PortEx
PortEx is a Java library for static malware analysis of Portable Executable files. Its focus is on PE malformation robustness, and anomaly detection. PortEx is written in Java and Scala, and targeted at Java applications.
Features
- Reading header information from: MSDOS Header, COFF File Header, Optional Header, Section Table
- Reading PE structures: Imports, Resources, Exports, Debug Directory, Relocations, Delay Load Imports, Bound Imports
- Dumping of sections, resources, overlay, embedded ZIP, JAR or .class files
- Scanning for file format anomalies, including structural anomalies, deprecated, reserved, wrong or non-default values.
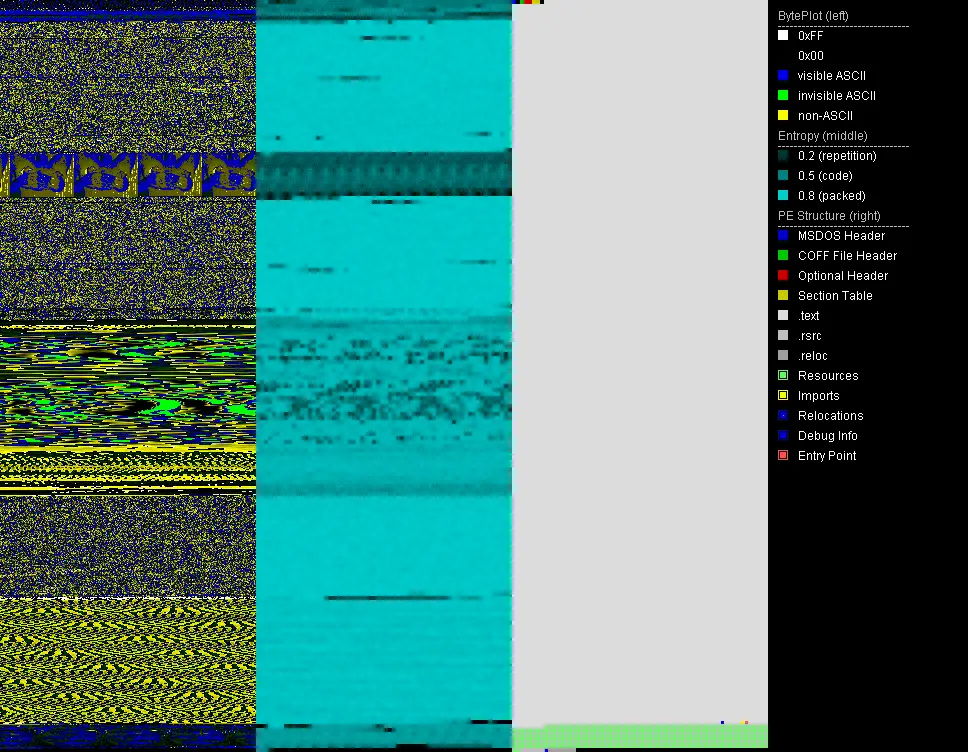
- Visualize PE file structure, local entropies and byteplot of the file with variable colors and sizes
- Calculate Shannon Entropy and Chi Squared for files and sections
- Calculate ImpHash and Rich and RichPV hash values for files and sections
- Parse RichHeader and verify checksum
- Calculate and verify Optional Header checksum
- Scan for PEiD signatures, internal file type signatures or your own signature database
- Scan for Jar to EXE wrapper (e.g. exe4j, jsmooth, jar2exe, launch4j)
- Extract Unicode and ASCII strings contained in the file
- Extraction and conversion of .ICO files from icons in the resource section
- Extraction of version information and manifest from the file
- Reading .NET metadata and streams (Alpha)
Changelog v4.0.7
Additions:
- timedatestamps added to ImportDLLs and import report
- repro debug info added, repro hash extraction
- reproducibility build checks for timestamps
Bugfixes:
- misaligned values in RichHeader caused crash
- added missing DLLCharacteristics (did these change in the last years?)
- visualizer legend not showing special sections in certain circumstances
Install & Use
Copyright 2014 Katja Hahn