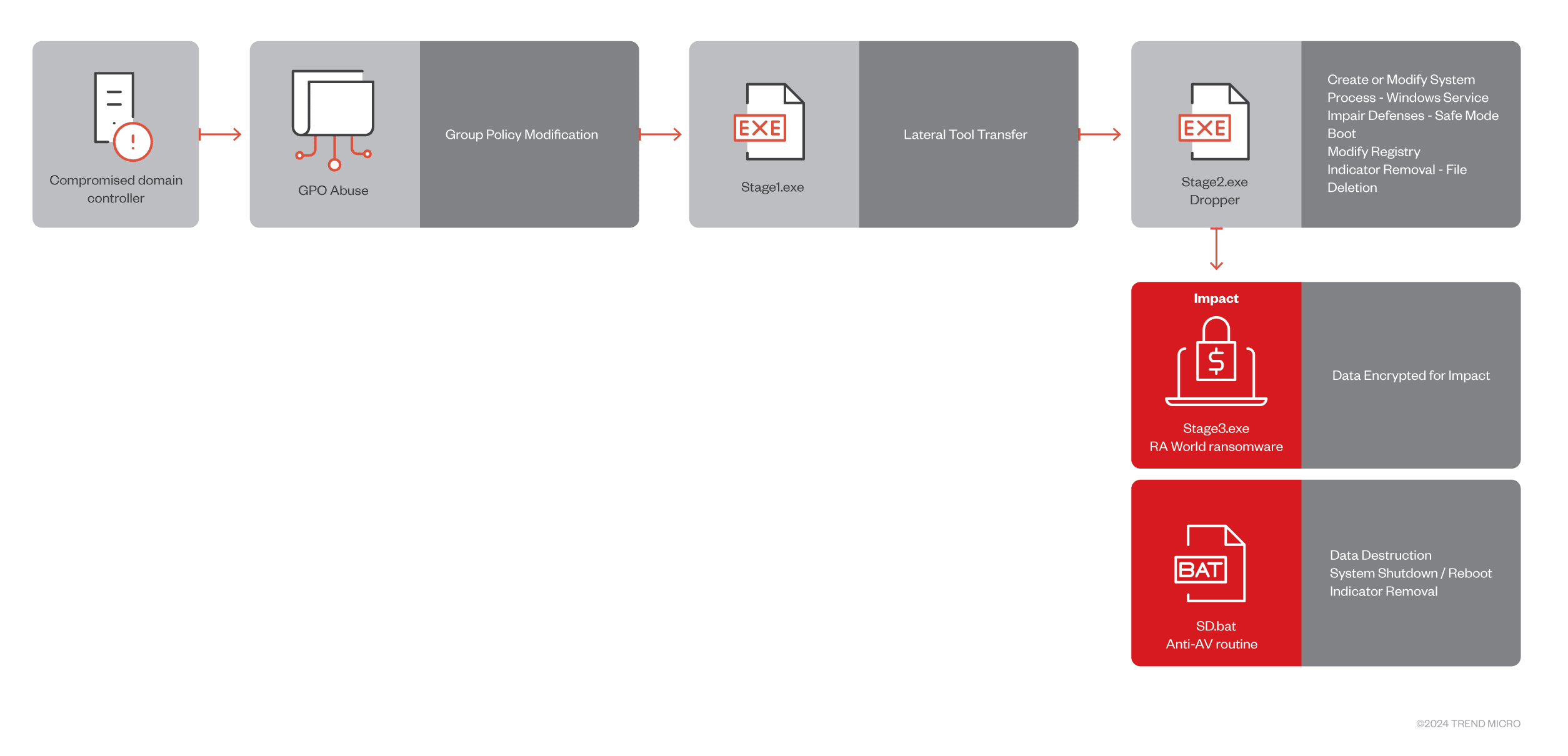
The RA World attack chain
When the Babuk ransomware group disbanded in 2021, it seemed like a minor victory in the ongoing battle against cybercrime. However, the leak of Babuk’s source code has become a breeding ground for new ransomware strains, one of the most dangerous being RA World (formerly RA Group). Since its emergence in April 2023, RA World has shown a disconcerting focus on breaching organizations worldwide, with significant attacks in the US, Germany, India, and Taiwan, particularly targeting the healthcare and finance sectors.
A Targeted, Multi-Stage Attack
The Trend Micro threat hunting team uncovered a recent RA World campaign against Latin American healthcare organizations. This attack reveals the group’s sophisticated, multi-stage tactics:

- The Foothold: RA World often starts by compromising domain controllers. This grants them the access needed to deploy their malicious components through machine Group Policy Objects (GPOs), a technique that allows broad changes across a network.
- Elevating Privileges: The presence of PowerShell scripts and indications of potential GPO tampering suggest a strategy of privilege escalation. This allows the ransomware to gain greater control and execute its payloads unhindered across the compromised domain.
- Targeted Movement: Interestingly, the payloads contain hardcoded domain information and check for machine names. This shows RA World’s attacks aren’t random; they focus their efforts on specific victims. Additionally, the presence of files like Finish.exe and Exclude.exe reveals strategic choices – either marking previous compromises or ‘no-go’ zones within the network.
- Establishing Persistence: To maintain its grip on infected systems, RA World creates a malicious service (MSOfficeRunOncelsls) designed to run in Safe Mode with Networking. Further, they cleverly modify the Boot Configuration Data (BCD) to force an automatic reboot into Safe Mode – this can cripple system recovery and keep the ransomware in control.
- Evading Detection: Like many advanced ransomware strains, RA World tries to disable security solutions. Analysts identified specific attempts to delete Trend Micro folders and use the WMIC utility to gather information on disks. After encryption, it removes its safe mode boot option and tries to cover its tracks.
- The Final Blow: The leaked Babuk code provides the core structure for RA World’s final execution. The ransomware encrypts critical data and drops ransom notes that publicly name recent victims who didn’t pay. This pressure tactic is designed to coerce organizations into paying the ransom.
Anti-AV Measures
RA World employs anti-detection techniques, including:
- Specific deletion of Trend Micro folders
- Use of the WMIC utility for disk information gathering
- Removal of safe mode boot options
- Forced reboots
RA World Origins and Insights
The Babuk source code leak has lowered the barrier to entry for ransomware groups. RA World’s attacks on healthcare highlight the targeting of specific organizations within vulnerable sectors.
Protect Your Organization: Recommendations
To defend against RA World and other ransomware strains, organizations should:
- Limit administrative access rights
- Keep security solutions and systems updated
- Maintain robust data backups
- Exercise extreme email and web caution
- Train staff in social engineering awareness
- Implement layered security at all network points