Image: Sekoia
The PolarEdge botnet, a sophisticated IoT-based malware campaign, has been discovered by Sekoia’s Threat Detection & Research (TDR) team, targeting vulnerable Cisco Small Business Routers and other edge devices. The botnet has infected over 2,000 devices globally and has been active since at least late 2023.
The attack campaign exploits CVE-2023-20118, a remote code execution (RCE) vulnerability affecting multiple Cisco Small Business Router models.
“On 22 January 2025, suspicious network traces were observed via our honeypots. Analysis indicated an attempt to exploit the CVE-2023-20118 vulnerability. Through this exploit, the attacker executed a remote command (RCE) to deploy a webshell on the target router,” the report states.
The flaw stems from improper input validation in /cgi-bin/config_mirror.exp, allowing unauthenticated attackers to execute commands remotely by crafting malicious HTTP requests.
Between January 22 and 31, 2025, attackers deployed a base64-encoded, gzip-compressed webshell to vulnerable routers. “To achieve persistence, the attacker replaced the router’s authentication CGI script (/usr/local/EasyAccess/www/cgi-bin/userLogin.cgi) with their webshell,” the report explains. This method ensures attackers maintain control over infected routers while evading detection.
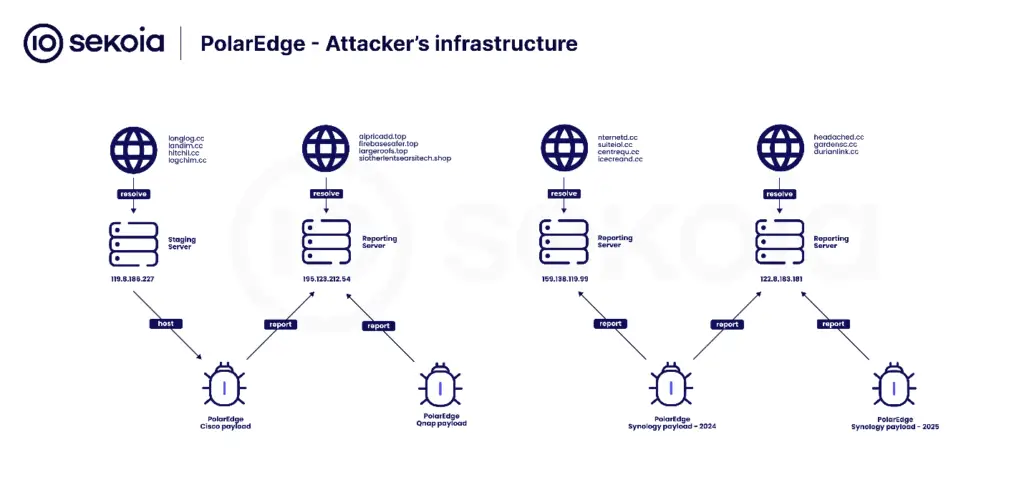
By February 10, 2025, PolarEdge operators evolved their tactics, replacing the webshells with a TLS backdoor implant, signaling a transition to large-scale botnet infrastructure. “The study of these payloads led to the discovery of a botnet comprising over 2,000 infected assets around the world, as well as the attacker’s infrastructure.”
PolarEdge employs multiple evasion and persistence techniques, including:
- Hiding its presence: Deletes logs and its own execution traces.
- Killing competing malware: Terminates suspicious processes.
- Leveraging encrypted command channels: Uses Mbed TLS (formerly PolarSSL) to secure C2 communications.
- Updating attack infrastructure dynamically: Shifts from hardcoded C2 servers to domain generation algorithms (DGA).
The TDR team identified compromised devices across multiple regions, with the U.S. leading infections (540 IPs), followed by Taiwan and South America. The botnet’s ability to target various architectures (Cisco, Asus, QNAP, and Synology) suggests an ongoing expansion of operations.
“PolarEdge botnet has been active since at least the end of 2023, targeting a wide range of devices and associated with a significant infrastructure,” the report concludes.
Related Posts:
- Chinese Hackers Suspected in Ivanti CSA Attacks: Webshells and Lateral Movement Detected Sources and related content
- IoT Botnet Fuels Large-Scale DDoS Attacks Targeting Global Organizations
- Hackers use Cisco Router flaws to attack Iran, 3,500 routers hacked