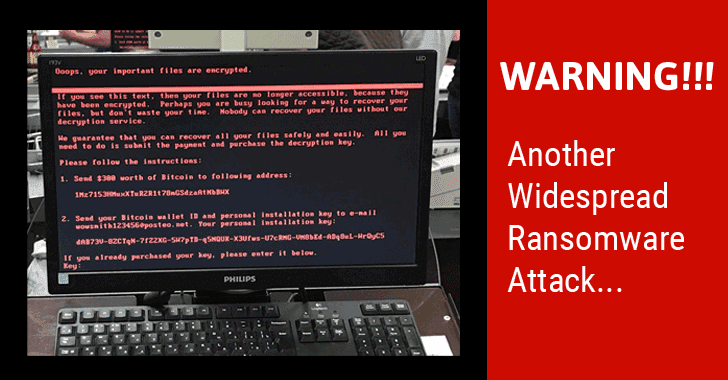
June 28, according to foreign media news, Ukraine and other countries are experiencing Petya blackmail virus attacks, government, banks and other important systems affected by the attack. The hacker is using the Petya blackmail variant Petwarp, using the same attack and WannaCry. National Internet Emergency Center today issued a warning notice.
The National Internet Emergency Response Center said that through the event tracking analysis found that the virus in the attack event belongs to the Petya blackmail variant Petwrap, the virus using the Microsoft Office / WordPad remote code execution vulnerability (CVE-2017-0199) by e-mail, After the success of the use of the eternal blue loopholes in the network to find open 445 port host to spread.
According to the statistical analysis of safety vendors Kaspersky researchers, the world’s main infected countries include Ukraine, Russia, Poland, Italy, Germany, and Belarus.
How to prevent Petya Ransomware
1. Do not easily click on unknown attachments, especially rtf, doc and other format files.
2. There is a network using the same account, password situation, please change the password as soon as possible, do not boot the computer, please confirm the password is completed, patch installation is complete and then boot operation.
3. Update the operating system patch (MS)
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
4. Update the Microsoft Office / WordPad Remote Code Execution Vulnerability – CVE -2017-0199 patch
https://technet.microsoft.com/en-us/office/mt465751.aspx
5. Disable the WMI service
https://msdn.microsoft.com/en-us/library/aa826517(v=vs.85).aspx