Image: mbog14
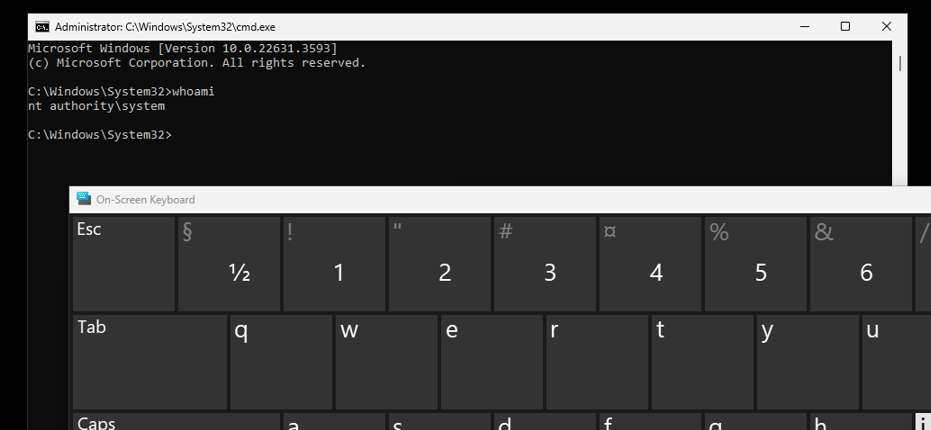
Security researcher mbog14 has published the technical details and proof-of-concept for a critical local privilege escalation (LPE) vulnerability affecting iTunes version 12.13.2.3, identified as CVE-2024-44193 (CVSS 8.4). This flaw, which has since been patched by Apple as of September 12, 2024, allows an attacker to gain SYSTEM-level access on Windows machines through an exploit involving the AppleMobileDeviceService.exe component installed alongside iTunes.
The vulnerability lies in the improper handling of user permissions within the directory C:\ProgramData\Apple\*. Low-privileged users, such as those in the local “Users” group, have write access to this directory, opening the door for an attacker to exploit the service. By restarting the AppleMobileDeviceService.exe service—an action that can be triggered by any unprivileged user—the attacker can leverage a file/folder deletion primitive to execute arbitrary code at the SYSTEM level.
As mbog14 explains, “The SYSTEM process will recursively query the subdirectories within the C:\ProgramData\Apple\Lockdown* path and delete files with the Delete On Close option enabled.” This behavior allows attackers to craft NTFS junctions that direct the service to delete specific files, potentially leading to SYSTEM privilege escalation.
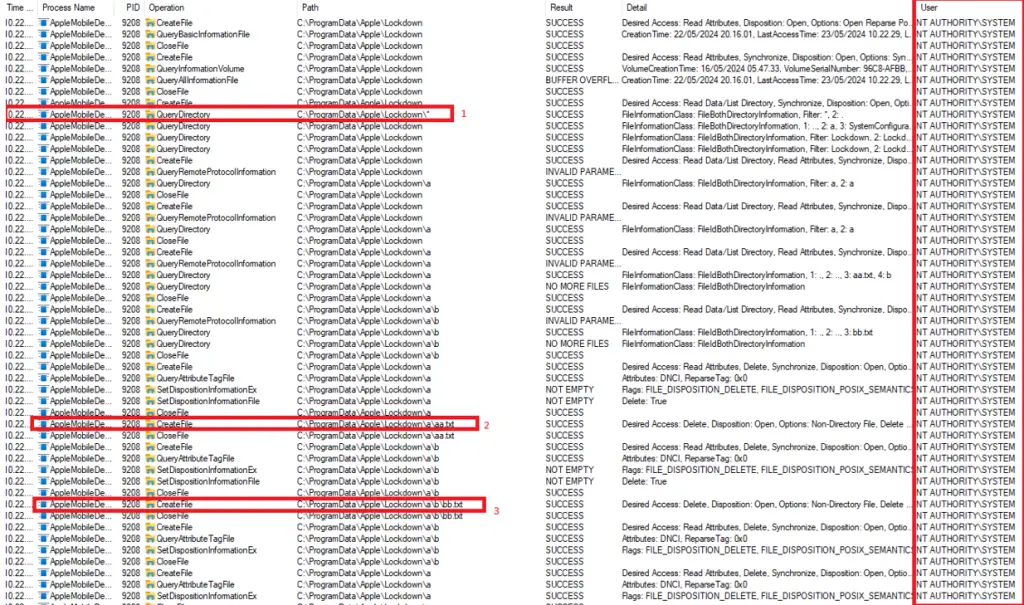
To exploit CVE-2024-44193, mbog14 demonstrated the use of NTFS junctions (similar to symlinks in Linux) to redirect file deletion to sensitive areas of the system. By carefully preparing junctions and leveraging Windows’ MSI rollback trick, the vulnerability can be triggered to overwrite critical files like HID.DLL in the C:\Program Files\Common Files\microsoft shared\ink\ directory. This ultimately results in spawning a SYSTEM shell.
The proof of concept (PoC) consists of five key steps, as described by the researcher:
- Set an oplock on the Lockdown directory to halt the process at the right time.
- Restart the Apple service, allowing the process to follow the NTFS junction.
- Prepare an MSI rollback trick to ensure that a malicious rollback script is used during the deletion process.
- Prepare the NTFS junction to point the file deletion operation to the MSI installer.
- Release the oplock, which triggers the race condition, allowing the malicious script to be written and executed
mbog14 explains the final step, where the exploit concludes with a SYSTEM shell: “Because we have overwritten the HID.DLL in C:\Program Files\Common Files\microsoft shared\ink\ using the malicious rollback script, a CMD shell will pop as SYSTEM, finishing our exploit.”
Apple has already patched this vulnerability in the latest version of iTunes, and users are strongly advised to update to version 12.13.2.3 or higher. However, this vulnerability serves as a critical reminder to carefully manage service permissions and user access on sensitive directories, particularly those that run with elevated privileges.
For security professionals and researchers interested in replicating the proof-of-concept exploit for CVE-2024-44193, mbog14 has provided detailed documentation and tools on their GitHub repository.
Related Posts:
- Researchers Detail Critical Vulnerability in AI-as-a-Service Provider Replicate
- Adobe releases the security updates to fix Remote Code Execution/Arbitrary file deletion in multi products
- Apache ActiveMQ Remote Code Execution Vulnerability