Image: Sekoia
In a recent report from Sekoia TDR, the Quad7 botnet operators—already known for leveraging compromised routers to relay attacks—are demonstrating an evolving arsenal of techniques and tools aimed at staying ahead of detection efforts. The report reveals that the group is actively developing new tools and techniques to evade detection and expand its reach, posing a growing threat to organizations and individuals worldwide.
The Quad7 botnet, also referred to as the “7777 botnet,” has been a thorn in the side of cybersecurity professionals for some time. This botnet predominantly compromises TP-Link routers, exposing them via open TELNET/7777 and Socks5 proxy ports. These compromised devices serve as conduits for brute-force attacks against Microsoft 365 accounts. The Quad7 operators use password-protected bind shells to secure their control, ensuring that any attacker who gains access can execute commands with root privileges.
However, Quad7 is not the only botnet in the operators’ toolkit. The alogin botnet—a network of compromised Asus routers—is another formidable weapon, exploiting open TELNET/63256 ports to relay attacks against VPNs, telnet, and SSH services. The operators’ ability to use both Quad7 and alogin botnets to relay attacks on critical infrastructure demonstrates their determination to remain a key player in the threat landscape.
While these botnets have been active for some time, recent findings reveal a shift in tactics by the Quad7 operators. According to Sekoia TDR, the operators are developing HTTP-based reverse shells as part of their next wave of attacks. These reverse shells, named UPDTAE backdoors (due to a typo in the code), are currently being tested on compromised routers. This move away from traditional open SOCKS proxies signifies a strategic shift to stealthier methods of control and communication, making it more difficult for security researchers to track the botnet’s operations.
Unlike their previous infrastructure, which was plagued by poor design choices like hardcoded passwords, the new HTTP reverse shells use JSON POST requests for communication, adding an additional layer of complexity to the malware’s operation. By moving away from traditional login interfaces, the Quad7 operators are not only increasing their operational security but also preventing other threat actors from hijacking their infrastructure.
