Preventing Mimikatz steal Windows system password
Introduction to Mimikatz
Mimikatz is an tool that can get memory from Windows and get plain text passwords and NTLM hash values. This article will show you how to get the password for this software.
Mimikatz is a tool that can get memory from a Windows Certified (LSASS) process and get a plaintext password and an NTLM hash value. An attacker can take a roaming inner network. They can pass the plaintext password or pass a hash value to mention. Maybe many people will ask, “Do not you think about how to defend Microsoft?”
Defensive measures
Step 1: Active Directory 2012 R2 functional level
First you can upgrade your domain or forest functional level to 2012 R2. This level adds a “protected user” user group. If you have seen TechNet on its introduction, you may feel that this user group will prevent mimikatz from getting the password. What is the actual situation?
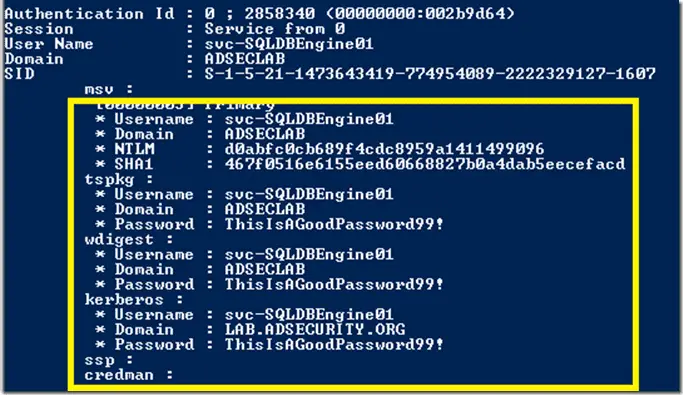
Note: For non-protected users, mimikatz is available to NTLM hashes.
And when the user is added to the protection of the user group, NTLM hash and plaintext password can not see.
Obviously, this trick is very useful, that Windows 7 or 2008 R2 on the protection of the user group is what?
It can be seen that even if a protected user group is added, passwords and hashes are visible.
But this machine has not played a patch. In fact, if the computer does not know what to protect the user group, then this user group will lose its meaning. Fortunately, Microsoft has this Windows8.1 and 2012R2 some functions ported to the old version of the Windows.
Step 2: Install KB2871997
If you have been installing Windows Update, KB2871997 should have been installed. This update will migrate the functionality of the protection user group to the older version of Windows. Once the installation of this update, Windows2008 R2 can also control the mimikatz.
Install KB2871997 update does not put the user into the protection of the user group is such an effect
And once joined the protection of the user group, the effect just like 2012 R2 on the same
Step 3: Remove the memory
This step is optional, because you may want to put all the accounts into the protection of the user group inside, but in fact not. Microsoft objected to the computer account and service account into the protection of the user group inside. So this step is for those who are not in the protection of the user group inside the user.
On Windows 2012 R2, mimikatz did not get the password, whether or not the user has been added to the protected user group, and Windows 2000, if not added to the protection of the user group, mimikatz still able to obtain the password.
The password is stored by a registry setting. As with the protection of user groups, in the new version of Windows (8.1+ & 2012R2 +), passwords are not stored in memory by default. This feature is also in the KB2871997 update was transplanted to the old version. However, due to compatibility reasons, after the installation of the update, the old version will still be stored in memory by default password. You just put the registry “UseLogonCredential” item set to 0 just fine.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\WDigest
This user has not been added to the protected user group, but the value of the registry has been changed, so Mimikatz can not get the plaintext password.




