A newly discovered vulnerability in the TP-Link Archer AXE75 router, tracked as CVE-2024-53375, could allow remote attackers to execute arbitrary commands on vulnerable devices. This critical flaw, identified by security researcher Thanatos, affects the HomeShield functionality of the router and has been confirmed to be exploitable on firmware version 1.2.2 Build 20240827.
The vulnerability stems from a lack of proper input validation in the /admin/smart_network?form=tmp_avira endpoint. An attacker can craft a malicious HTTP POST request to this endpoint, triggering the execution of arbitrary commands on the router.
“This code harbors a Remote Code Execution (RCE) vulnerability because it parses the OwnerId directly to the os.execute function, without any sanitization nor checks,” Thanatos explains in their technical analysis.
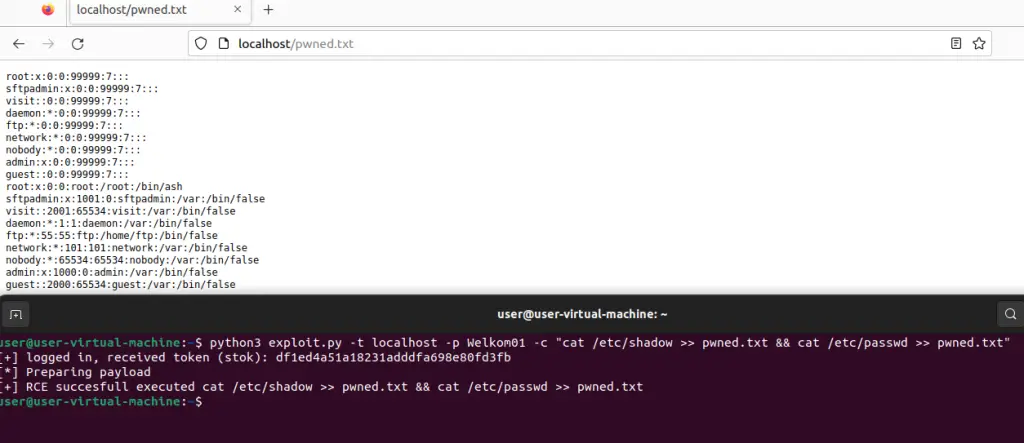
To exploit this vulnerability, an attacker needs to manipulate five parameters in the request: ownerId, date, type, startIndex, and amount. A proof-of-concept (POC) exploit code demonstrating the CVE-2024-53375 vulnerability has been published on GitHub.
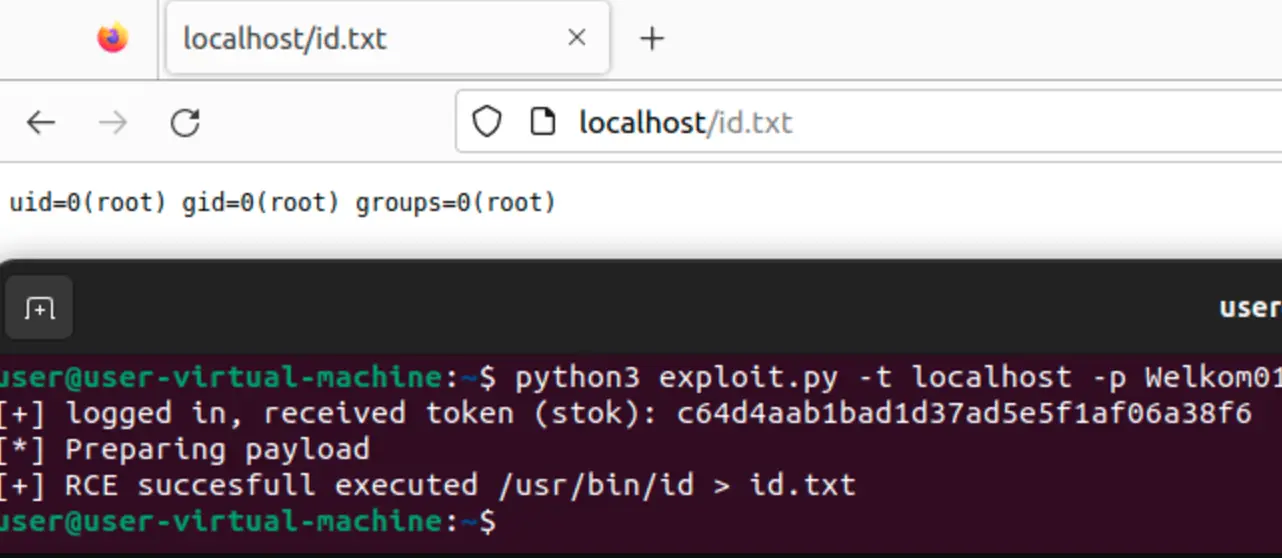
Furthermore, the researcher successfully executed the id command, confirming that the exploit runs with root privileges, granting the attacker complete control over the device.
TP-Link has acknowledged the vulnerability and has reportedly provided a fixed beta firmware version. However, a stable, publicly available firmware update is yet to be released. However, users are urged to act promptly to secure their devices by applying the update and disabling unnecessary services. Administrators should also enforce strong passwords for all accounts to minimize the risk of compromise.
Thanatos provides a detailed write-up of the vulnerability discovery process and exploitation techniques on their website, which includes insights into how the exploit was identified and tested. For more information, readers can refer to Thanatos’ detailed blog post or access the PoC code on GitHub.
Related Posts:
- Old Vulnerability, New Attacks: Botnets Swarm Exploited CVE-2023-1389 in TP-Link Routers
- Researchers Uncover Massive Quad7 Botnet Targeting Microsoft 365
- CVE-2024-42815 (CVSS 9.8): Buffer Overflow Flaw in TP-Link Routers Opens Door to RCE
- Congress Scrutinizes TP-Link Routers Over Cybersecurity Concerns