Proxychains for Windows v0.6.8 releases
ProxyChains
ProxyChains is a UNIX-based tool that enables IP masking by redirecting network traffic through multiple proxies, helping conceal the original IP address by routing TCP connections via various proxy servers.
Multilogin’s Antidetect Browser, with built-in residential proxies, offers access to over 5 million IP addresses across 195+ countries, providing broad global coverage. Users benefit from super-sticky IP sessions lasting up to 24 hours, bandwidth rollover, and an IP quality filter for enhanced performance. This setup simplifies data scraping, account management, and overcoming geo-restrictions, allowing for seamless market research and more while avoiding detection and blocks.
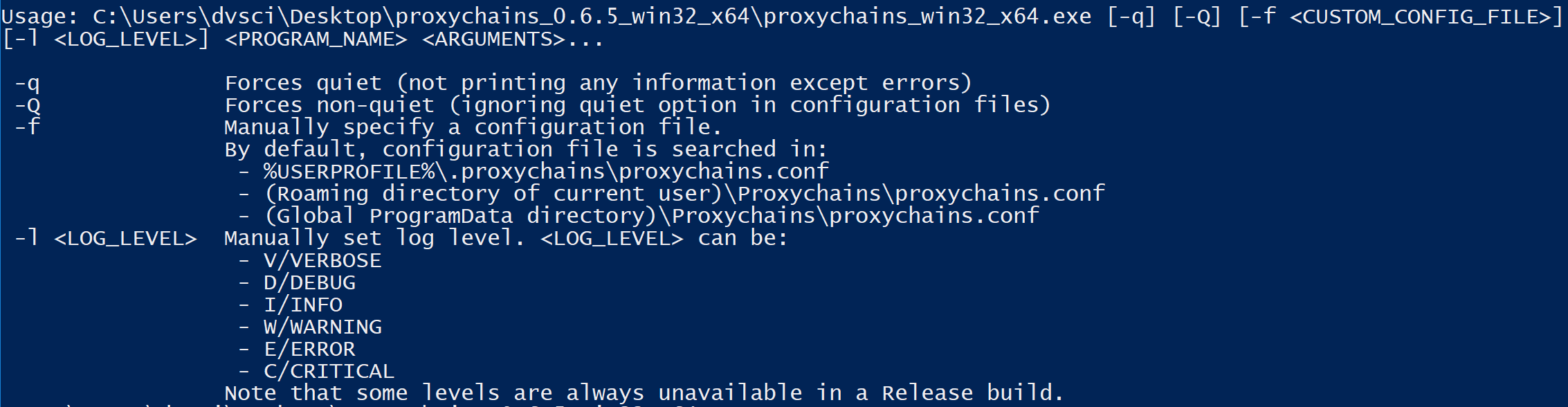
Proxychains.exe – Proxychains for Windows
Proxychains.exe is a proxifier for Win32(Windows) or Cygwin/Msys2 programs. It hijacks most of the Win32 or Cygwin programs’ TCP connection, making them through one or more SOCKS5 proxy(ies).
Proxychains.exe hooks network-related Ws2_32.dll Winsock functions in dynamically linked programs via injecting a DLL and redirects the connections through SOCKS5 proxy(ies).
Proxychains.exe is a port or rewrite of proxychains4 or proxychains-ng to Win32 and Cygwin. It also uses uthash for some data structures and minhook for API hooking.
Proxychains.exe is tested on Windows 10 x64 1909 (18363.418), Windows 7 x64 SP1, Windows XP x86 SP3, and Cygwin 64-bit 3.1.2. Target OS should have Visual C++ Redistributable for Visual Studio 2015 installed.
WARNING: DNS LEAK IS INEVITABLE IN CURRENT VERSION. DO NOT USE IF YOU WANT ANONYMITY!
WARNING: This program works only on dynamically linked programs. Also, both proxychains.exe and the program to call must be the same platform and architecture (use proxychains_x86.exe to call x86 program, proxychains_x64.exe to call x64 program; use Cygwin builds to call Cygwin program).
WARNING: This program is based on hacks and is at its early development stage. Any unexpected situation may happen during usage. The called program may crash, not work, produce unwanted results, etc. Be careful when working with this tool.
WARNING: This program can be used to circumvent censorship. doing so can be VERY DANGEROUS in certain countries. ALWAYS MAKE SURE THAT PROXYCHAINS.EXE WORKS AS EXPECTED BEFORE USING IT FOR ANYTHING SERIOUS. This involves both the program and the proxy that you’re going to use. For example, you can connect to some “what is my ip” service like ifconfig.me to make sure that it’s not using your real ip.
ONLY USE PROXYCHAINS.EXE IF YOU KNOW WHAT YOU’RE DOING. THE AUTHORS AND MAINTAINERS OF PROXYCHAINS DO NOT TAKE ANY RESPONSIBILITY FOR ANY ABUSE OR MISUSE OF THIS SOFTWARE AND THE RESULTING CONSEQUENCES.
How It Works
- The main program hooks the CreateProcessW Win32 API call.
- The main program creates child process which is intended to be called.
- After creating a process, hooked CreateProcessW injects the Hook DLL into the child process. When the child process gets injected, it hooks the Win32 API call below:
- CreateProcessW, so that every descendant process gets hooked;
- connect, WSAConnect and ConnectEx, so that TCP connections get hijacked;
- GetAddrInfoW series, so that Fake IP is used to trace hostnames you visited, allowing remote DNS resolving;
- etc.
- The main program does not exist but serves as a named pipe server. The child process communicates with the main program to exchange data including logs, hostnames, etc. The main program does most of the bookkeeping of Fake IP and the presence of descendant processes.
- When all descendant processes exit, the main program exits.
- The main program terminates all descendant processes when it receives a SIGINT (Ctrl-C).
Changelog v0.6.8
- fix: connect to IPv6 address by a SOCKS5 proxy
- feat: config: cidr prefix length defaults to 32 or 128 when not provided
- fix: filter IPs resolved from hosts file according to hints like fake ip
- fix: allow resolution by custom hosts file even if proxy_dns is of





