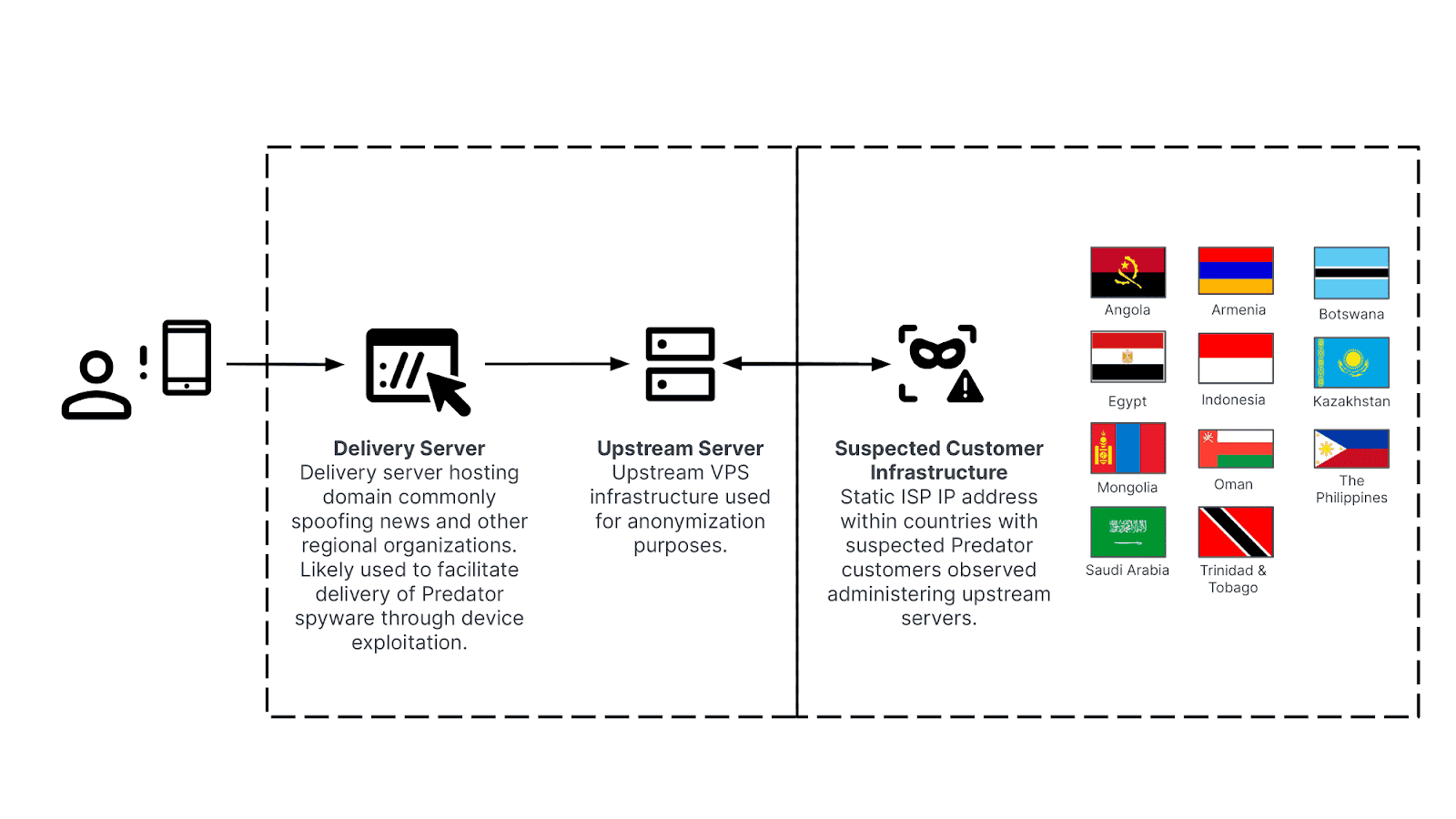
Multi-tier Predator delivery network architecture (Source: Recorded Future)
The operators behind the invasive Predator mobile spyware remain undeterred by public exposure and scrutiny. Recorded Future’s Insikt Group researchers have exposed the spyware’s rebuilt infrastructure, revealing that Predator is likely being actively used in at least eleven countries. Worryingly, this includes Botswana and the Philippines, where Predator customers were previously unknown.
Predator’s Capabilities and History of Abuse

Predator, developed by Cytrox and managed by the Intellexa alliance, has been a looming presence in the realm of mercenary spyware since 2019. This tool has found its way into at least eleven countries, including Angola, Armenia, Botswana, Egypt, Indonesia, Kazakhstan, Mongolia, Oman, the Philippines, Saudi Arabia, and Trinidad and Tobago. Designed for both Android and iOS devices, its stealthy infiltration capabilities grant it access to a device’s microphone, camera, and sensitive data without the user’s knowledge. This versatility, coupled with its elusive nature, makes Predator a formidable tool in the hands of malicious actors.
While its developers market Predator for legitimate use in counterterrorism and law enforcement, its history reveals a sinister pattern. Predator has been repeatedly linked to the targeting of journalists, politicians, activists, and other individuals deemed inconvenient or threatening by those wielding this invasive technology.
How the Spies Operate
These spyware operators use a variety of tactics to infect your phone. They might send you carefully crafted messages with malicious links or exploit vulnerabilities in your phone’s operating system. Predator mobile spyware incorporates Python-based modules allowing for seamless updates and the introduction of new functionalities without repeated exploitation. Its modus operandi involves gaining comprehensive access to the device’s data and functionalities, all while remaining virtually undetectable to the user. This level of intrusion is facilitated through a combination of “1-click” and “zero-click” attack vectors, showcasing a high degree of technical sophistication and a blatant disregard for privacy.
To maintain secrecy, the Predator network is a labyrinth of hidden servers and anonymization techniques. Spyware operators use these tools to obscure their identities, making it extremely difficult to trace the attacks back to their source.
The Mercenary Spyware Market: A Growing Threat
The persistence of Predator spyware, alongside others like NSO Group’s Pegasus, signals a worrying trend in the mercenary spyware market. This burgeoning industry poses a significant threat not just to civil society but to anyone of interest to entities wielding these espionage tools. The European Union’s resolution to curb the abuse of spyware among member states is a step in the right direction, yet the global nature of this challenge calls for a more concerted international effort.
In the face of this invisible menace, Insikt Group recommends a multi-faceted approach to defense. Regular updates, device reboots, the use of lockdown modes, and the separation of personal and corporate devices are just the beginning. Organizations must foster a culture of security awareness, and minimal data exposure, and adopt dynamic security policies.