
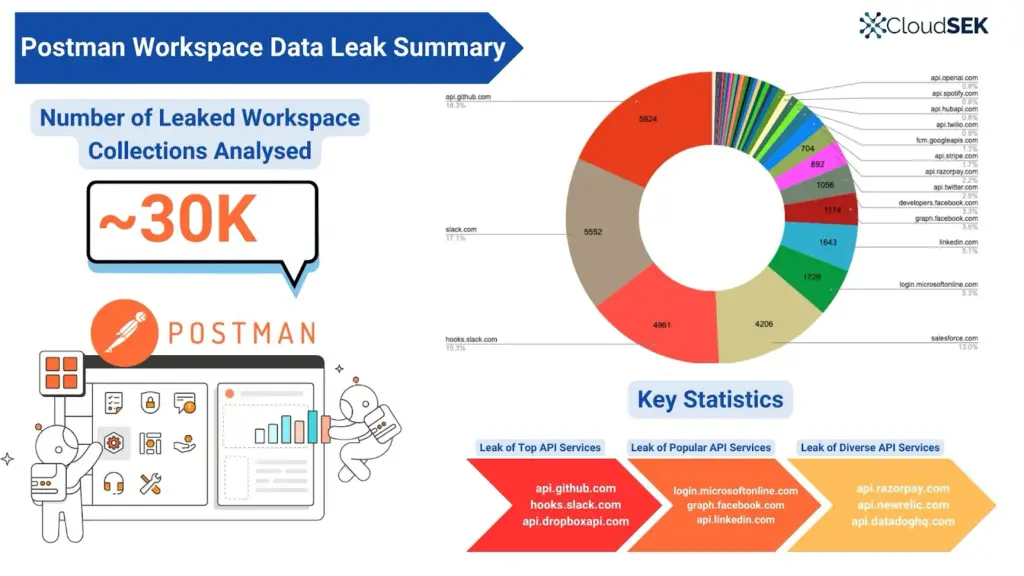
A recent report by CloudSEK’s TRIAD Team, has shed light on alarming security vulnerabilities within Postman, a popular platform for API development and testing. The investigation revealed over 30,000 publicly accessible Postman workspaces exposing sensitive information, including API keys, tokens, and confidential business data.
The year-long study, powered by CloudSEK’s XVigil platform, uncovered widespread security lapses in Postman workspaces, primarily due to misconfigured access controls and poor data handling practices. Sensitive data leaks included:
- API Keys and Tokens: Access and refresh tokens from major platforms like Razorpay, Zendesk, and New Relic, enabling unauthorized access to payment systems, CRM tools, and internal logs.
- Confidential Business Data: Leaks from private workspaces belonging to industries like healthcare and e-commerce, jeopardizing customer data and proprietary business logic.
- Sensitive Documentation: Exposed API documentation with detailed endpoints and authentication methods, increasing the attack surface for malicious actors.
“Postman environments often house sensitive data, from API keys and tokens to confidential business logic, making it a potential goldmine for malicious actors when mishandled,” the report cautioned.
The risks associated with these exposures are severe. For instance:
- Unauthorized System Access: Exposed tokens allowed attackers to log into systems with full administrative privileges, as demonstrated in the case of leaked Zendesk credentials.
- Financial Fraud: Razorpay API key leaks could lead to unauthorized transactions, financial loss, and payment system abuse.
- Reputational Damage: Misuse of exposed credentials to launch phishing campaigns or alter official content further amplifies the fallout.
One critical incident involved a public Postman workspace leaking Okta IAM API credentials for a leading athletic apparel company. According to the report, “With that access any threat actor could have accessed other internal APIs of that brand mentioned in the Postman Workspace. Due to these accesses, malicious actors could exfiltrate various invoices, trade contents, attributes, shipment details along with various commercial data.”
The report identified several common causes for these vulnerabilities:
- Inadvertent Sharing: Sensitive data embedded in shared collections and environments was accessible due to inadequate access restrictions.
- Misconfigured Access Controls: Overly permissive settings allowed unauthorized users to access critical resources.
- Public Repositories: Syncing Postman collections to public repositories like GitHub exposed secrets to anyone with access.
- Storing Sensitive Data in Plaintext: Environment variables and authentication details saved in plaintext were vulnerable to exposure.
To address these risks, CloudSEK recommends implementing robust security practices, including:
- Using Environment Variables Wisely: Avoid hardcoding sensitive information and regularly clearing variables.
- Restricting Access Permissions: Limit sharing to essential team members and regularly review permissions.
- Adopting External Secrets Management: Use tools designed to securely store and manage sensitive credentials.
- Monitoring and Logging: Leverage activity logs to audit access and detect suspicious behavior.
- Short-Lived Tokens: Replace long-lived tokens with short-lived ones to reduce potential damage in case of exposure.
Following these findings, Postman has introduced a Secret Protection Policy to enhance security in its Public API Network. The platform now proactively alerts users when secrets are detected, enabling them to resolve issues and transition to private workspaces. “These decisive measures underscore Postman’s dedication to user safety and the integrity of their Public API Network,” the report noted.
Related Posts:
- Thousands of API Secrets Exposed on Postman – Are Your Credentials At Risk?
- Google Patches Workspace Authentication Flaw, Thwarting Account Takeover Attempts
- Sophisticated Linux Malware Campaign Targets Misconfigured Cloud Services
- Evolving Cryptojacking Campaign Targets Misconfigured Kubernetes Clusters