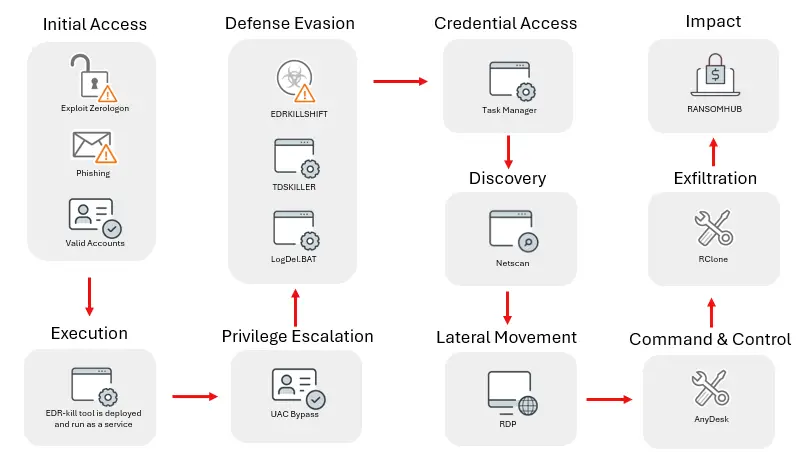
The infection chain of the RansomHub utilizing EDRKillShifter | Image: Trend Micro
In a recently uncovered report by Trend Micro, the notorious RansomHub ransomware group has been found to leverage a powerful new tool, EDRKillShifter, to disable endpoint detection and response (EDR) solutions and antivirus protections, allowing them to evade detection and wreak havoc on compromised systems.
RansomHub has already made a name for itself through its affiliate model, enabling cybercriminals to employ sophisticated techniques to prolong their presence in infected networks. What sets this ransomware apart is its ability to bypass traditional security measures through the integration of EDRKillShifter, a tool designed to undermine EDR solutions and render security monitoring ineffective.
EDRKillShifter exploits vulnerable drivers within a system, exploiting weaknesses to terminate EDR and antivirus software. This allows the ransomware to remain undetected, persist in compromised environments, and continually disrupt security operations. The tool dynamically adjusts its evasion techniques in real-time, adapting to evolving detection capabilities.
Once deployed, EDRKillShifter is fully integrated into the ransomware’s attack chain, providing RansomHub with the capability to disable security measures at every stage of an attack. From initial access to data exfiltration, EDRKillShifter ensures that attackers maintain control over the system, outsmarting traditional endpoint security.
Over the past several months, RansomHub has successfully targeted over 210 organizations across multiple sectors, including critical infrastructure such as IT, healthcare, government services, and financial services. The FBI’s recent advisory in August confirmed the extent of RansomHub’s impact, shedding light on the group’s far-reaching ransomware campaigns.
RansomHub typically gains access to systems through phishing emails, exploiting known vulnerabilities, and password-spraying attacks. In a notable incident analyzed by Trend Micro, a single compromised user account facilitated most of the malicious activities. The attackers also exploited the Zerologon vulnerability (CVE-2020-1472) as another potential access vector.
Once inside a network, RansomHub employs a series of batch script files—named “232.bat,” “tdsskiller.bat,” “killdeff.bat,” and “LogDel.bat”—to disable security mechanisms such as Windows Defender. These scripts alter system settings, terminate processes, and tamper with event logs to cover the attackers’ tracks.
RansomHub escalates its attacks by dumping credentials from the Local Security Authority Subsystem Service (LSASS), granting access to sensitive credentials that further deepen the breach. With tools like NetScan and AnyDesk, the attackers map the network, allowing them to move laterally across systems, deploying ransomware and exfiltrating data.
RansomHub utilizes command-line tools such as “rclone” to exfiltrate valuable files to remote locations, leveraging these stolen files as bargaining chips in their ransom demands.
The integration of EDRKillShifter into RansomHub’s arsenal marks a significant escalation in the capabilities of modern ransomware. The tool’s ability to disable security defenses with surgical precision makes it a formidable threat to organizations relying solely on traditional endpoint protection measures.
As ransomware groups increasingly adopt similar tools to evade detection, the cybersecurity community must prioritize adaptive, multilayered defense strategies. Organizations need to incorporate proactive threat intelligence and advanced detection mechanisms that go beyond conventional security tools to safeguard their digital assets.
Related Posts:
- EDRKillShifter: A New EDR-Killing Tool in Ransomware Attack
- RansomHub: A New Ransomware-as-a-Service Threatens Multiple Operating Systems
- Ransomhub’s SCADA Hack: A Wake-Up Call for Industrial Cybersecurity
- Zerologon Vulnerability Strikes Again: RansomHub Exploits Legacy Flaw
- Unveiling RansomHub Ransomware: New Infection Chains and Rising Threats