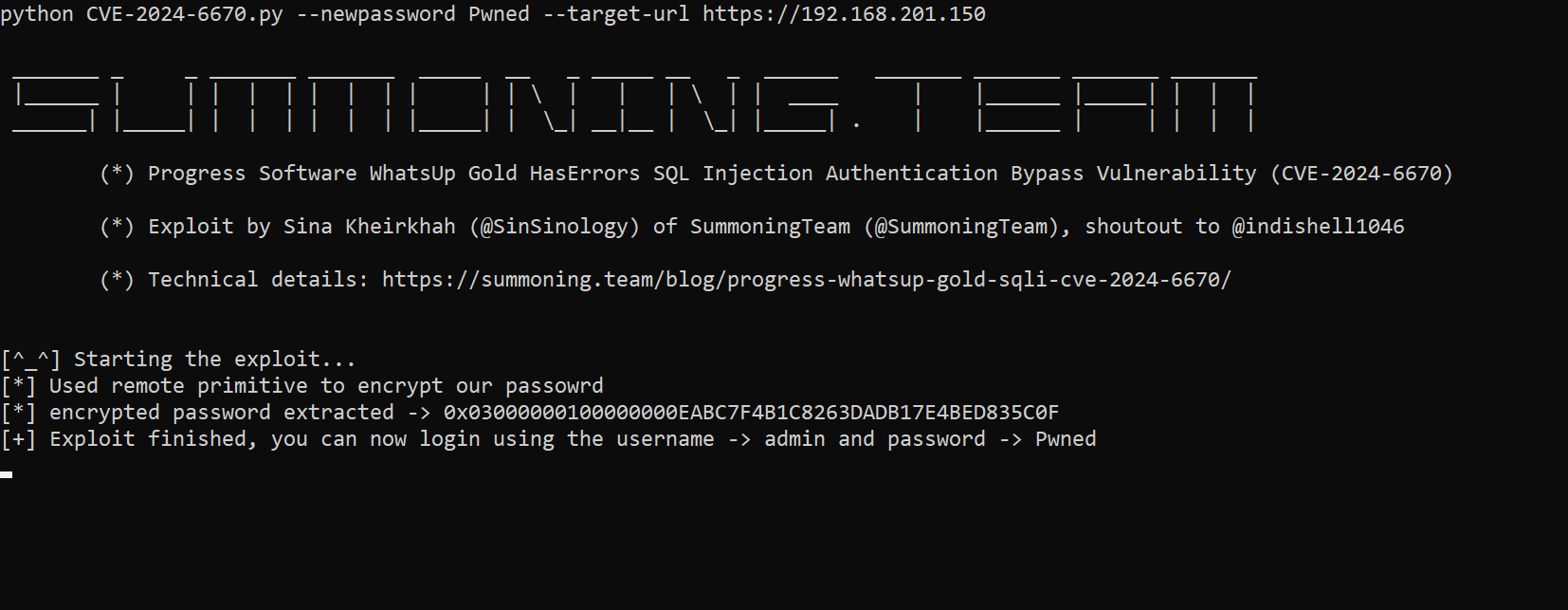
Researcher Sina Kheirkhah of the Summoning Team has published the technical details and a proof-of-concept (PoC) exploit for a critical vulnerability, identified as CVE-2024-6670, affecting Progress Software’s WhatsUp Gold. With a CVSS score of 9.8, this flaw presents a severe risk, allowing remote attackers to bypass authentication without any prior credentials.
The CVE-2024-6670 vulnerability resides within the HasErrors method of WhatsUp Gold, a popular network monitoring tool used by organizations to manage and monitor their IT infrastructure. The vulnerability stems from the improper validation of user-supplied input before it is used to construct SQL queries. This oversight enables attackers to manipulate the input, bypassing the system’s authentication mechanisms entirely.
The flaw is particularly dangerous because it requires no prior authentication or special privileges to exploit. An attacker only needs to craft a malicious string and send it to the vulnerable application, effectively granting them unauthorized access to the system.
Kheirkhah, who has detailed the technical aspects of the CVE-2024-6670 vulnerability on his blog, also provided a proof-of-concept (PoC) exploit, which is now publicly available on GitHub. The PoC demonstrates how easily this vulnerability can be exploited, raising concerns about the potential for widespread abuse.
If successfully exploited, an attacker could gain full access to WhatsUp Gold, potentially leading to the manipulation of network monitoring data, unauthorized access to sensitive information, or further exploitation of the network infrastructure managed by the software.
Progress Software has released a fix for this critical vulnerability in WhatsUp Gold version 2024.0.0. Organizations using older versions of WhatsUp Gold are strongly urged to upgrade their systems immediately to mitigate the risk of unauthorized access and potential data breaches.
Related Posts:
- Critical Vulnerabilities in Progress WhatsUp Gold Demand Immediate Action
- Critical Vulnerabilities Uncovered in Progress WhatsUp Gold (CVE-2024-6670 & CVE-2024-6671)
- Bitcoin Gold Hacked: Lose $18 Million