PSDecode v5.1 releases: deobfuscating encoded PowerShell scripts
PSDecode
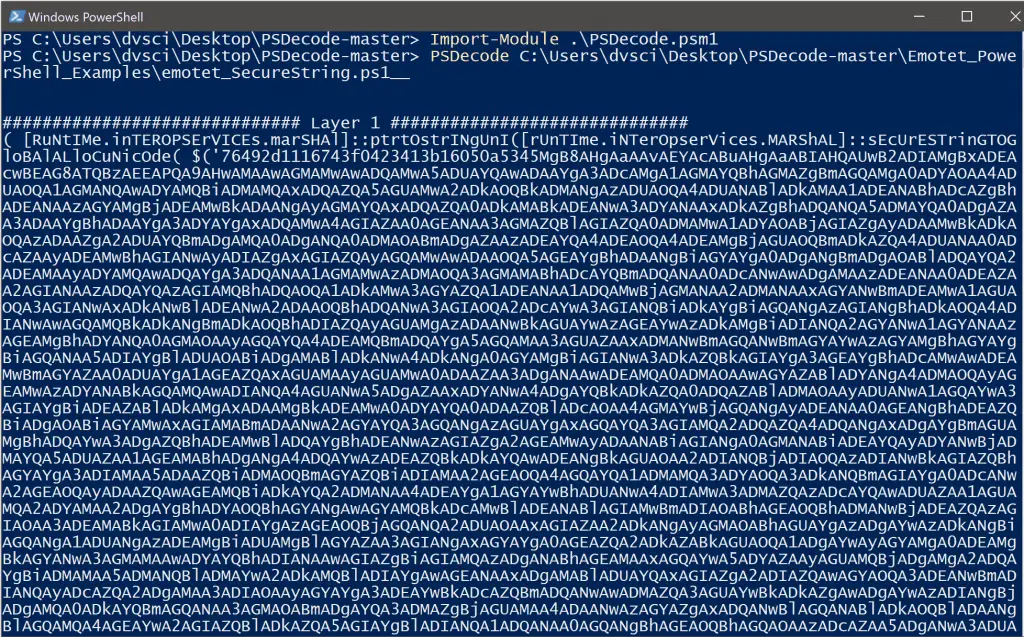
This is a PowerShell script for deobfuscating other encoded PowerShell scripts. Often, malicious PowerShell scripts have several layers of encodings (Replace, Base64Decode, etc…) that, once decoded, are executed via a call to Invoke-Expression (IEX, &, .), Invoke-Command, etc… This script employs a technique called method overriding that enables us to essentially intercept calls to functions that I have accounted for within this script and print out the arguments being passed to it (a.k.a what the script was trying to execute).
** Important Note #1: Only run this script within an isolated sandbox. If the encoded PowerShell attempts to execute a function which I have not accounted for, there is a chance it could execute**
** Important Note #2: The default execution policy for PowerShell is Restricted and if you don’t use PowerShell a lot, chances are when you go running this script, it will give you an error stating “PSDecode cannot be loaded because the execution of scripts is disabled on this system”. If you receive this message, you’ll need to change your execution policy to Unrestricted either temporarily or permanently. The simplest way is to open a PowerShell command prompt as Administrator and run: set-executionpolicy unrestricted**
Changelog v5.1
- Bug Fix: Changed encoded command length check to write to temp file if length of encoded command is less than 8k bytes. The previous value (12190) referred to the max length of script blocks permitted by PowerShell. However, for Windows XP+, the max command-line length is 8191 bytes, which is the value that should be respected. Issue #12
Download
git clone https://github.com/R3MRUM/PSDecode.git
Use
- Copy PSDecode.psm1 into $PSHome\Modules\
- Open a new instance of PowerShell
- Option #1 [Pass encoded PowerShell via File]:
> PSDecode .\encoded_ps.ps1
or if the malicious script is Unicode:
> PSDecode .\uencoded_ps.ps1 -u
- Option #2 [Pass encoded PowerShell via PIPE]:
> Get-Content .\encoded_ps.ps1 | PSDecode

Optional Parameter
-u: Default file encoding expected is ASCII. This switch tells PSDecode that the script being decoded is Unicode encoded.
Example Powershell Scripts
In this repository, I’ve included Emotet_PowerShell_Examples.zip, which contains a few different LIVE emotet PowerShell scripts. You can use these to play around with PSDecode and get a better understanding of how it is supposed to function. It is important to note that these examples are malicious and could potentially result in an infection if handled improperly. These are provided for educational purposes only and I assume no responsibility for what you do with them. You’ve been warned.
The password for the archive is: infected
Copyright (C) 2017 R3MRUM
Source: https://github.com/R3MRUM/