PiSavar: WiFi Pineapple Activities Detection
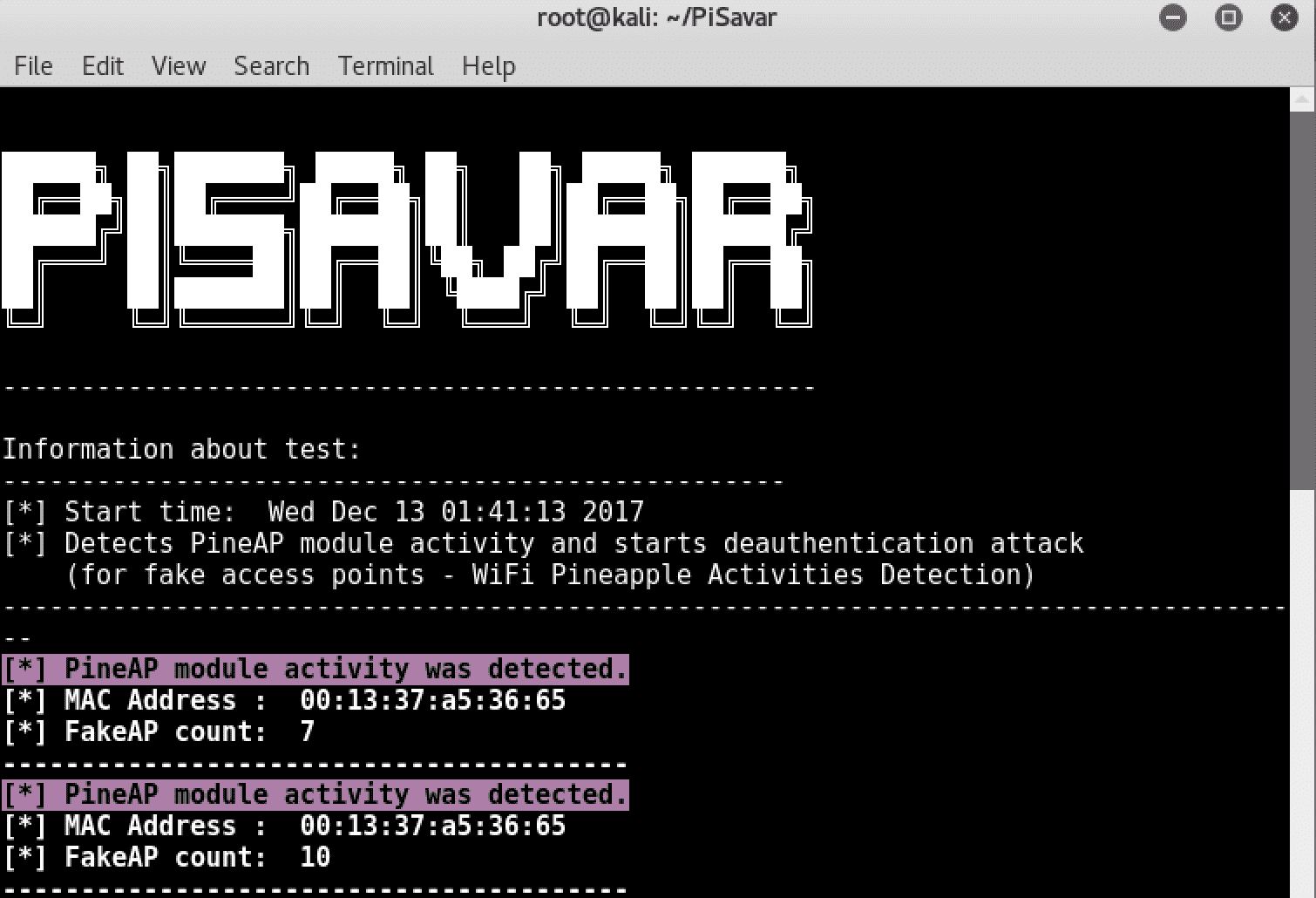
PiSavar – Detects PineAP module and starts deauthentication attack (for fake access points – WiFi Pineapple Activities Detection)
About Project
The goal of this project is to find out the fake access points opened by the WiFi pineapple device using the PineAP module and to prevent clients from being affected by initiating a deauthentication attack to the attacking device.
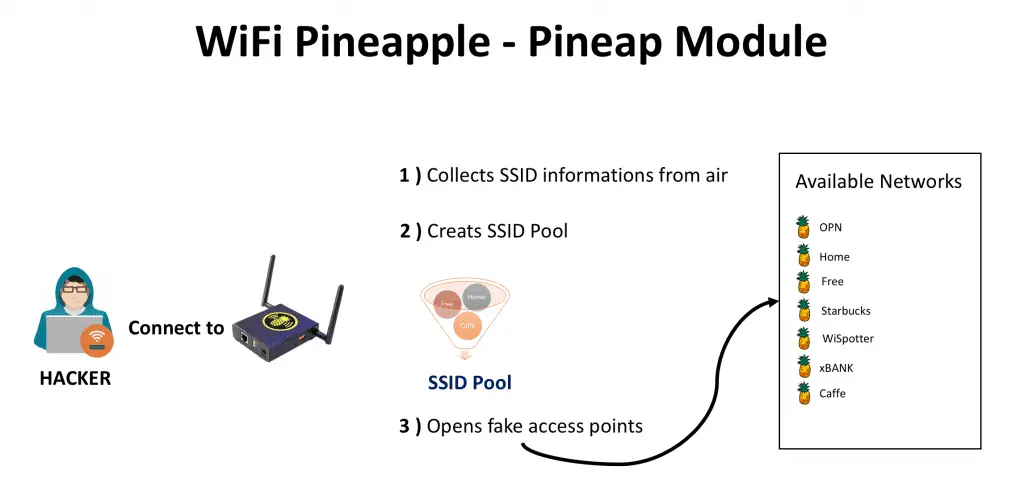
How PineAP Module Works
- Collects SSID information
- Creates SSID pool with collected SSID information
- Creates fake access points using information in the SSID pool
Features of PiSavar
- Detects PineAP activities.
- Detects networks opened by PineAP.
- Starts deauthentication attack for PineAP.
Diagram
Usage
Requirements
- Hardware: TP-LINK TL-WN722N
- Modules: scapy, time, termcolor, argparse, commands, netifaces, logging
Kali Linux:
git clone https://github.com/WiPi-Hunter/PiSavar.git
pip install termcolor
Run the program with the following command:
Monitor mode:
Run:









