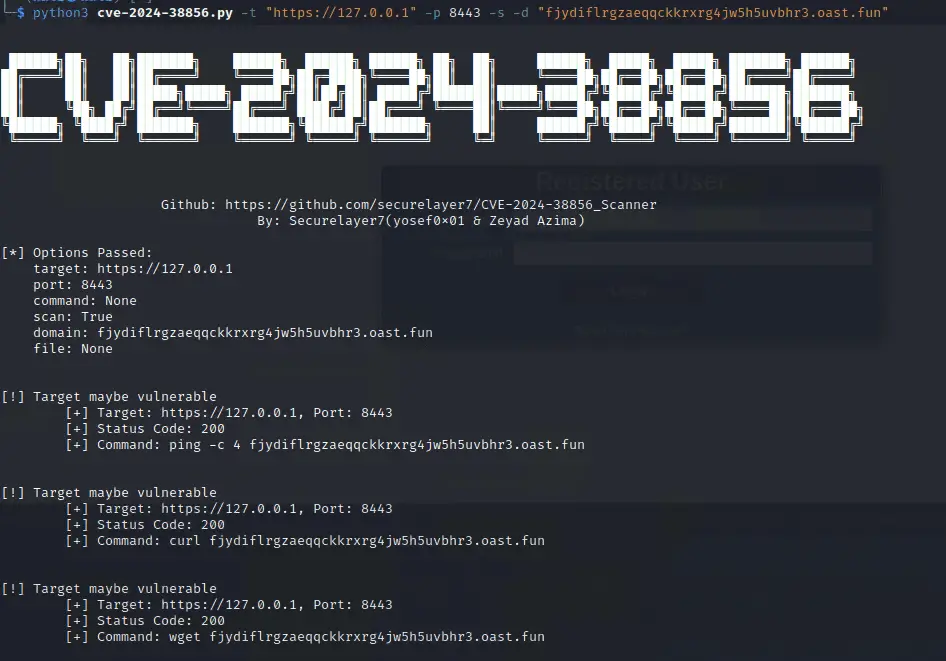
Today, cybersecurity researcher Zeyad Azima from SecureLayer7 and Youssef Muhammad have published a proof-of-concept (PoC) exploit code for a critical vulnerability (CVE-2024-38856) in the Apache OFBiz open-source enterprise resource planning (ERP) system. This vulnerability is a pre-authentication remote code execution flaw that poses a severe threat to affected systems, with a CVSS score of 9.8 out of 10.
CVE-2024-38856 affects Apache OFBiz versions prior to 18.12.15. The root cause of this vulnerability is a flaw in the authentication mechanism that allows unauthenticated users to access functionalities typically restricted to logged-in users. This breach paves the way for remote code execution, enabling threat actors to execute arbitrary code on the compromised systems.
SonicWall, the security firm that discovered and reported this vulnerability, highlighted that the flaw resides in the override view functionality of Apache OFBiz. This critical weakness exposes essential endpoints to unauthenticated attackers, who can exploit it via specially crafted requests.
Interestingly, CVE-2024-38856 is also a patch bypass for a previously addressed vulnerability, CVE-2024-36104. The earlier flaw, a path traversal vulnerability, was fixed in early June with the release of Apache OFBiz version 18.12.14. However, the newly discovered vulnerability can bypass this patch, making it imperative for users to update their systems to version 18.12.15.
Security researcher Hasib Vhora from SonicWall provided additional insights, explaining that the exploit involves abusing the override view functionality. Unauthenticated access is granted to the ProgramExport endpoint by chaining it with other non-authenticated endpoints. This method allows attackers to achieve remote code execution without prior authentication, significantly increasing the risk for affected systems.
The PoC exploit code for CVE-2024-38856 is now available on GitHub, providing a tangible demonstration of how the vulnerability can be exploited. This availability raises the stakes, urging administrators to take immediate action.
To mitigate the risks associated with CVE-2024-38856, it is crucial for organizations using Apache OFBiz to update their installations to version 18.12.15 without delay. This update addresses the vulnerability, preventing unauthorized access and potential remote code execution.
Related Posts:
- CVE-2024-38856: Critical Apache OFBiz Flaw Opens Door to Unauthorized Code Execution
- Actively Exploited Apache OFBiz Flaw Triggers Urgent Security Alert
- Multi security vulnerabilities was found on Apache OFBiz
- Critical Pre-auth RCE Vulnerability Discovered in Apache OFBiz
- RCE Vulnerability in Apache OFBiz: Immediate Action Required