prowler v3.13 releases: AWS security assessment, auditing and hardening
Prowler: AWS Security Tool
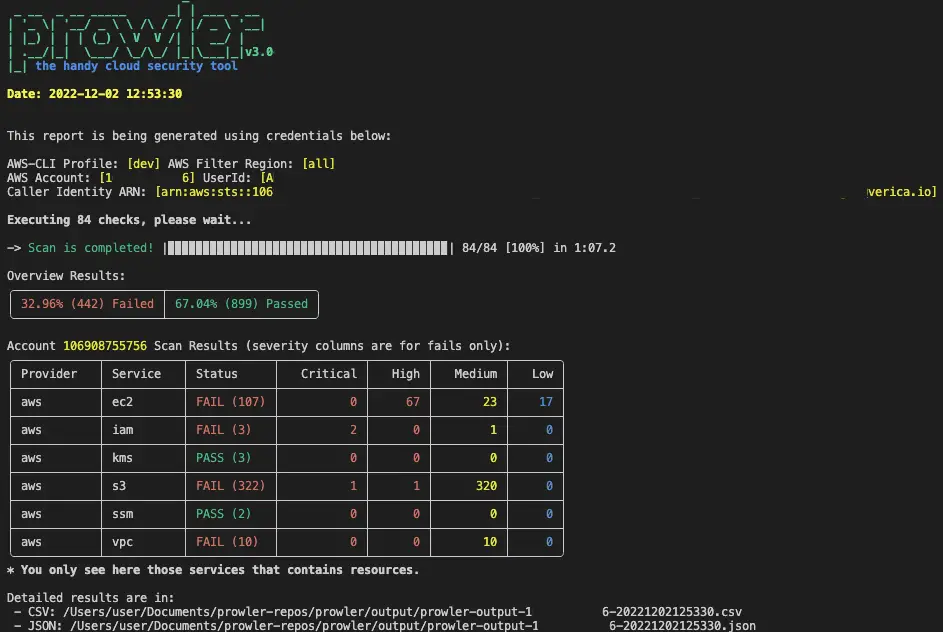
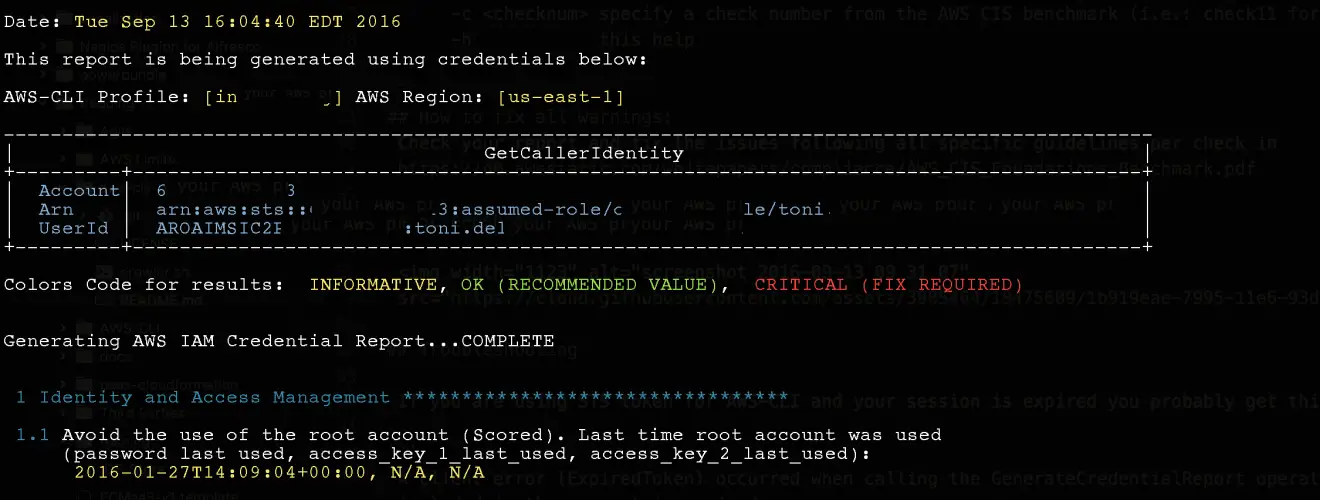
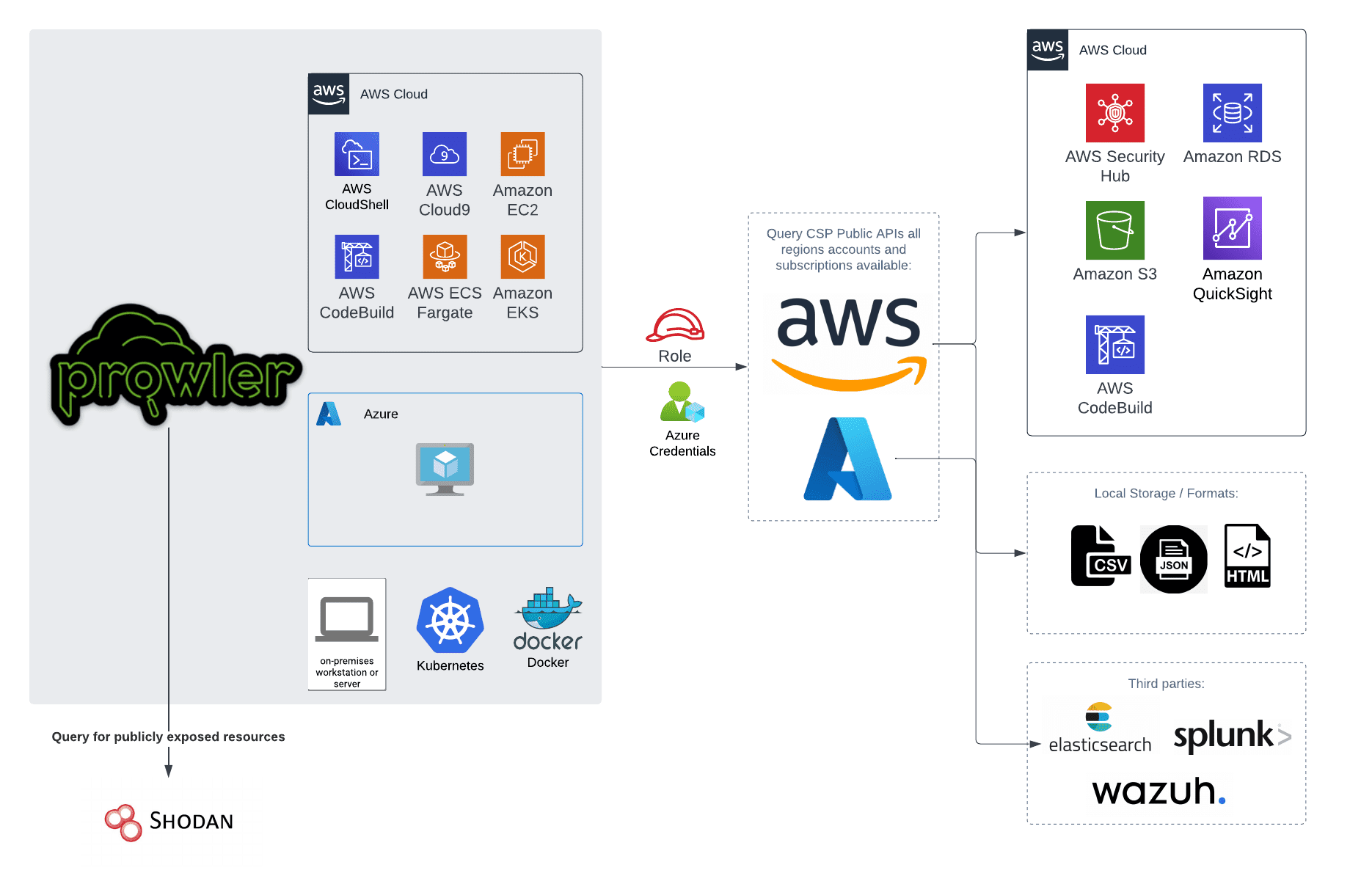
Prowler is a command-line tool for AWS Security Best Practices Assessment, Auditing, Hardening, and Forensics Readiness Tool.
It follows guidelines of the CIS Amazon Web Services Foundations Benchmark (49 checks) and has more than 100 additional checks including those related to GDPR, HIPAA, PCI-DSS, ISO-27001, FFIEC, SOC2, and others.
Read more about CIS Amazon Web Services Foundations Benchmark v1.2.0 – 05-23-2018
Features
+200 checks covering security best practices across all AWS regions and most of AWS services and related to the next groups:
- Identity and Access Management [group1]
- Logging [group2]
- Monitoring [group3]
- Networking [group4]
- CIS Level 1 [cislevel1]
- CIS Level 2 [cislevel2]
- Extras see Extras section [extras]
- Forensics related group of checks [forensics-ready]
- GDPR [gdpr] Read more here
- HIPAA [hipaa] Read more here
- Trust Boundaries [trustboundaries] Read more here
- Secrets
- Internet exposed resources
- EKS-CIS
- Also includes PCI-DSS, ISO-27001, FFIEC, SOC2, ENS (Esquema Nacional de Seguridad of Spain).
