PwnAuth: web application framework for launching and managing OAuth abuse campaigns
PwnAuth
A web application framework for launching and managing OAuth abuse campaigns.
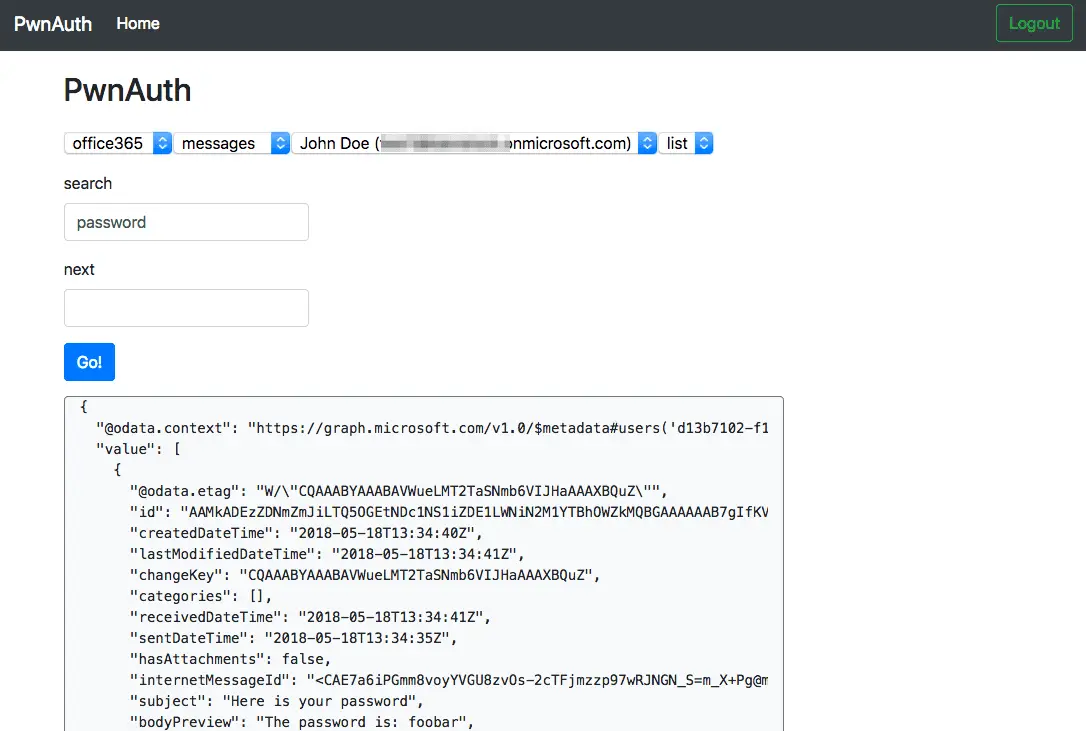
Image: FireEye
Minimum requirements
- An Internet-accessible server (tested running Ubuntu 16.04)
- Nginx
- Docker (apt install docker.io)
- Docker-Compose (newest version from docker website)
- A Valid SSL certificate
Installation
- Clone the repository onto your server: git clone https://github.com/fireeye/PwnAuth.git
- Inside
Dockerfilecustomize the settings to your site:- Change
DJANGO_SITEto match the FQDN or IP address you will use to access the PwnAuth App. - Change the
SECRET_KEYto a new random value. - Set
DJANGO_ENVtoprodordevdepending on if you are in production or not.
- Change
- Configure your SSL certificates and NGINX. I have provided a sample NGINX configuration in
nginx/oauth.conf - Run
setup.shas root. This will build the docker services for the OAuth application as well as set up an initial Django administrator for you to use the application with. - Login to the app. Navigate to
/auth/loginin your browser to log in to the application with the account you just created.
Modules
PwnAuth is designed to be modular. A new Identity Provider can easily be supported by developing the necessary database models and views to interact with the Resource Server. As long as you follow the module implementation guidelines, the GUI will automatically detect the module and it will be ready for use.
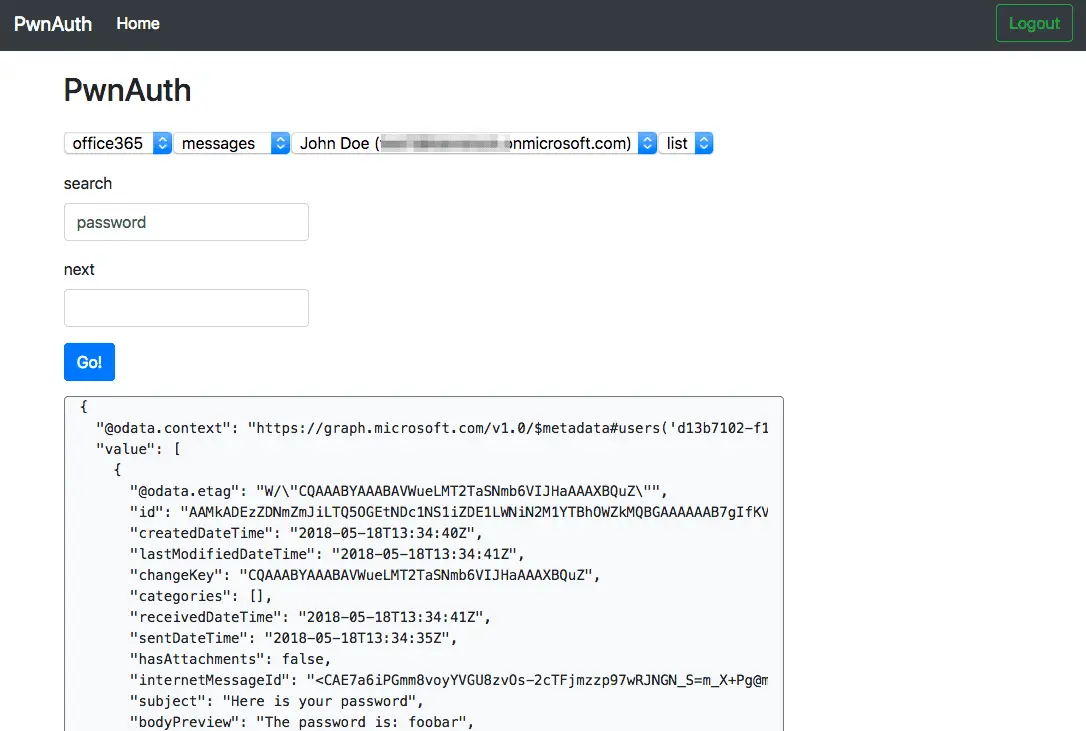
Office 365
- You must create a new OAuth application with Microsoft at the Microsoft App Portal
- You must create a “Web” platform with a proper Redirect URL. The default configuration for PwnAuth is
/oauth/api/microsoft/callback - Be sure to create a secret key and ensure your scopes include
user.readandoffline_access - Import the application settings into the application using the GUI
- Send out your phishing emails using the authorization_url_full link and wait for responses!
Usage
PwnAuth is designed to have interacted with an inside of a browser. There is also an API available for power users. To learn more about using PwnAuth see the wiki.
Logging
Logs are written to /var/log/oauth on your host system where docker is running. The audit log records all actions taken in the application and by whom.
Detection
Detection can be quite difficult due to the limited amount of information on these applications that are exposed. In general, the best bet is to hunt for specific scopes that would be suspicious (i.e. offline access, sending/reading of mail) as well as apps that have to redirect URLs (the URL that receives the token) that are strange. This issue is further compounded by a large number of “legitimate” applications out there that request incredibly wide scopes.
Copyright 2018 FireEye, Inc.
Source: https://github.com/fireeye/