Image: Synacktiv
Synacktiv’s cybersecurity researcher Baptiste MOINE has uncovered a critical format string vulnerability in the Synology TC500 security camera, running on an ARM 32-bit architecture. This flaw, residing in a Web service function parsing HTTP requests, has raised significant concerns about security camera vulnerabilities in today’s interconnected world. Despite robust protections such as Address Space Layout Randomization (ASLR) and Position Independent Executables (PIE), this vulnerability remained exploitable.
In his detailed analysis, MOINE explained how the vulnerability stemmed from improper handling of format strings within the print_debug_msg function. He pointed out, “The function allows an attacker to control the format string passed to vsnprintf, leading to potential arbitrary memory writes.” Such a flaw in formatting HTTP requests opened up critical access for attackers, enabling controlled memory modifications that bypassed ASLR and PIE protections.
The challenge was not trivial: payloads were limited to 128 characters with restricted character ranges (0x00 to 0x1F), and, crucially, attackers had no visibility into the format string output, making it a “blind exploitation” scenario. According to MOINE, “The absence of stack or base address leaks meant we had no visibility into the memory layout,” adding an extra layer of complexity.
MOINE’s strategy to tackle this vulnerability was sophisticated. By leveraging indirect memory manipulation, he overcame payload and visibility limitations to achieve arbitrary code execution. The process involved a manipulation technique: “We found a looping pointer that could be modified to point to another area of the stack… creating a double pointer, allowing us to use the first pointer to modify the second, effectively pointing it to any location on the stack.” This allowed MOINE to target precise stack locations despite the constraints.
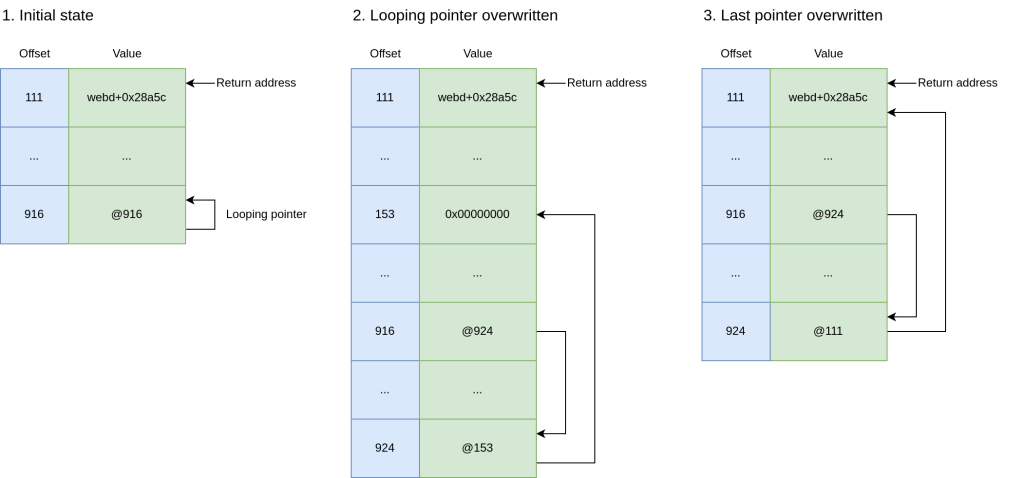
Once arbitrary write access was established, MOINE began constructing a Return-Oriented Programming (ROP) chain in unused stack space within the vulnerable function’s stack frame. He used format string specifiers like %*X$c and %Y$c to read specific stack values and store them in the “character counter.” Through precise increments, he adjusted values and placed gadget addresses within the unused stack space.
This meticulous process built the ROP chain byte-by-byte, eventually enabling the execution of a final command via system(). The exploit crafted a shell command byte-by-byte, using “sh${IFS}-c${IFS}’echo${IFS}synodebug:synodebug|chpasswd;telnetd’”, which was written in memory for execution.
Baptiste MOINE published a Python script to exploit this flaw to get a root shell and take over TC500 and BC500 camera models.
Synology has since patched this vulnerability in its TC500 and BC500 camera models, addressing the flaw in firmware version 1.1.3-0442 ahead of Pwn2Own, ensuring the exploit could not be executed during the competition. For affected users, updating to the latest firmware is highly recommended to prevent potential exploitation.
Related Posts:
- Synology Fixes Critical Vulnerabilities in Synology Photos and BeePhotos After Pwn2Own Exposure
- Synology Surveillance Station Vulnerabilities Expose Systems to Attack – Update Immediately
- Critical Flaw in Synology Camera Firmware Expose Devices to RCE and DoS Attacks
- Synology Camera Critical Vulnerabilities Patched: Upgrade Immediately