probeSniffer: tool for sniffing unencrypted wireless probe requests
probeSniffer
A tool for sniffing unencrypted wireless probe requests from devices.
new in 3.0:
- Less packet drop
- Offline / Faster vendor resolving
- Way better performance on slower systems
- Switching from scapy to tshark packet capture
- Displaying / Logging BSSID’s from probe requests (only if not broadcast)
Features:
- Capturing and displaying probe requests real-time
- Offline vendor resolving from MAC addresses
- Displaying the number of devices nearby
- Displaying the RSSIs of probe requests
- Settable nicknames for mac addresses
- Option to filter output by mac address
- Displaying BSSIDs from probe requests
- Capturing ‘broadcast’ probe requests (without ssid)
- Logging the probe requests to an SQLite database file
Requirements:
- Kali Linux / Raspbian with root privileges
- Python3 & pip3 & tshark & pyshark
- A wireless card (capable for monitor mode)
Installing
$ sudo apt-get update && sudo apt-get install python3 python3-pip tshark -y
$ git clone https://github.com/xdavidhu/probeSniffer
$ cd probeSniffer/
$ python3 -m pip install -r requirements.txt
Usage
Make sure to put your interface into monitor mode before!
$ sudo python3 probeSniffer.py [monitor-mode-interface] [options]
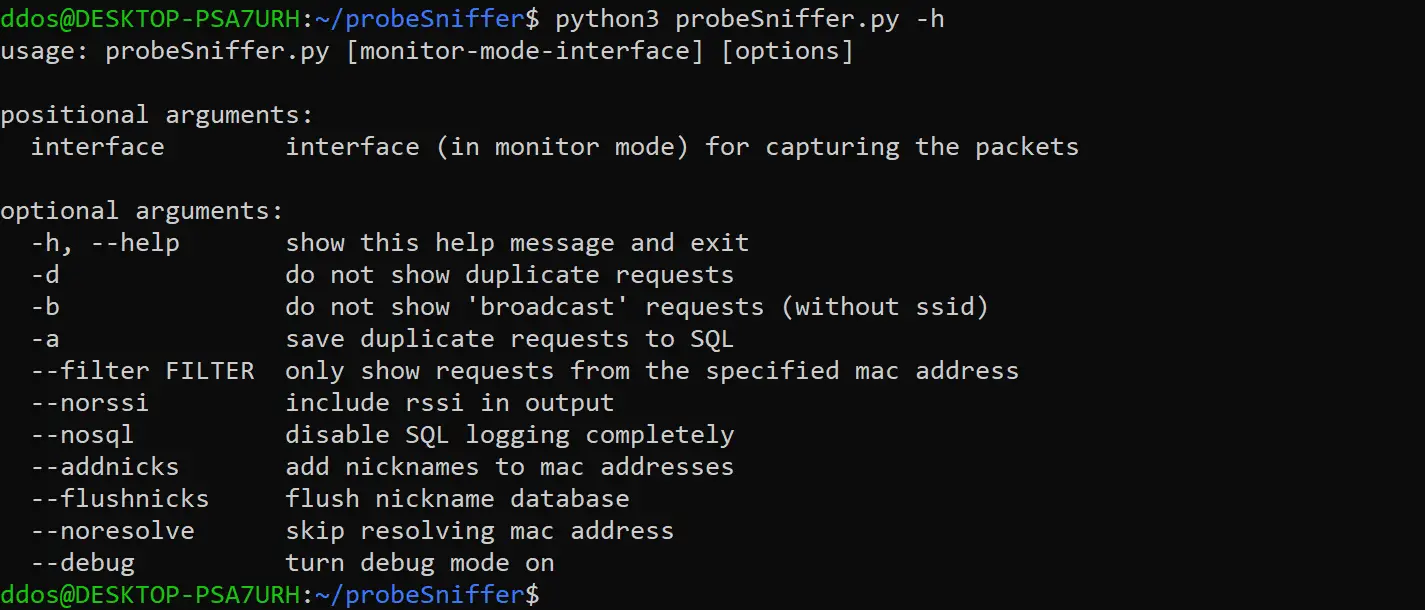
Options
- -h / display the help message
- -d / do not show duplicate requests
- -b / do not show ‘broadcast’ requests (without ssid)
- -a / save duplicate requests to SQL
- –filter / only show requests from the specified mac address
- –norssi / do not include RSSI in output
- –nosql / disable SQL logging completely
- –addnicks / add nicknames to mac addresses
- –flushnicks / flush nickname database
- –noresolve / skip resolving mac address
- –debug / turn debug mode on
Copyright (c) 2017 David Schütz
Source: https://github.com/xdavidhu



