
NoName057(16) public attack announcement on Telegram | Image: NETSCOUT
Japan has become the latest target of pro-Russian hacktivists following the country’s move towards increased military cooperation with the US. According to a new report from cybersecurity researcher Marcin Nawrocki at NETSCOUT, two prominent pro-Russian threat actors, NoName057(16) and the Russian Cyber Army Team, launched a coordinated DDoS attack campaign against Japanese organizations on October 14th, 2024.
This offensive comes in the wake of “Japan’s call for increased participation in US-led military alliances,” as stated in the report. The attacks appear to be a direct response to an interview published by the Ministry of Foreign Affairs of the Russian Federation (MID) on October 11th, 2024, expressing concerns over Japan’s “rising defense budget, development of pre-emptive strike capabilities, and involvement in US-led military exercises and joint ballistic missile-defense research and cooperation.”
The DDoS attacks have primarily targeted organizations in the logistics and manufacturing sectors, with a particular focus on harbors and shipbuilding. Government, political, and social organizations have also been hit, including the political party of Japan’s newly elected prime minister. The report suggests that these high-profile targets were chosen to “generate significant publicity.”
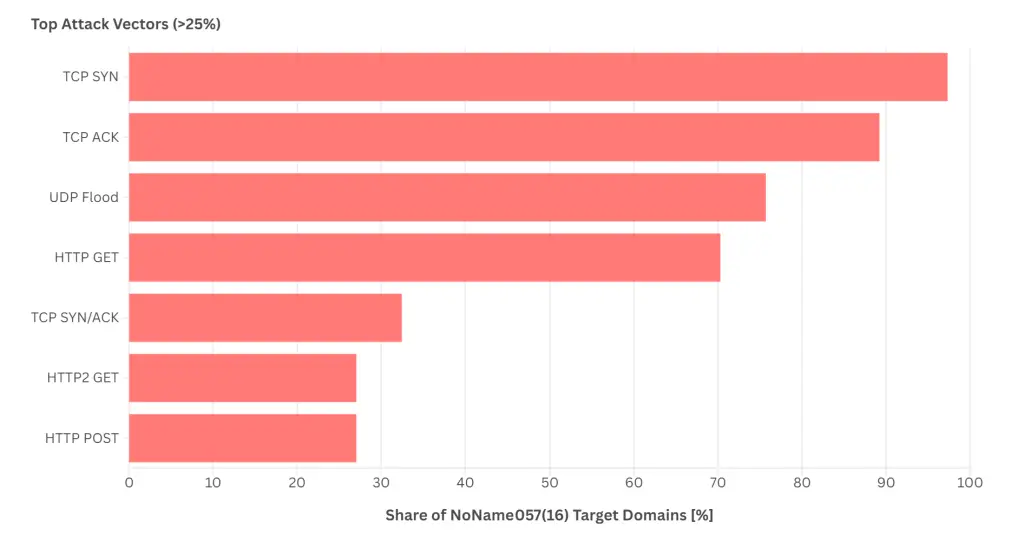
Nawrocki’s analysis reveals a sophisticated and multi-faceted attack strategy. “NoName057(16) is pushing the limits of its DDoSia botnet’s capabilities, employing a wide range of direct-path attack vectors against multiple targets,” the report states. These vectors include various types of TCP packet-flooding, with TCP SYN-floods being the most common, as well as HTTP-based attacks.
Interestingly, the report notes a pattern in the timing of the attacks. “All new C2 server updates occurring between 07:00 and 13:00 UTC (16:00 to 22:00 in Japan, UTC+9), which corresponds to typical working hours for the presumably Russian group.”
While these attacks are impactful, NETSCOUT assures that they haven’t significantly disrupted the overall threat landscape in the region. “NETSCOUT observes approximately 2,000 DDoS attacks targeting Japanese networks daily,” the report explains.
However, the incident serves as a stark reminder of the growing use of cyber warfare tactics in geopolitical conflicts. As the report concludes, “as DDoS attacks continue to affect organizations globally, implementing robust detection and mitigation strategies remains crucial for maintaining digital availability.”
Related Posts:
- NoName057(16): Russia’s DDoS Disruptors Target the West
- The United States and Ukraine carry out large-scale cybersecurity cooperation
- Operation Japan’s Cyber Response to Fukushima Decision