PoC released for critical CloudPanel CVE-2023-35885 vulnerability
CloudPanel is a free and modern server control panel that allows users to configure and manage their servers with ease. However, a recently discovered vulnerability in CloudPanel 2 could allow attackers to bypass authentication and gain unauthorized access to the file manager.
The vulnerability, which has been assigned the identifier CVE-2023-35885, affects CloudPanel 2 versions prior to 2.3.1. It stems from the fact that the file manager in CloudPanel 2 does not perform session authentication. This means that an attacker can simply insert the encrypted value of the clp-fm cookie with the default secret key to gain access to the file manager.
Once an attacker has gained access to the file manager, they can upload malicious files to the server. These files could then be used to launch further attacks, such as privilege escalation or data theft.
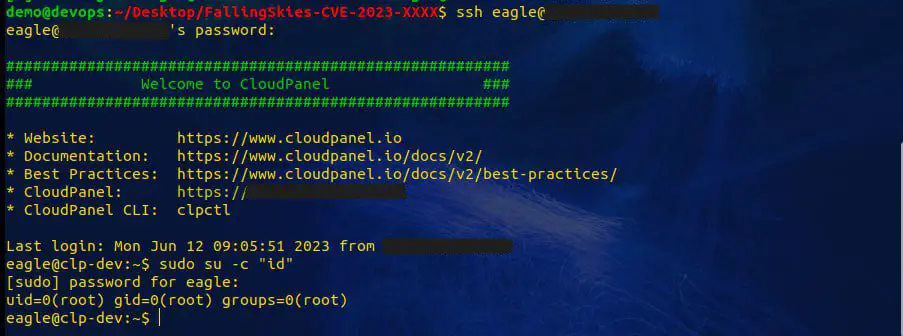
The vulnerability has been exploited in the wild, and security researcher Farhan Phakhruddin has published a PoC exploit code that can be used to exploit the CVE-2023-35885 vulnerability. PoC for CVE-2023-35885 could potentially allow an attacker to upload a webshell into the server. Phakhruddin has released the technical details for this security issue on his blog, offering a deeper insight into the mechanism of this vulnerability.

CloudPanel has released a patch for the vulnerability in version 2.3.1. Users are advised to upgrade to the latest version of CloudPanel as soon as possible.
Impact of the Vulnerability
The impact of the CVE-2023-35885 vulnerability can be significant. By exploiting the vulnerability, an attacker could gain unauthorized access to the file manager on a CloudPanel server. This could allow the attacker to upload malicious files to the server, which could then be used to launch further attacks.
In addition, the vulnerability could also be used to escalate privileges on the server. This is because the default user for the file manager, clp, has sudo privileges. This means that an attacker who gains access to the file manager could use the sudo command to execute commands with root privileges.
Mitigation Strategies
There are a number of steps that can be taken to mitigate the risk posed by the CVE-2023-35885 vulnerability. These include:
- Upgrading to CloudPanel version 2.3.1 or later.
- Enabling session authentication for the file manager.
- Using a strong secret key for the clp-fm cookie.
- Keeping the clp-fm cookie up to date.
The CVE-2023-35885 vulnerability is a serious security issue that could allow attackers to gain unauthorized access to CloudPanel servers. Users are advised to upgrade to CloudPanel version 2.3.1 or later as soon as possible. In the meantime, they should take steps to mitigate the risk posed by the vulnerability, such as enabling session authentication for the file manager and using a strong secret key for the clp-fm cookie.