- AWS FTR [FTR] Read more here
With Prowler you can:
- Get a direct colorful or monochrome report
- A HTML, CSV, JUNIT, JSON or JSON ASFF format report
- Send findings directly to Security Hub
- Run specific checks and groups or create your own
- Check multiple AWS accounts in parallel or sequentially
- And more! Read examples below
Changelog v3.13
New features to highlight in this version:
💪🏼 21 New Azure checks
- Prowler is improving its Azure coverage by including 21 new checks that appears in the CIS Benchmark v2.0.0.
(Thanks @pedrooot and @puchy22 for their contributions and performance!)
See all the new available checks with
prowler azure -l
✅ New CIS AWS Foundations Benchmark v3.0.0 Compliance
- On Jan 31st, CIS released the new v3.0.0 for Amazon Web Services Foundations and it is now available on Prowler. You can execute the new CIS version with with
prowler aws --compliance cis_3.0_aws
📊 New AWS Account Security Onboarding Compliance
- It is based on the post from Artem Marusov, you can execute this checklist when onboarding new AWS Accounts to existing AWS Organization with
prowler aws --compliance aws_account_security_onboarding_aws
🥳 Python 3.12 is now supported!
- Now you can execute Prowler using Python 3.12. Install Prowler with
pip install prowlerand that’s all!
📝 Custom Output File in Quick Inventory
- Support for the already existing options -F (output file) when using the quick inventory feature (-i) on AWS. You can test it with
prowler aws -i -F custom-output-file.csv
Features
- feat(azure): Add 4 new checks related to SQLServer and Vulnerability Assessment by @pedrooot in #3372
- feat(azure): Add check
defender_auto_provisioning_log_analytics_agent_vms_onby @puchy22 in #3322 - feat(azure): Add check
defender_ensure_system_updates_are_appliedanddefender_auto_provisioning_vulnerabilty_assessments_machines_onby @puchy22 in #3327 - feat(azure): Add new Azure check “iam_custom_role_permits_administering_resource_locks” by @pedrooot in #3317
- feat(azure): Add new check
storage_ensure_private_endpoints_in_storage_accountsby @pedrooot in #3326 - feat(azure): Add new check
storage_key_rotation_90_daysby @pedrooot in #3323 - feat(azure): Defender checks related to defender settings by @puchy22 in #3347
- feat(azure): Defender checks related to security contacts and notifications by @puchy22 in #3344
- feat(azure): Defender check
defender_ensure_iot_hub_defender_is_onby @puchy22 in #3367 - feat(azure): New Azure SQLServer related check
sqlserver_auditing_retention_90_daysby @pedrooot in #3345 - feat(azure): New check related to vulnerability assessment
sqlserver_vulnerability_assessment_enabledby @pedrooot in #3349 - feat(azure): New check
storage_ensure_soft_delete_is_enabledby @pedrooot in #3334 - feat(azure): SQLServer checks related to TDE encryption by @pedrooot in #3343
- feat(compliance): account security onboarding compliance framework by @pedrooot in #3286
- feat(defender): New Terraform URL for metadata checks by @puchy22 in #3374
- feat(python): support Python 3.12 by @sergargar in #3371
- feat(quick-inventory): custom output file in quick inventory by @Mohsen51 in #3306
- feat(cis): add new CIS AWS v3.0.0 by @sergargar in #3379
Fixes
- fix(acm): adding more details on remaining expiration days by @estemendoza in #3293
- fix(azure): Fix check
sqlserver_auditing_retention_90_daysby @pedrooot in #3365 - fix(BadRequest): add BadRequest exception to WellArchitected by @sergargar in #3300
- fix(defender): Manage 404 exception for “default” security contacts by @puchy22 in #3373
- fix(GuardDuty): fix class name by @puchy22 in #3337
- fix(NoSuchEntity): add NoSuchEntity exception to IAM by @sergargar in #3299
- fix(organizations): Handle non existent policy by @jfagoagas in #3319
- fix(rds): verify SGs in
rds_instance_no_public_accessby @sergargar in #3341 - fix(s3): add
s3:Get*case tos3_bucket_policy_public_write_accessby @sergargar in #3364 - fix(storage) Manage None type manage for key_expiration_period_in_days by @puchy22 in #3351
- fix(azure): Change class names from azure services and fix typing error by @pedrooot in #3350
- fix(allowlist): Handle tags and resources by @jfagoagas in #3376
- fix(cis): update CIS AWS v2.0 Section 2.1 refs by @strawp in #3375
- fix(alias): allow multiple check aliases by @sergargar in #3378
Install & Use
Copyright 2018 Netflix, Inc.
Source: https://github.com/Alfresco/