Image: Binarly
In a recent and alarming discovery, cybersecurity specialists from Binarly have identified a critical flaw affecting hundreds of UEFI products from 10 prominent suppliers. The vulnerability, dubbed “PKfail,” poses a severe threat as it allows attackers to bypass Secure Boot and install malicious software directly into the system’s firmware.
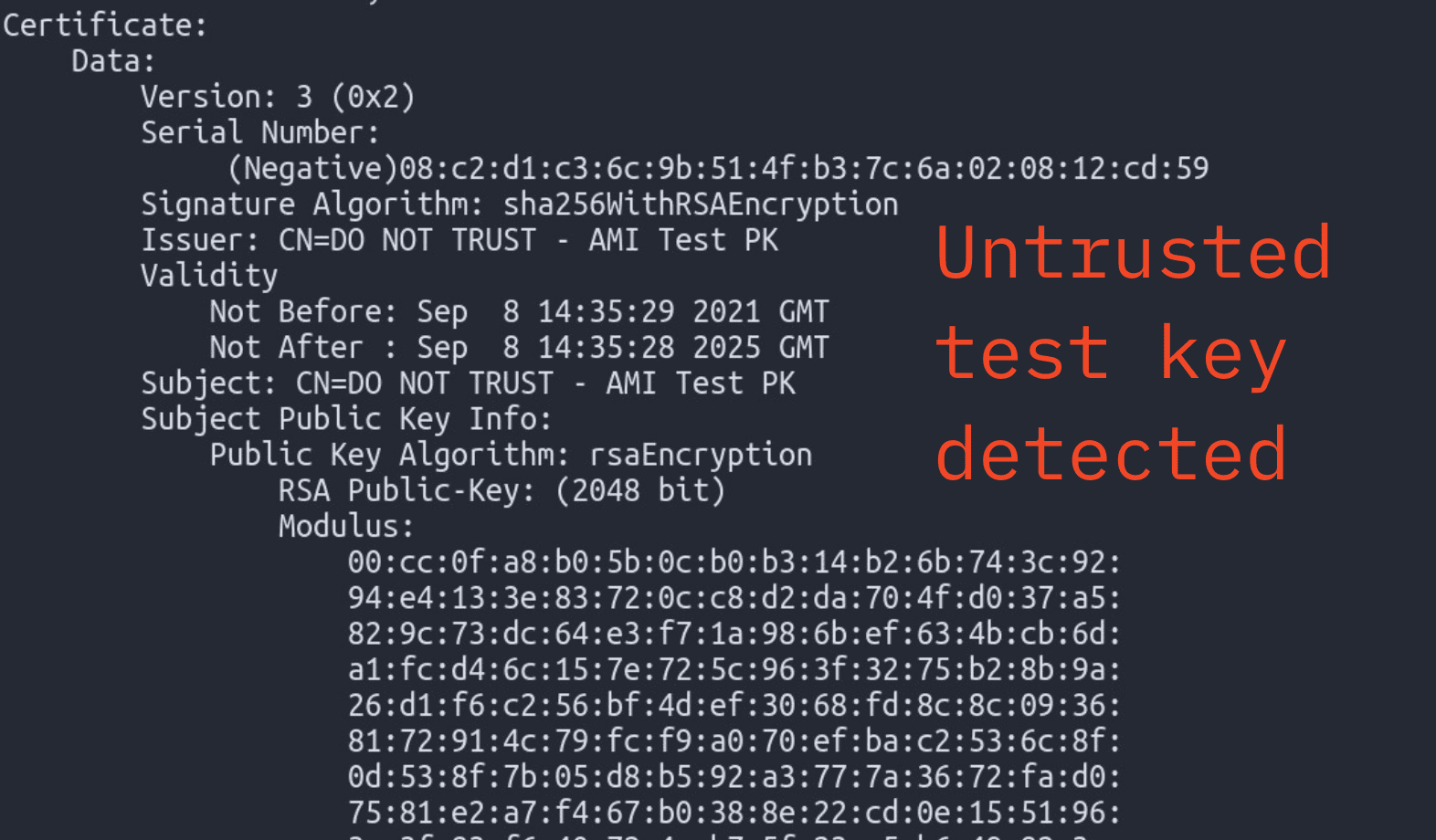
The Heart of the Issue: The Untrustworthy Platform Key
The root of this vulnerability lies in the use of a test Secure Boot key, commonly referred to as the Platform Key (PK), generated by American Megatrends International (AMI). Marked explicitly as “DO NOT TRUST,” these keys were intended to be replaced by device suppliers with their own securely generated keys. However, in many cases, OEMs and device suppliers failed to make this critical replacement, resulting in devices being shipped with unreliable keys.
The Platform Key is integral to the security of UEFI systems, managing Secure Boot databases and maintaining the trust chain from firmware to the operating system. The failure to replace these keys with secure ones has exposed numerous devices to potential exploitation.
Widespread Risk: Over 800 Devices Vulnerable
The scope of this vulnerability is vast. Among the manufacturers affected are industry giants such as Acer, Aopen, Dell, Formelife, Fujitsu, Gigabyte, HP, Intel, Lenovo, and Supermicro. In total, 813 products are at risk. If a cybercriminal gains access to these vulnerable devices along with the private part of the Platform Key, they can bypass Secure Boot protections. By manipulating the Key Exchange Key, Signature Database, and Forbidden Signature Database, the attacker can compromise the entire security chain, from firmware to the operating system. This breach allows them to sign and distribute UEFI rootkits like CosmicStrand and BlackLotus, further endangering the security of the affected systems.
An Enduring Threat: Over a Decade of Vulnerability
Binarly’s research indicates that this issue has been persistent for over 12 years, with the first vulnerable firmware released in May 2012 and the latest as recent as June 2024. This makes PKfail one of the most prolonged vulnerabilities of its kind, highlighting a significant oversight in the firmware supply chain.
Detailed Findings and Mitigation Measures
A more in-depth analysis revealed that more than 10% of the examined firmware images utilize untrustworthy Platform Keys. Binarly’s platform identified 22 unique untrustworthy keys among nearly 900 affected devices, as detailed in the vulnerability description BRLY-2024-005, which carries a CVSS score of 8.2.
To mitigate the risk, Binarly advises suppliers to generate and manage Platform Keys using hardware security modules. They should replace any test keys provided by independent BIOS vendors with securely generated proprietary keys. Users, on the other hand, are urged to keep an eye on firmware updates and promptly apply all security patches related to the PKfail issue.
Taking Action: Resources for Users
To assist users in identifying and addressing this vulnerability, Binarly has launched a dedicated website, pk.fail. This resource allows users to scan firmware binaries for vulnerable devices and malicious payloads free of charge, providing an essential tool in the fight against this significant security threat.
In conclusion, the PKfail vulnerability uncovered by the Binarly Research Team underscores the critical importance of robust security practices in the firmware supply chain. By addressing these vulnerabilities and implementing the recommended safeguards, the tech industry can better protect against future threats and ensure the integrity of UEFI systems.
Related Posts:
- LogoFAIL Vulnerabilities Expose Firmware Attacks: Endpoint Security Solutions at Risk
- 22,000 Suppliers Hit in Daikin Data Breach