Python Taint v0.42 released: Static Analysis Tool for Detecting Security Vulnerabilities
Python Taint
Static analysis of Python web applications based on theoretical foundations (Control flow graphs, fixed point, data flow analysis)
This report presents the static analysis too PyT which has been created to detect security vulnerabilities in Python web applications, in particular applications, built in the framework Flask.
The tool utilizes the monotone framework for the analysis. An AST is built by the builtin AST library, and a CFG is built from the AST. The resulting CFG is then processed so Flask specific features are taken into account. A modified version of the reaching definitions algorithm is now run by the fixed-point algorithm to aid the finding of vulnerabilities. Vulnerabilities are detected based on a definition file containing ’trigger words’. A trigger word is a word that indicates where the flow of the program can be dangerous. The detected vulnerabilities are in the end reported to the developer.
PyT has been created with flexibility in mind. The analysis can be either changed or extended so the performance of PyT can be improved upon. Also, the Flask specific processing can be changed so other frameworks can be analyzed without major changes to PyT. In order to test the abilities of PyT, a number of vulnerable applications were manufactured and PyT was evaluated with these. All the manufactured examples were correctly identified as being vulnerable by PyT.
To test PyT in a more realistic setting it was also run on 7 open source projects. Here no vulnerabilities were found. One of the projects was so big that PyT spent very long on the analysis and was therefore terminated.
Features
- Detect Command injection
- Detect SQL injection
- Detect XSS
- Detect directory traversal
- Get a control flow graph
- Get a def-use and/or a use-def chain
- Search GitHub and analyze hits with PyT
- Scan intraprocedural or interprocedural
- A lot of customization possible
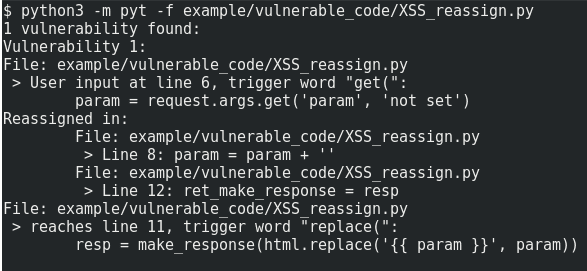
Example usage and output:
Changelog v0.42
November 1st, 2018
💥 Breaking Changes
- Changed trigger file format when specifying specific tainted args ([#182])
🎉 New Features
- Function calls such as
list.appendanddict.updatenow propagate taint to the list or dict ([#181])
🐛 Bugfixes
- IfExp (or ternary) expression handling improved ([#179])
Install
Usage from Source
Tutorial
Copyright (C) 2016 KevinHock





