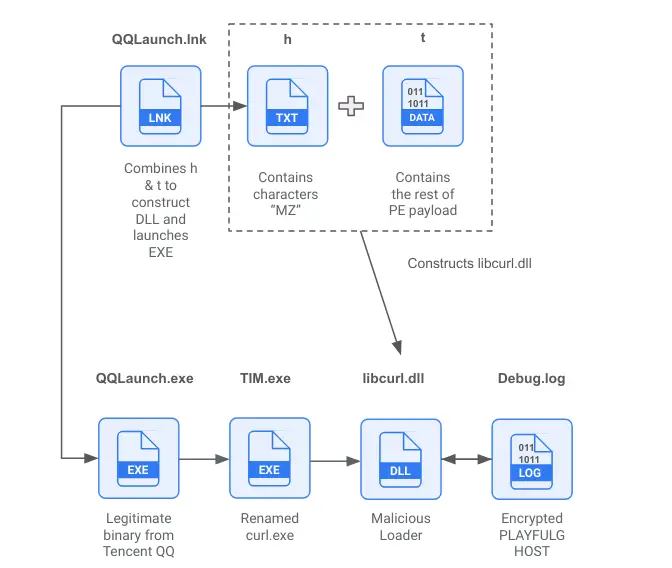
LNK combines the files “h” & “t” to construct malicious DLL and launches EXE | Source: Google
A detailed analysis from security researcher Tatsuhiko at Google has unveiled the sinister capabilities of PLAYFULGHOST, a highly sophisticated backdoor rooted in the notorious Gh0st RAT. Leveraging unique traffic patterns and encryption, PLAYFULGHOST poses a severe threat with its advanced functionality and clever distribution techniques.
PLAYFULGHOST malware builds upon the legacy of Gh0st RAT, a remote administration tool whose source code was leaked in 2008. The malware not only supports keylogging, screen capture, audio capture, and file execution but also features functionalities aimed at anti-forensics, remote control, and privilege escalation.
“PLAYFULGHOST distinguishes itself through its use of distinct traffic patterns and encryption,” the analysis noted.
PLAYFULGHOST malware exploits two primary attack vectors to infiltrate systems:
- Phishing Emails: Attackers use themes such as “code of conduct” to lure victims into downloading malicious RAR archives disguised as image files. Once extracted and executed, these files initiate the download of PLAYFULGHOST from a remote server. A malicious RAR archive cleverly masked with a .jpg extension serves as the initial infection vector.
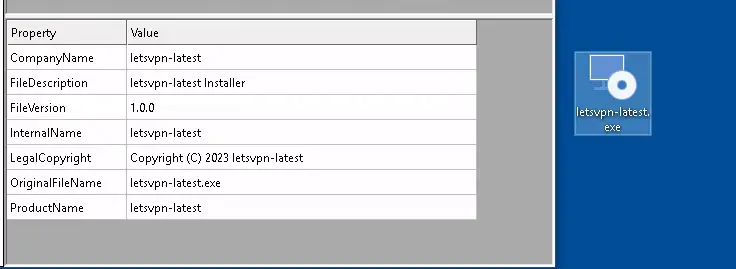
- SEO Poisoning: The malware is bundled with popular applications like LetsVPN and distributed via manipulated search engine results, making it appear as a legitimate download. “Upon execution, the trojanized installer drops an additional malicious Windows executable designed to download PLAYFULGHOST components from a remote server,” Tatsuhiko explained.
PLAYFULGHOST employs a multi-step execution process:
- A legitimate executable vulnerable to DLL hijacking loads a malicious DLL.
- The malicious DLL decrypts and injects the PLAYFULGHOST payload into memory.
In one scenario, a renamed Tencent executable (“svchost.exe”) loads the malicious DLL, which then activates PLAYFULGHOST. Another observed tactic involves a Windows LNK file combining fragments to construct a malicious DLL and launching it through legitimate Tencent binaries.
The malware is often deployed alongside additional tools like BOOSTWAVE (an in-memory dropper) and CHROMEUSERINFO.dll, which extracts stored credentials from Google Chrome.
PLAYFULGHOST backdoor secures persistence through registry run keys, scheduled tasks, and startup folder entries. It supports a wide range of malicious functions, including data theft, file manipulation, remote shell access, and even nuisance activities like blocking mouse input or opening the CD tray.
Google’s SecOps team has shared actionable detection techniques, leveraging MITRE ATT&CK® frameworks to identify malicious registry keys, scheduled tasks, and suspicious network activity linked to PLAYFULGHOST.
Related Posts:
- Warning: DLL Hijacking in Modern Malware Campaigns
- The Rise of Fake Online Meeting Websites Spreading Android and Windows RATs
- Beware! Fake Notion Installer Spreads Data-Stealing Malware
- WikiKit Phishing Kit Targets Major Industries with Evasive Techniques