
Sample Ransom Note
On August 1st, India experienced a massive disruption in its banking payment systems due to a ransomware attack on C-Edge Technologies, a service provider for several banks. The Juniper Networks team provided a detailed analysis of the breach in their report.
C-Edge Technologies was exposed due to a misconfigured Jenkins server. This server became the initial point of attack, allowing the attackers to gain unauthorized access to the company’s systems and deploy the ransomware. The attack was carried out by the RansomEXX group, which has a long history of targeting businesses, government agencies, and banking organizations worldwide.
The vulnerability exploited in the attack, CVE-2024-23897 (CVSS score: 9.8), enables an unauthenticated attacker to read arbitrary files on the Jenkins controller’s file system and execute malicious code.
With extensive knowledge of Jenkins vulnerabilities, many security researchers replicated specific attack scenarios and created working proof-of-concept exploits for the mentioned vulnerability, publishing them on GitHub.
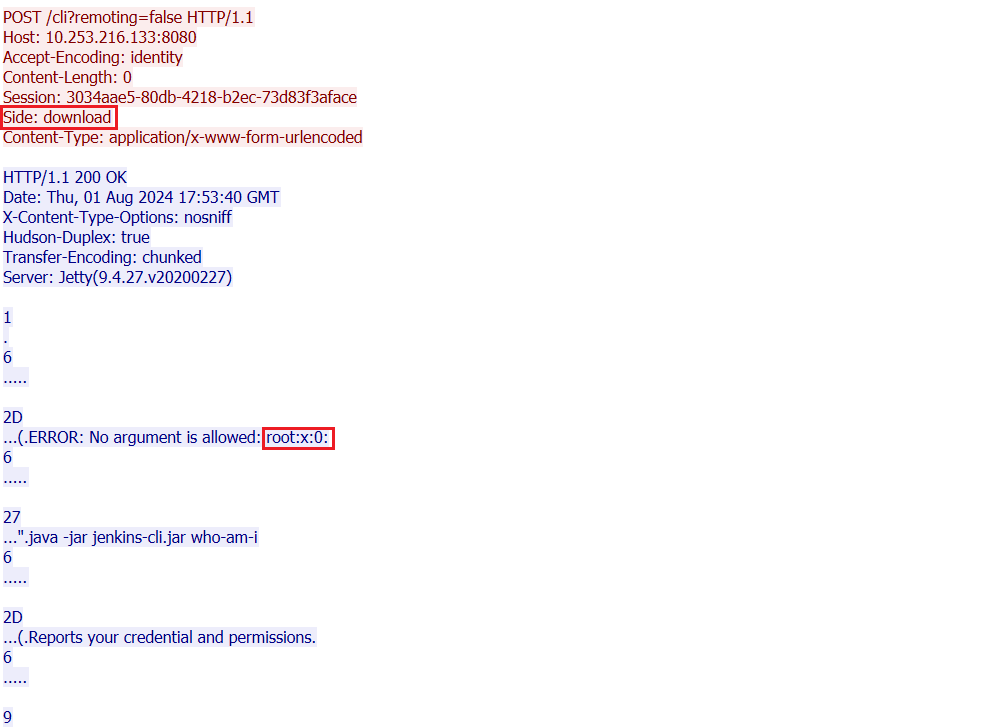
The attack began with the hackers sending a POST request to the Jenkins server, attempting to execute a malicious command. The server processed the request, granting the attackers access to sensitive information, including user data. It was later revealed that the issue stemmed from a software component of the server that incorrectly handled such requests, allowing the cybercriminals to bypass security measures and gain access to server commands. Subsequent command execution and output retrieval through Jenkins were performed using the network analysis tool Wireshark.
Juniper Networks experts emphasized that the attack on C-Edge Technologies highlights the importance of regular updates and patches for all software solutions in use. In this case, the Jenkins vulnerability could have been prevented through timely updates and proper server configuration. The incident also demonstrates the need for strict configuration management, especially for critical systems like Jenkins servers.
Furthermore, the incident underscores the necessity of adopting a Zero Trust model, which assumes that no device or user should be trusted by default. Continuous verification of all operations and users is key to protecting against such threats.