Security researchers at F5 Networks have discovered a new Linux encrypted botnet and named it “PyCryptoMiner,” whose main target is a Linux system with a public SSH port.
According to the researchers, PyCryptoMiner mainly includes the following five features:
- Based on the Python scripting language, this means hard to detect
- Receives a new C & C server allocation using Pastebin [.] Com (under the username “WHATHAPPEN”) when the original Command and Control (C & C) server is not available
- Domain registrants are associated with more than 36,000 domain names, some of which have been known for fraud, gambling and adult services since 2012
- Was used to mine Monero, a cryptocurrency favored by cybercriminals and highly anonymous. As of late December 2017, PyCryptoMiner has mined Monroe, worth about $ 46,000
- Leverage CVE-2017-12149 Vulnerability, Introducing New Scanning Features for Vulnerable JBoss Servers in Mid-December
Unlike binary malware alternatives, Python-based scripting languages make PyCryptoMiner more confusing and more averse. In addition, it is executed by a legitimate binary.
PyCryptoMiner propagates by trying to guess the SSH login credentials of the target Linux device and if successful, it will deploy a simple base64-encoded Python script for connecting to the C & C server to download and execute additional Python code.
This Python script also collects information about infected devices, including the host / DNS name, operating system name and architecture, CPU count, and CPU usage, and it also checks if the device is already infected and if the infected device is used Monroe dig or scan.
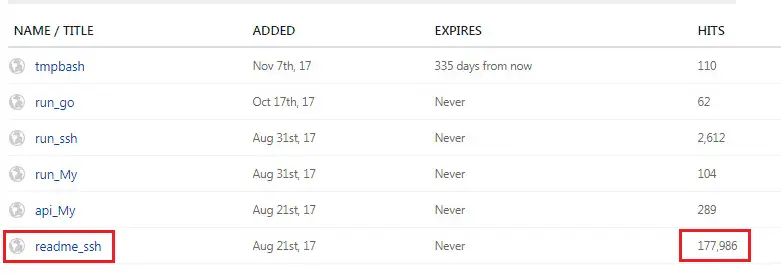
The researchers confirmed through the information provided on the Pastebin [.] Com page that PyCryptoMiner may have been launched as of August 2017. In the survey, the resource has been viewed 177987 times, and about 1000 times a day will be added.
When querying the domain name “zsw8.cc” of these C & C servers, the registrant name was found to be “xinqian Rhys”
Domain registrants are associated with more than 36,000 domain names, some of which have been known for fraud, gambling and adult services since 2012.
PyCryptoMiner uses two wallet addresses, 94 and 64 Monroe respectively, worth about $46,000
Source: f5.com