The Sekoia TDR team’s continued monitoring of the Quad7 operators has uncovered new botnet clusters that indicate broader expansion. In addition to alogin and xlogin, other *login botnets—such as rlogin, axlogin, and zylogin—have surfaced, each targeting specific network devices. For example:
- rlogin focuses on Ruckus Wireless devices, with a smaller botnet of around 213 compromised devices as of August 2024.
- zylogin targets Zyxel VPN appliances, though it remains a much smaller operation.
The introduction of these new botnets suggests that the Quad7 operators are expanding their reach, targeting a broader range of devices in the hopes of increasing their attack surface.
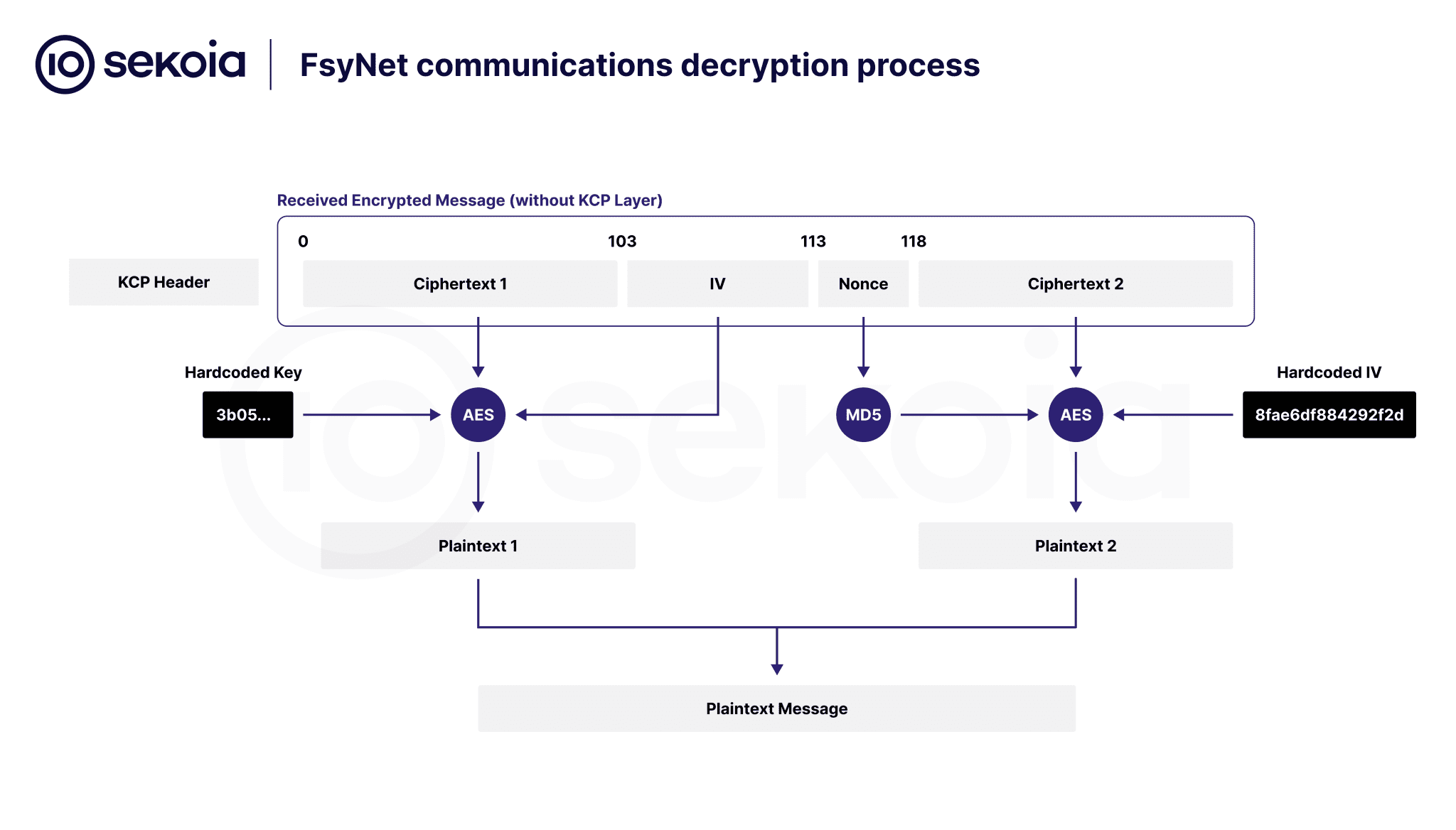
Another notable discovery in the report is the emergence of FsyNet, a project that further underscores the sophistication of the Quad7 operators. FsyNet leverages the KCP protocol, a low-latency alternative to TCP, to create encrypted communication channels between compromised devices and the attackers’ command-and-control servers.
The FsyNet project employs firewall manipulation scripts and a series of C++ binaries to launch its attack infrastructure, allowing the operators to tunnel communications through devices without relying on the more detectable SOCKS proxies of the past. This layered approach to securing communications marks a significant upgrade in the Quad7 operators’ methods, making their botnet more resilient to takedown attempts.
As the report from Sekoia TDR shows, their botnet infrastructure is evolving to become stealthier, harder to detect, and more secure. With the introduction of HTTP reverse shells, a shift away from open SOCKS proxies, and the creation of sophisticated new projects like FsyNet, it’s clear that the Quad7 operators are gearing up for larger, more evasive campaigns.
For a more in-depth analysis, you can review the full report from Sekoia TDR here.
Related Posts:
- Researchers Uncover Massive Quad7 Botnet Targeting Microsoft 365
- France Leads International Effort to Eradicate PlugX Trojan from 3,000 Systems
- Cybercriminals have been earned over $16 million by distributing ransomware for 2 years
- Linux Kernel 6.9 Reaches End of Life, Users Urged to Upgrade for Continued Security