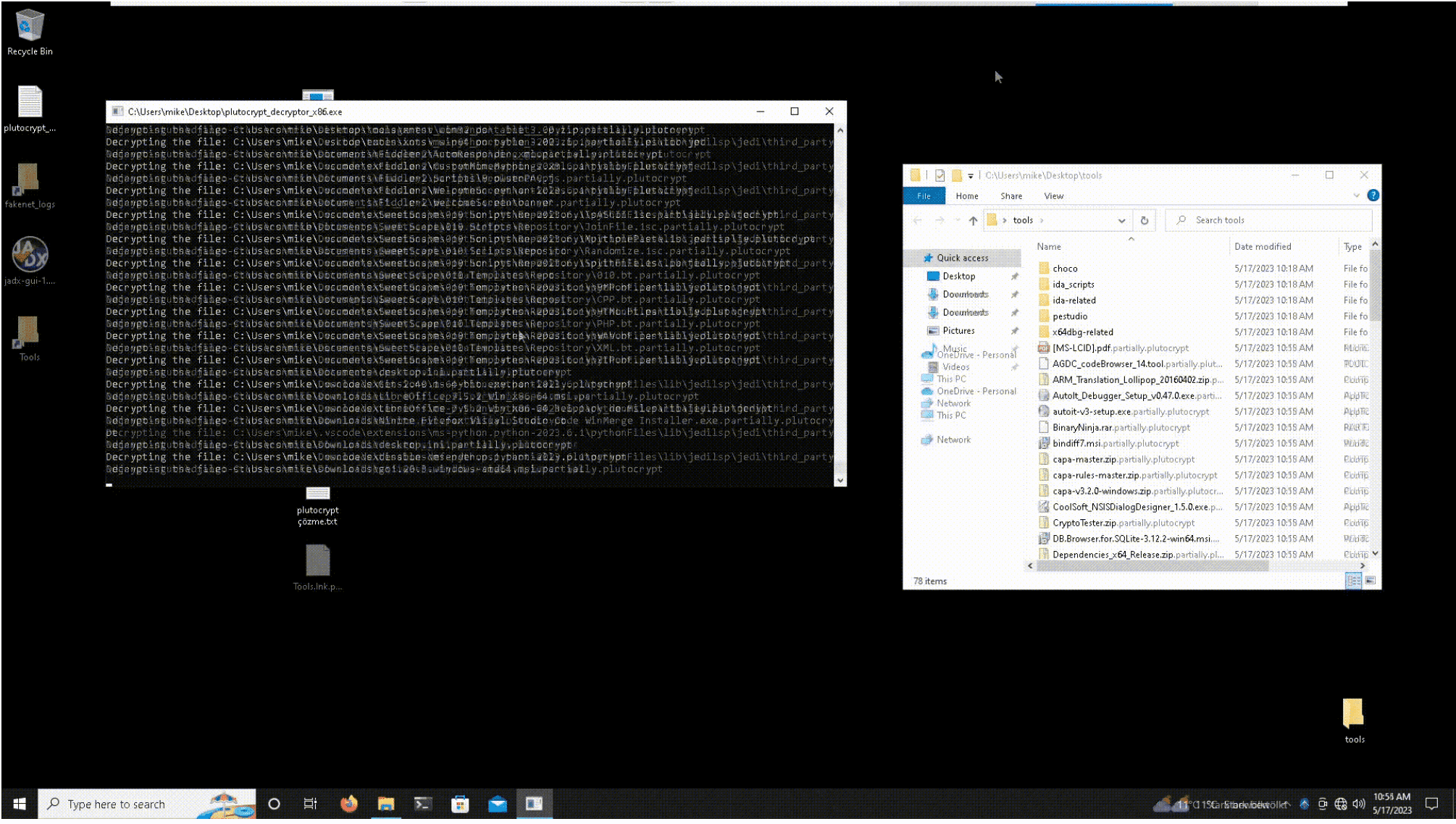
PlutoCrypt Ransomware Decryptor
What are PlutoCrypt and The Decryptor?
PlutoCrypt is a variant of CryptoJoker ransomware. The decryptor in this repository has been developed for PlutoCrypt – but with a small modification, it can also work for other CryptoJoker variants.

How does it work?
PlutoCrypt encrypts files with a randomly generated key which has a 20-byte key size. The encryption is byte addition with this key. The decryptor performs a known plaintext attack, and the plaintext is !This program cannot be run in DOS text sequence that starts at position 77 of the Windows executables. Since it is longer than 20 bytes, it is more than enough for recovering the key.
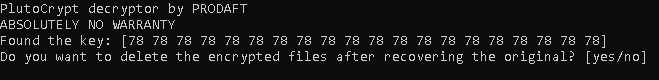
Note: Due to a wrong implementation of PlutoCrypt’s encryption function, the effective key size is 1 byte rather than 20 bytes. Hence, when the decryptor is running, the found key will have the same byte size. An example screenshot is given below. However, in case of any future development of the malware, we have implemented the decryptor with the assumption that the key size is still going to be 20 bytes.
How to run the decryptor?
- Download the decryptor executable from the release page or build as explained in How to build from the source section
- Move the executable to your infected machine
- Run the executable by double clicking
- The executable will ask you to keep the encrypted files or delete them. Answer that question with a yes or no depending on your preference
- When the execution is finished, press enter to exit
- Some files may not be recovered due to certain permissions. In that case, these errors will be logged into the plutocrypt_decryptor_err.log file located in the same position as the executable. It is recommended to read that log file after the execution.
Copyright © PRODAFT SARL. 2023