Qilin Ransomware: Beyond Encryption, a New Threat of Credential Theft

The Qilin ransomware group, already infamous for its “double extortion” tactics, has now added a new strategy to its repertoire: credential harvesting from Google Chrome browsers. A recent investigation by the Sophos X-Ops team revealed that during a Qilin ransomware breach in July 2024, attackers employed a novel approach to steal credentials stored in Chrome, exacerbating the chaos typically associated with ransomware attacks.
Qilin has been on the radar of cybersecurity professionals for over two years, with its most notable attack in June 2024 targeting Synnovis, a UK governmental service provider linked to various healthcare institutions. Traditionally, Qilin has relied on “double extortion,” where they steal a victim’s data, encrypt their systems, and then demand ransom for both the decryption key and to prevent the release or sale of the stolen data. However, the group’s latest activity indicates a shift in tactics, focusing not just on the victim’s network but also on individual user credentials stored within Chrome browsers.
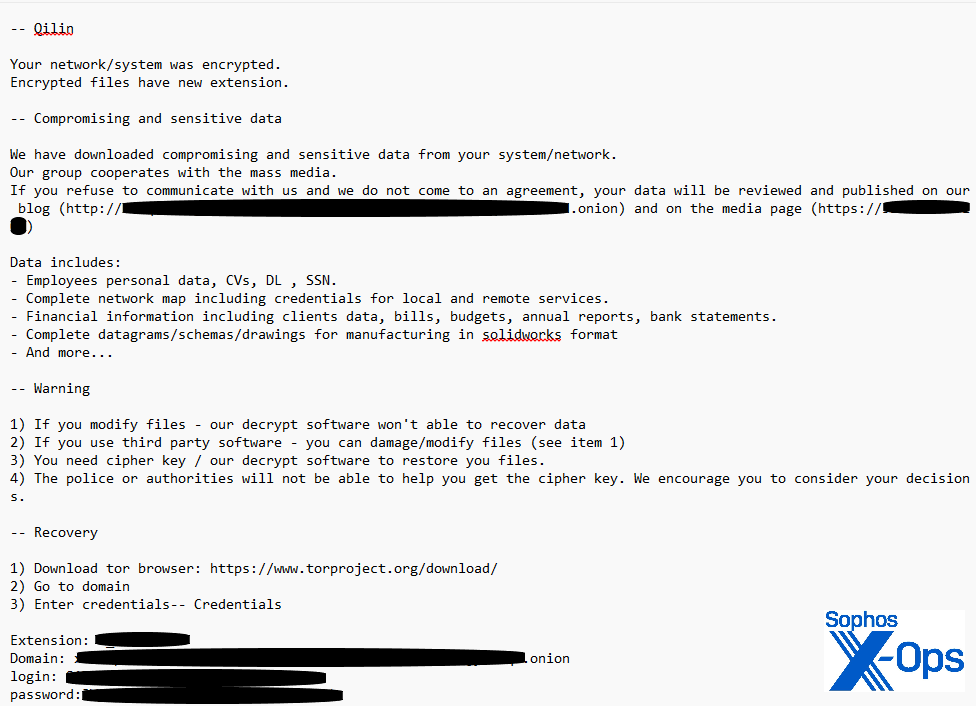
A Qilin ransom note
The breach investigated by Sophos X-Ops began with the attackers gaining access to the target network through compromised credentials, a common entry method for Qilin and other ransomware groups. The initial access was achieved via a VPN portal that lacked multi-factor authentication (MFA) protection. Once inside, the attackers exhibited patience, with an 18-day dwell time between the initial access and their next move, suggesting the possible involvement of an Initial Access Broker (IAB).
The attackers’ next move was lateral movement within the network, eventually reaching a domain controller. Here, they modified the default domain policy by introducing a logon-based Group Policy Object (GPO) designed to harvest credentials. This GPO deployed a PowerShell script, IPScanner.ps1, that specifically targeted credential data stored in Chrome browsers.
Whenever a user logged on to an endpoint connected to the infected domain, the GPO-triggered script would execute, creating files containing the harvested credentials. These files were then written back to a newly created directory on the domain’s SYSVOL share, cleverly named after the hostname of the compromised device. This approach ensured that the attackers could silently and efficiently collect a wealth of credential data without raising immediate suspicion.
The choice of Chrome as the target for this credential theft was far from arbitrary. With over 65% of the browser market share, Chrome is statistically the most likely source of valuable credentials, both personal and work-related. The attackers likely capitalized on the fact that the average user stores a significant number of passwords in their browser, potentially giving Qilin access to credentials for dozens, if not hundreds, of third-party sites.
Interestingly, while multiple domain controllers within the same Active Directory domain were infected and encrypted by the ransomware, the domain controller where the credential-harvesting GPO was deployed was left untouched.
Organizations and individuals alike need to remain vigilant, adopting robust security measures such as multi-factor authentication and regular password updates. It’s also crucial to educate users about the risks of storing sensitive information within browsers and to encourage the use of password managers.
Related Posts:
- Qilin Ransomware Group’s Latest Victims: From Schools to Municipalities
- WordPress Tackles PHP and RCE Flaws in Security Update
- Trojan Malware Infiltrates Browser Extensions, Impacts 300,000 Users
- Zero-Day Vulnerability: 18 Years of Exploiting the ‘0.0.0.0’ Flaw
- New Chrome and Firefox malicious extensions prevent user removal to hijack browsers





