Image: Mouad Kondah
The researcher published the technical details and a proof-of-concept (PoC) exploit for CVE-2024-38821 (CVSS 9.1). This vulnerability, affecting versions of Spring WebFlux, allows attackers to access restricted resources under certain conditions, posing a serious threat to applications dependent on Spring’s WebFlux module.
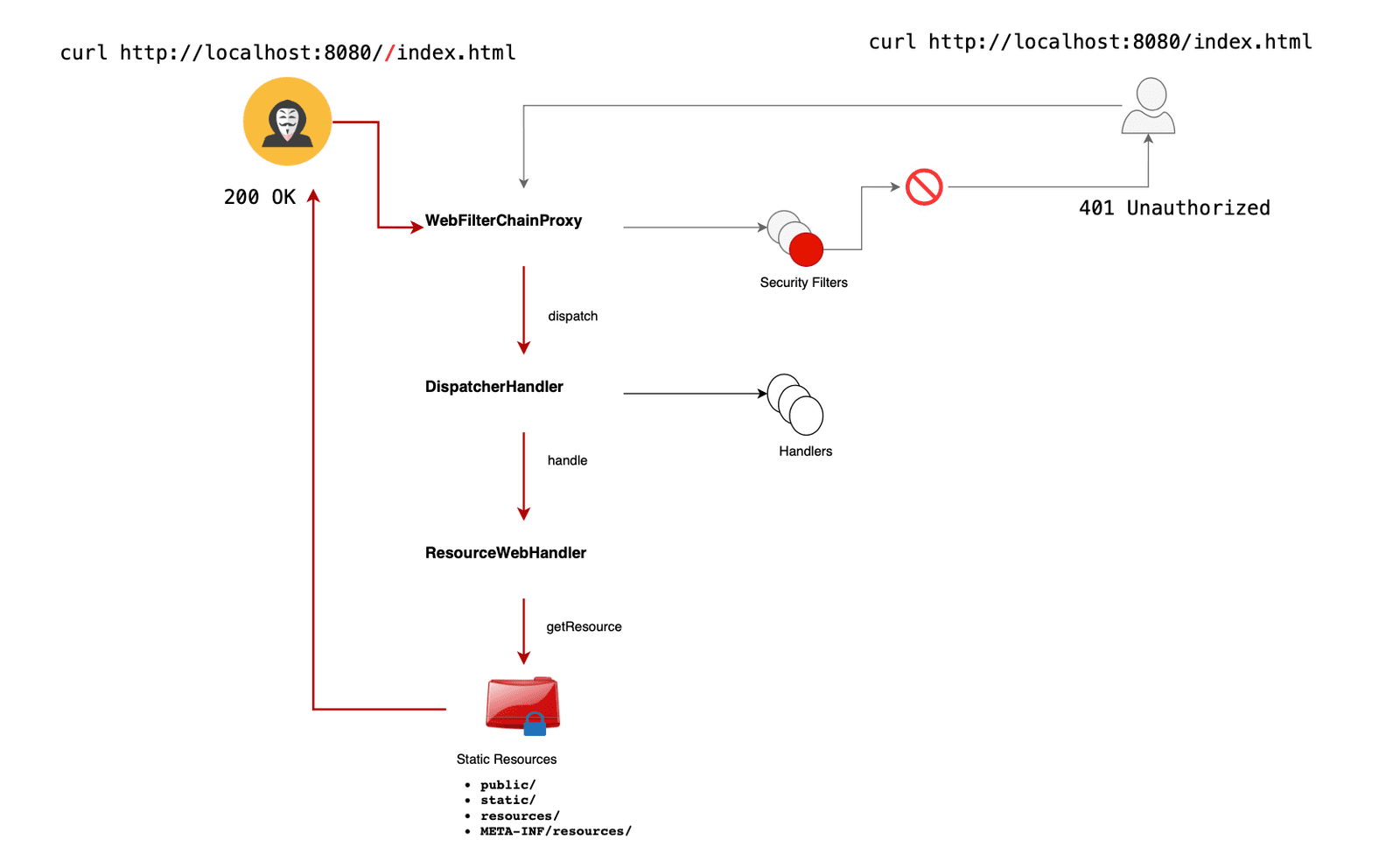
According to cybersecurity researcher Mouad Kondah, the issue lies specifically in how Spring WebFlux handles static resources. Kondah explains that when security filters are bypassed, an attacker can exploit crafted URL paths to access protected files. For example, manipulating the URL path from /index.html to //index.html can allow attackers to bypass the strict path-matching rules used by Spring Security filters, potentially exposing sensitive resources.
The vulnerability impacts WebFlux applications utilizing static resources with non-permitAll authorization rules. This means that applications relying on Spring’s ResourceWebHandler—responsible for serving static resources such as images, HTML files, and YAML files—are at risk. The core issue arises because Spring’s security filters, implemented through classes like WebFilterChainProxy, do not correctly intercept or block unauthorized access when URL path manipulation is used.
The attack flow begins with a request bypassing the security filter, allowing the attacker’s request to reach the DispatcherHandler. Kondah illustrates that for each mapping, the DispatcherHandler tries to find an appropriate handler. If all security filters are bypassed, unrestricted access may result. This sequence leads the request to the ResourceWebHandler, which processes the crafted path, ultimately exposing restricted resources without proper authorization.
Interestingly, only static resources are vulnerable in this scenario. Non-static resources in Spring employ additional path validation through strict predicates like PathPatternPredicate, which Kondah describes as capable of rejecting manipulated paths that don’t match predefined patterns. This stringent filtering results in a 400 NOT FOUND error if the attacker attempts unauthorized access to non-static resources, effectively blocking unintended access. Kondah released a PoC exploit code for CVE-2024-38821 on his Github repo.
To mitigate the vulnerability, Spring recommends updating to the latest secure versions. Users of affected versions should upgrade to their respective fixed versions to prevent exploitation. Versions with patches include 5.7.13, 5.8.15, 6.0.13, 6.1.11, 6.2.7, and 6.3.4, though some of these are available only through Enterprise Support.
Related Posts:
- CVE-2024-38821 (CVSS 9.1) Allows Authorization Bypass in Spring WebFlux Applications
- Spring Security fixes two high-severity flaws
- Spring Framework Multiple Security Vulnerability
- Muti vulnerabilities (Remote Code Execution) exist on Spring