Python’s New Threat: Malicious PyPI Packages Targeting Linux Devices
The Python community has recently faced a new threat: three new malicious PyPI (Python Package Index) packages that deploy CoinMiner on Linux devices. These packages, identified as `modularseven-1.0`, `driftme-1.0`, and `catme-1.0`, have been discovered by FortiGuard’s AI-driven OSS malware detection system, marking a significant escalation in the sophistication of attacks targeting the open-source ecosystem.
At first glance, these packages seem harmless. However, upon initial use, they deploy a CoinMiner executable on Linux devices. This method is strikingly similar to the “culturestreak” PyPI package discovered earlier, suggesting a pattern of increasingly complex attacks in the Python package ecosystem.
The attack methodology of these packages is meticulously planned. For instance, the `driftme-1.0` package, used as an illustrative example, showcases the multi-staged nature of these attacks. The malicious payload is concealed and released incrementally, making detection challenging. The first stage involves decoding a string into a shell command, which fetches content from a remote URL using curl and executes it via the Bash shell. This script, named `unmi.sh`, contains the second stage of the payload.

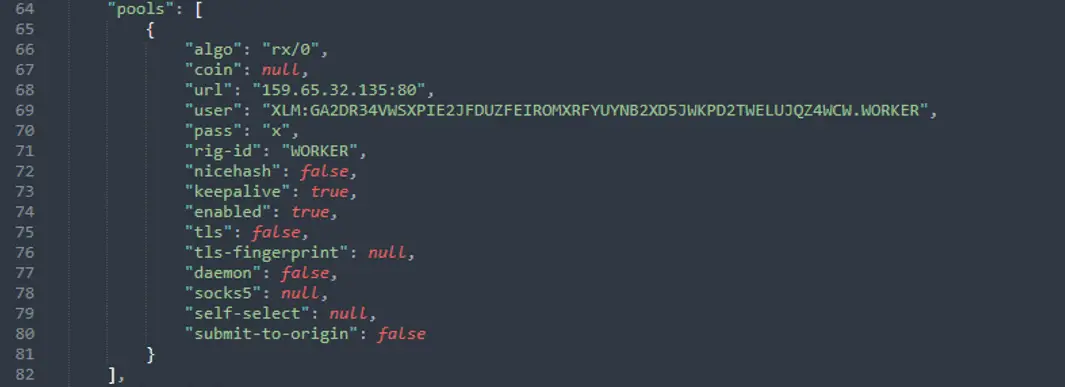
Settings for mining pools | Image: FortiGuard
The `unmi.sh` script plays a crucial role in setting up the CoinMiner executable. It downloads a configuration file, `config.json`, and the CoinMiner executable itself from remote locations. The configuration file outlines the cryptocurrency mining settings, including the mining algorithm, device resource settings, and designated mining pools. The executable is then run in the background, ensuring its persistence and reactivation with every new Bash shell session.
These packages demonstrate enhanced strategies in evading detection compared to “culturestreak.” They introduce an extra stage where crucial commands are stored in the `unmi.sh` file on a remote server. This approach minimizes the code within the PyPI package and allows for controlled disclosure of the malicious code, improving the chances of evading security solutions.
The inclusion of malicious commands in the `~/.bashrc` file ensures the malware’s persistence and reactivation on the user’s device, extending the duration of its covert operation. This strategy highlights the malware’s ability to exploit the user’s device stealthily for prolonged periods.
This recent discovery underscores the continuous evolution of malicious strategies and the importance of vigilance in the Python community. It serves as a reminder of the critical need to scrutinize code and packages from unverified sources and to stay informed about potential threats.