitiously. This dropper library initiates the download and execution of two hidden files, embedding themselves within the system to facilitate further malicious activities.
- Stealthy Backdoor: The campaign’s complexity unfolds with the execution of hidden binaries, such as the .test file, which masquerades as an SSH command to disguise its true nature—a backdoor providing comprehensive access to the infected system.
- Persistence & Further Attacks: Another component masquerades as a system service to secure a persistent foothold on the machine. It’s designed to download even more malicious payloads.
The Need for Behavior-Based Detection
This campaign highlights the growing sophistication of macOS threats and the limitations of traditional signature-based detection. Malware authors continue to adapt their techniques to evade static defenses.
Elastic Security Recommendations
Elastic Security Labs provides actionable guidance for detecting this threat and similar attacks. Key recommendations include:
- Unauthorized Libraries: Monitor for unsigned or untrusted libraries loaded by legitimate applications to identify early infection attempts.
- Hidden Executables: Detect the execution of concealed binaries, especially from non-standard system directories.
- Persistence Detection: Identify attempts to install malicious launch agents or daemons that masquerade as legitimate system services.
- Network Anomaly Detection: Alert on unexpected outbound connections initiated by hidden processes, which may indicate backdoor activity.