Python NodeStealer Evolution: Targeting Facebook Ads Manager and Credit Cards

The ever-evolving Python NodeStealer has resurfaced with advanced techniques and a broader target range, as detailed in the latest report by Jan Michael Alcantara of Netskope Threat Labs. Initially known for targeting Facebook business accounts, this infostealer now sets its sights on Facebook Ads Manager and credit card information, showcasing an alarming level of sophistication.
NodeStealer continues to prey on Facebook credentials but has added a new layer to its operations. By targeting Facebook Ads Manager accounts, the malware collects login details, cookies, and crucial budget information using Facebook’s Graph API. The report explains that attackers “generate an access token by logging into adsmanager.facebook.com using cookies collected on the victim’s machine” to extract financial details such as daily ad spending limits and total campaign budgets.
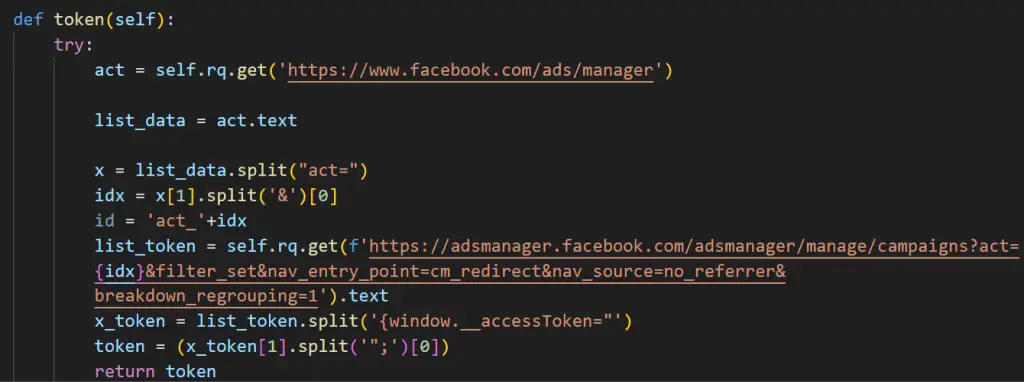
Routine to collect Facebook Ads Manager token | Image: Netskope
Netskope researchers suggest the intent behind targeting Ads Manager is to weaponize stolen accounts for malicious advertising campaigns. These could potentially include fraudulent promotions or malvertisements designed to spread further malware.
Beyond its focus on Facebook accounts, NodeStealer now steals credit card information. The malware copies the “Web Data” SQLite database from browsers, extracting cardholder names, expiration dates, and numbers. Using Python’s SQLite3 library, it queries stored payment data, a capability that significantly broadens its threat scope.
NodeStealer’s new variants employ various advanced techniques:
- Windows Restart Manager: The malware uses this tool to unlock browser database files, stopping processes that might otherwise block access. “Using LOLBins like Windows Restart Manager helps attackers evade detection by leveraging Microsoft-signed binaries,” the report states.
- Persistence via Registry Keys: Shifting from startup folders to run registry keys, the malware now uses PowerShell to execute its Python script automatically on system startup.
- Junk Code and Batch Files: Variants feature massive amounts of junk code to evade detection, with some using batch files to dynamically generate and execute the malicious script
True to its roots, NodeStealer uses Telegram for data exfiltration. Stolen credentials, along with the victim’s IP address, hostname, and country, are zipped and sent to the attacker, maintaining its stealthy operations.
Interestingly, NodeStealer avoids victims in Vietnam, the likely home country of its operators. The script checks the victim’s IP-based location using ipinfo and exits if the country code is “VN.” This tactic minimizes the risk of local legal repercussions and detection by regional law enforcement.
As Alcantara notes, these new techniques “help defenders adjust their controls to detect, prevent and hunt Python NodeStealer on their environment.” With attackers continually refining their strategies, vigilance, and adaptability remain crucial in the fight against cybercrime.





