PoC Exploit Releases for Critical Progress Flowmon Bug – CVE-2024-2389 (CVSS 10)
Researchers at Rhino Security Labs have detailed a critical security flaw in Progress Flowmon, a widely used network monitoring tool. Identified as CVE-2024-2389, this vulnerability allows for unauthenticated command injection with a severity score of 10 on the CVSS scale, indicating the highest level of risk.
The flaw was discovered during an exhaustive enumeration of unauthenticated endpoints within the software’s code, specifically within the “AllowedModulesDecider.php” file. This file lists modules accessible without user authentication, among which the “Service:Pdfs:Confluence” module was found to contain exploitable code linked to PDF generation functionalities.
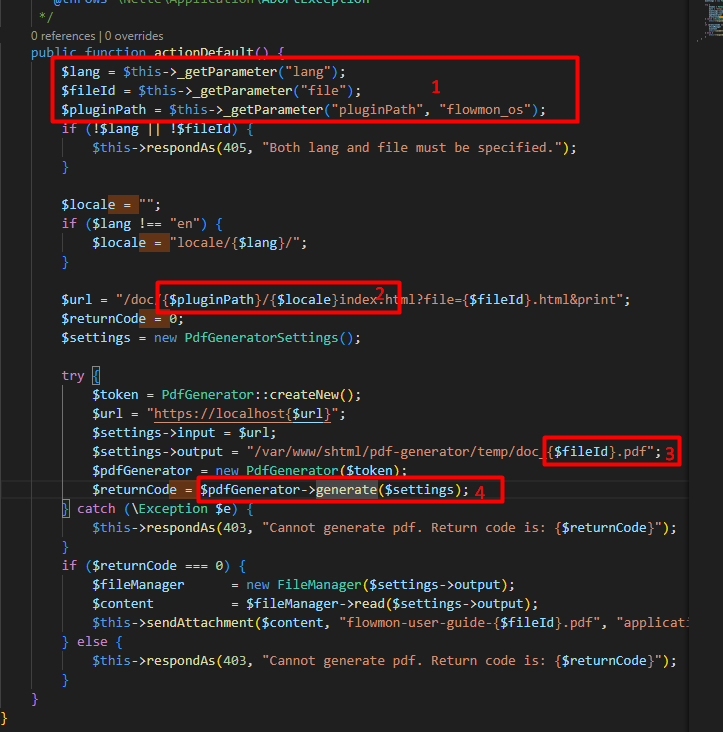
Image: Rhino Security Labs
The vulnerability stems from how “ConfluencePresenter.php” handles user input parameters such as `pluginPath`, `locale`, and `file`. These parameters are directly passed into the URL and file output strings, which are then utilized by the “PdfGenerator.generate()” method. This method acts as a wrapper for executing system commands through “getExec.run()”.
Due to the flawed handling where command parameters are passed as a single string rather than an array, attackers can manipulate the input fields to inject malicious commands. This allows them to escape the intended command constraints and execute arbitrary system commands.
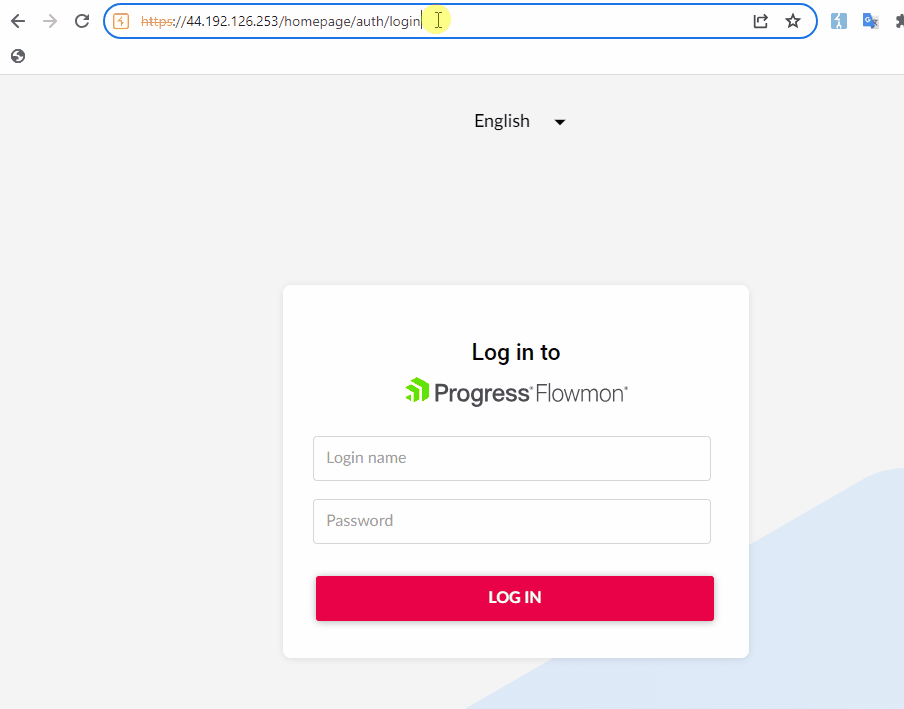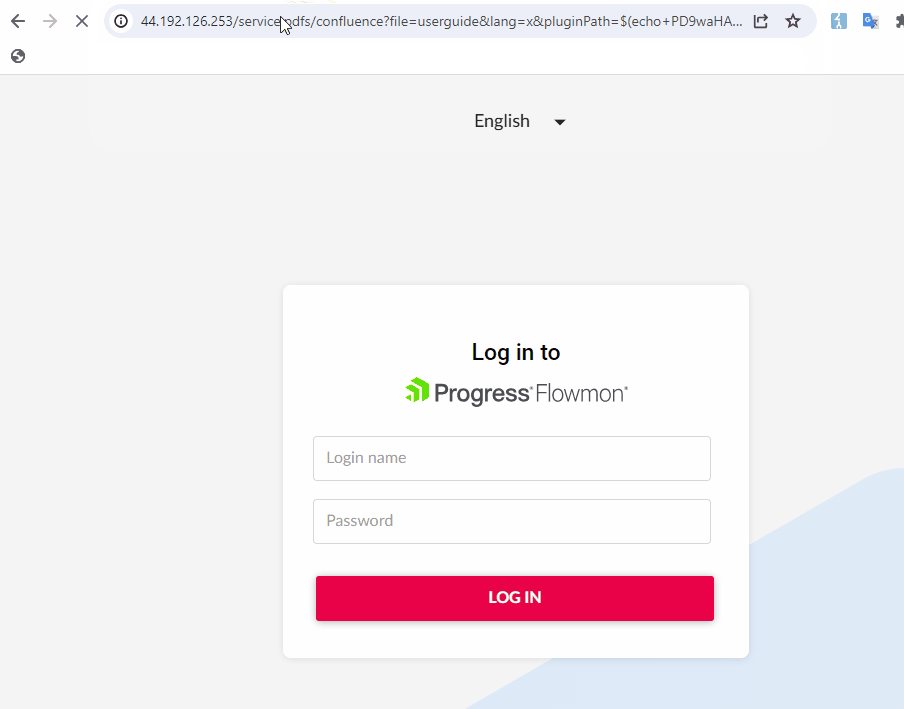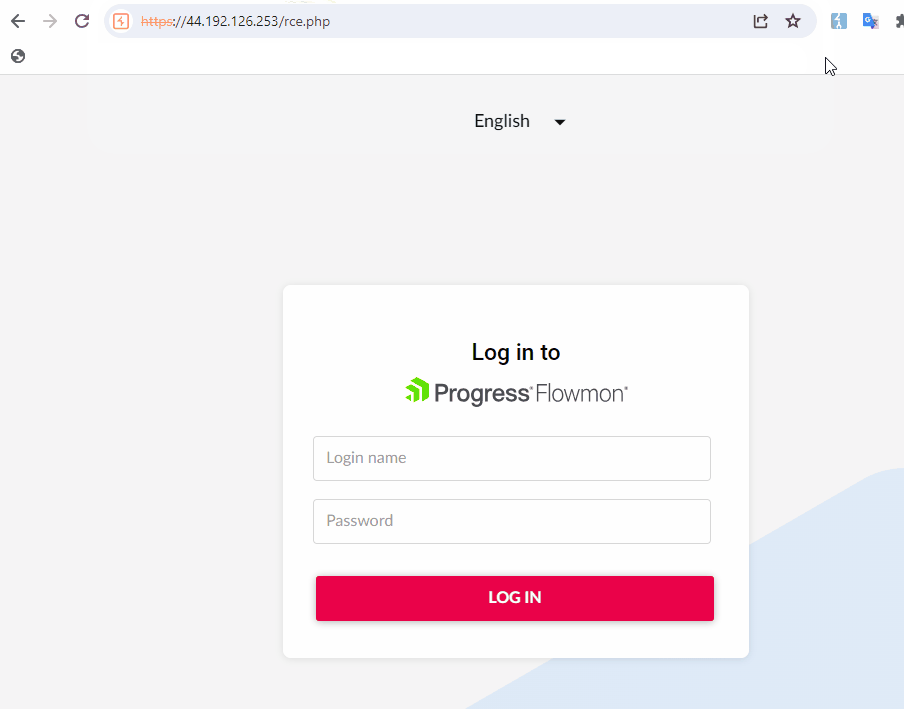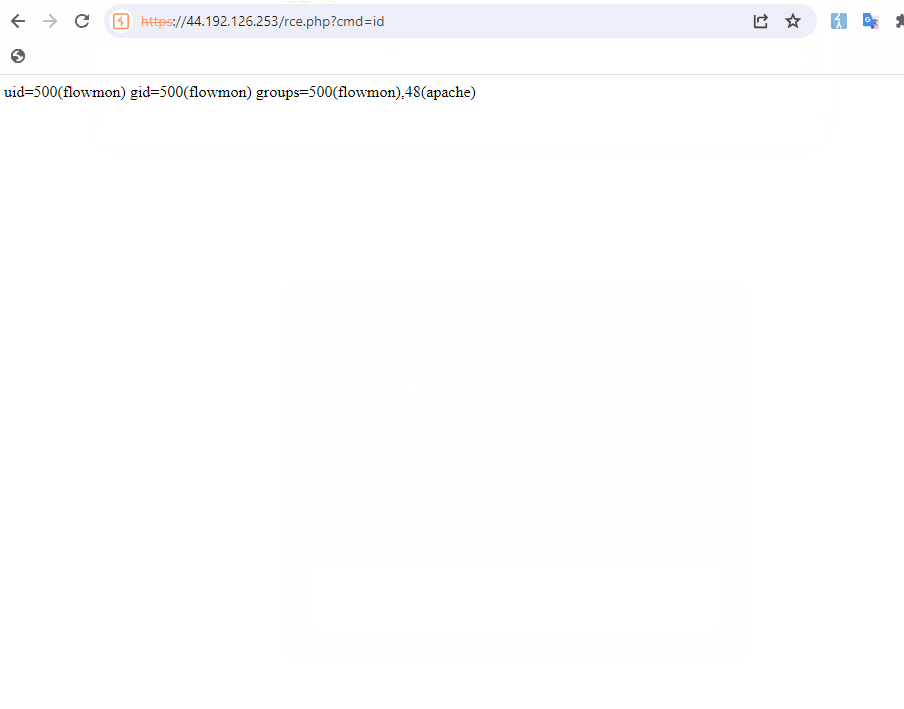
By exploiting this vulnerability, attackers can inject commands to write a web shell into the server directory, such as “/var/www/shtml/”, effectively gaining the ability to remotely control the affected server. The example provided by the researchers led to the creation of a malicious file “rce.php”, demonstrating the ease with which the system integrity could be compromised.

Image: Rhino Security Labs
Once initial command execution is established, the threat actors can operate under the “flowmon” user context. This user has sudo privileges for several commands, which can be further exploited to achieve a root shell, elevating the attacker’s control over the system.
Rhino Security Labs has not only disclosed the CVE-2024-2389 vulnerability but has also provided a proof of concept (PoC) in their CVE GitHub repository. Additionally, a Metasploit module has been developed, which is in the process of being integrated into the main project, further aiding cybersecurity professionals in testing and mitigating the vulnerability in their network environments.
In response to the discovery, Progress has released patched versions of Flowmon—versions 12.3.5 and 11.1.14—that address this critical vulnerability. Users of the software are urged to update their installations immediately to protect their networks from potential exploits.





